Source: thehackernews.com – Author: . May 21, 2023Ravie LakshmananSoftware Security / Malware The maintainers of Python Package Index (PyPI), the official third-party software repository for the...
Day: May 29, 2023
Meet ‘Jack’ from Romania! Mastermind Behind Golden Chickens Malware – Source:thehackernews.com
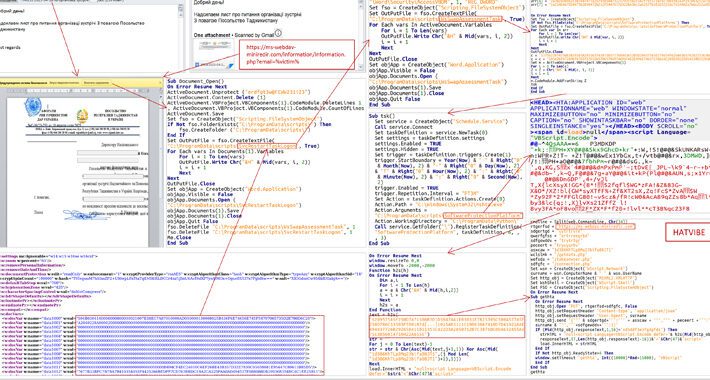
Source: thehackernews.com – Author: . The identity of the second threat actor behind the Golden Chickens malware has been uncovered courtesy of a “fatal” operational security...
Notorious Cyber Gang FIN7 Returns With Cl0p Ransomware in New Wave of Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . May 20, 2023Ravie LakshmananCyber Crime / Ransomware The notorious cybercrime group known as FIN7 has been observed deploying Cl0p (aka Clop)...
Warning: Samsung Devices Under Attack! New Security Flaw Exposed – Source:thehackernews.com
Source: thehackernews.com – Author: . May 20, 2023Ravie LakshmananMobile Security / Cyber Attack The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has warned of active exploitation...
Privacy Sandbox Initiative: Google to Phase Out Third-Party Cookies Starting 2024 – Source:thehackernews.com
Source: thehackernews.com – Author: . May 19, 2023Ravie LakshmananOnline Privacy / Tech News Google has announced plans to officially flip the switch on its twice-delayed Privacy...
Dr. Active Directory vs. Mr. Exposed Attack Surface: Who’ll Win This Fight? – Source:thehackernews.com
Source: thehackernews.com – Author: . Active Directory (AD) is among the oldest pieces of software still used in the production environment and can be found in...
Threat Intelligence & Dark web Monitoring Tools
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
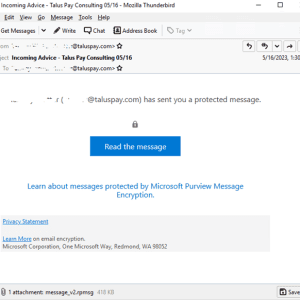
Attackers use encrypted RPMSG messages in Microsoft 365 targeted phishing attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of phishing attacks that are combining the use of compromised Microsoft 365 accounts and .rpmsg encrypted emails. Trustwave...
Industrial automation giant ABB disclosed data breach after ransomware attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Swiss electrification and automation technology giant ABB confirmed it has suffered a data breach after a ransomware attack. ABB has...
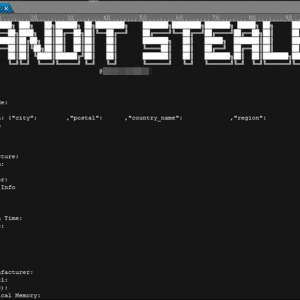
New Bandit Stealer targets web browsers and cryptocurrency wallets – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Bandit Stealer is a new stealthy information stealer malware that targets numerous web browsers and cryptocurrency wallets. Trend Micro researchers...
Clever ‘File Archiver In The Browser’ phishing trick uses ZIP domains – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams A new ‘File Archivers in the Browser’ phishing kit abuses ZIP domains by displaying fake WinRAR or Windows File Explorer...
PyPI announces mandatory use of 2FA for all software publishers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Python Package Index (PyPI) has announced that it will require every account that manages a project on the platform...
Iranian Agrius Hackers Targeting Israeli Organizations with Moneybird Ransomware – Source:thehackernews.com
Source: thehackernews.com – Author: . May 25, 2023Ravie LakshmananRansomware / Endpoint Security The Iranian threat actor known as Agrius is leveraging a new ransomware strain called...
GUAC 0.1 Beta: Google’s Breakthrough Framework for Secure Software Supply Chains – Source:thehackernews.com
Source: thehackernews.com – Author: . May 25, 2023Ravie LakshmananSoftware Security / Supply Chain Google on Wednesday announced the 0.1 Beta version of GUAC (short for Graph...
Iranian Tortoiseshell Hackers Targeting Israeli Logistics Industry – Source:thehackernews.com
Source: thehackernews.com – Author: . May 24, 2023Ravie LakshmananCyber Threat / Web Security At least eight websites associated with shipping, logistics, and financial services companies in...
What to Look for When Selecting a Static Application Security Testing (SAST) Solution – Source:thehackernews.com
Source: thehackernews.com – Author: . If you’re involved in securing the applications your organization develops, there is no question that Static Application Security Testing (SAST) solutions...
Data Stealing Malware Discovered in Popular Android Screen Recorder App – Source:thehackernews.com
Source: thehackernews.com – Author: . May 24, 2023Ravie LakshmananMobile Security / Data Safety Google has removed a screen recording app named “iRecorder – Screen Recorder” from...
Legion Malware Upgraded to Target SSH Servers and AWS Credentials – Source:thehackernews.com
Source: thehackernews.com – Author: . May 24, 2023Ravie LakshmananServer Security / Malware An updated version of the commodity malware called Legion comes with expanded features to...
N. Korean Lazarus Group Targets Microsoft IIS Servers to Deploy Espionage Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . May 24, 2023Ravie LakshmananCyber Espionage / Server Security The infamous Lazarus Group actor has been targeting vulnerable versions of Microsoft Internet...
Cyber Attacks Strike Ukraine’s State Bodies in Espionage Operation – Source:thehackernews.com
Source: thehackernews.com – Author: . May 24, 2023Ravie LakshmananCyber War / Threat Intel The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of cyber attacks...
GoldenJackal: New Threat Group Targeting Middle Eastern and South Asian Governments – Source:thehackernews.com
Source: thehackernews.com – Author: . May 23, 2023Ravie LakshmananCyber Threat / APT Government and diplomatic entities in the Middle East and South Asia are the target...
North Korean Kimsuky Hackers Strike Again with Advanced Reconnaissance Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . May 23, 2023Ravie LakshmananCyber Threat / Malware The North Korean advanced persistent threat (APT) group known as Kimsuky has been observed...
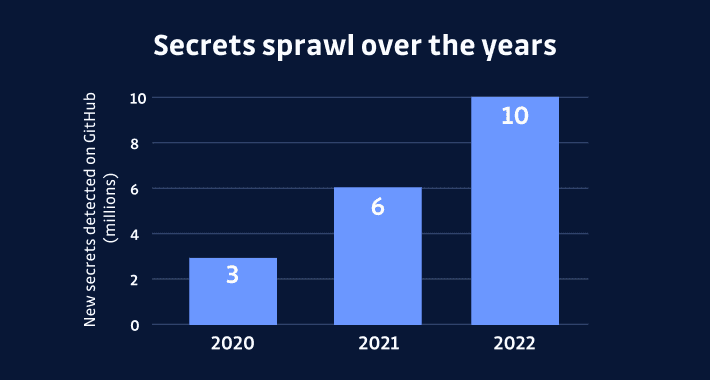
The Rising Threat of Secrets Sprawl and the Need for Action – Source:thehackernews.com
Source: thehackernews.com – Author: . The most precious asset in today’s information age is the secret safeguarded under lock and key. Regrettably, maintaining secrets has become...
New WinTapix.sys Malware Engages in Multi-Stage Attack Across Middle East – Source:thehackernews.com
Source: thehackernews.com – Author: . May 23, 2023Ravie LakshmananEndpoint Security/ Malware An unknown threat actor has been observed leveraging a malicious Windows kernel driver in attacks...
China Bans U.S. Chip Giant Micron, Citing “Serious Cybersecurity Problems” – Source:thehackernews.com
Source: thehackernews.com – Author: . May 23, 2023Ravie LakshmananNational Security / Hardware China has banned U.S. chip maker Micron from selling its products to Chinese companies...
E.U. Regulators Hit Meta with Record $1.3 Billion Fine for Data Transfer Violations – Source:thehackernews.com
Source: thehackernews.com – Author: . May 22, 2023Ravie LakshmananData Protection / Privacy Facebook’s parent company Meta has been fined a record $1.3 billion by European Union...
Indonesian Cybercriminals Exploit AWS for Profitable Crypto Mining Operations – Source:thehackernews.com
Source: thehackernews.com – Author: . May 22, 2023Ravie LakshmananCryptocurrency / Cloud Security A financially motivated threat actor of Indonesian origin has been observed leveraging Amazon Web...