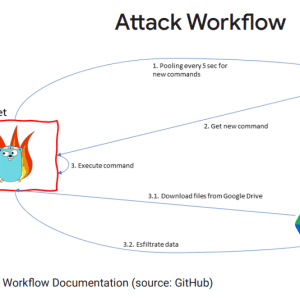
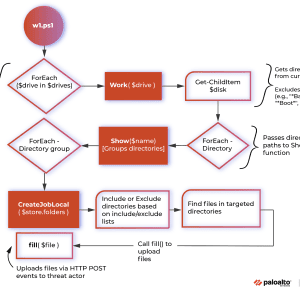
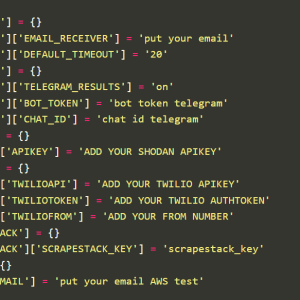
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Day: April 17, 2023
Montana Becomes First US State to Pass TikTok Ban
The state of Montana in the US has become the first to pass legislation banning TikTok on personal devices. The bill, SB 419, passed by a vote...
Ransomware Attack Hits Payments Giant NCR’s Datacenter
US payments giant NCR has been hit by a ransomware attack that targeted one of its data centers in Aloha, Hawaii. The company unveiled the breach...
Qbot Banking Trojan Increasingly Delivered Via Business Emails
A malicious spam-email campaign has been observed increasingly spreading banking Trojans from the QBot (or Qakbot) family using fake business emails. Discovered by security researchers at...
Friendly Hacker, Keren Elazari, to Announced as Keynote Speaker at Infosecurity Europe 2023
Acclaimed security analyst, author and TED speaker, Keren Elazari, has today been announced as the latest keynote speaker at Infosecurity Europe, the most influential information security event running...
The State of Cloud Native Security Report 2023 by Paloalto Networks
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
How to Protect Your Ecommerce Site from Cybersecurity Threats
By Karl Pulanco, Product Portfolio Manager, Yondu Modern businesses no longer need a physical store to sell goods and services. All they need now is an...
China-linked APT41 group spotted using open-source red teaming tool GC2 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. China-linked APT41 group used the open-source red teaming tool GC2 in an attack against a Taiwanese media organization. Google Threat...
Vice Society gang is using a custom PowerShell tool for data exfiltration – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Vice Society ransomware operators have been spotted using a PowerShell tool to exfiltrate data from compromised networks. Palo Alto Unit...
Experts warn of an emerging Python-based credential harvester named Legion – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Legion is an emerging Python-based credential harvester and hacking tool that allows operators to break into various online services. Cado...
Experts found the first LockBit encryptor that targets macOS systems – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Researchers warn that the LockBit ransomware gang has developed encryptors to target macOS devices. The LockBit group is the first...
LockBit Ransomware Tests Taking a Bite Out of Apple Users – Source: www.databreachtoday.com – Author: 1.
Source: www.databreachtoday.com – Author: 1. Cybercrime , Cybercrime as-a-service , Endpoint Security Don’t Panic: Apparent macOS Beta Testing is Highly Buggy, Poses No Immediate Threat Mathew...
GUEST ESSAY: The Top 10 cybersecurity shortfalls that put SMBs, enterprises at elevated risk
By Harman Singh No organization is immune to cybersecurity threats. Even the most well-protected companies can be susceptible to attacks if they are not careful about...
Payments Giant NCR Hit by Ransomware – Source: www.securityweek.com – Author: Eduard Kovacs –
Source: www.securityweek.com – Author: Eduard Kovacs. Category & Tags: Ransomware,Featured,ransomware – Ransomware,Featured,ransomware US payments giant NCR confirmed over the weekend that a data center outage is...
Mobb Raises $5.4 Million in Seed Funding for Automatic Vulnerability Fixing Tool – Source: www.securityweek.com – Author: Eduard Kovacs –
Source: www.securityweek.com – Author: Eduard Kovacs. Category & Tags: Application Security,Cybersecurity Funding,Funding/M&A,funding – Application Security,Cybersecurity Funding,Funding/M&A,funding Boston, MA-based Mobb on Monday announced raising $5.4 million in...
Online Gaming Chats Have Long Been Spy Risk for US Military – Source: www.securityweek.com – Author: Associated Press –
Source: www.securityweek.com – Author: Associated Press. Category & Tags: Data Protection – Data Protection Step into a U.S. military recreation hall at a base almost anywhere...
Google Warns of New Chrome Zero-Day Attack – Source: www.securityweek.com – Author: Ryan Naraine –
Source: www.securityweek.com – Author: Ryan Naraine. Category & Tags: Vulnerabilities,Featured,Google Chrome,vulnerability,Zero-Day – Vulnerabilities,Featured,Google Chrome,vulnerability,Zero-Day Another day, another zero-day attack hitting widely deployed software from a big...
FBI Arrests 21-Year-Old Guardsman in Leak of Classified Military Documents – Source: www.securityweek.com – Author: Associated Press –
Source: www.securityweek.com – Author: Associated Press. Category & Tags: Data Breaches,arrested,data leak – Data Breaches,arrested,data leak A Massachusetts Air National Guard member was arrested Thursday in...
CISA Introduces Secure-by-design and Secure-by-default Development Principles – Source: www.securityweek.com – Author: Kevin Townsend –
Source: www.securityweek.com – Author: Kevin Townsend. Category & Tags: Government,IoT Security,Supply Chain Security,Vulnerabilities,CISA,Featured – Government,IoT Security,Supply Chain Security,Vulnerabilities,CISA,Featured CISA has described and published a set of...
Microsoft Warns Accounting, Tax Return Preparation Firms of Remcos RAT Attacks – Source: www.securityweek.com – Author: Ionut Arghire –
Source: www.securityweek.com – Author: Ionut Arghire. Category & Tags: Malware & Threats,malware – Malware & Threats,malware Microsoft is warning of a new Remcos remote access trojan...
Google, CISA Warn of Android Flaw After Reports of Chinese App Zero-Day Exploitation – Source: www.securityweek.com – Author: Eduard Kovacs –
Source: www.securityweek.com – Author: Eduard Kovacs. Category & Tags: Mobile & Wireless,Vulnerabilities,Android,Featured – Mobile & Wireless,Vulnerabilities,Android,Featured An Android vulnerability that was reportedly exploited as a zero-day...
Juniper Networks Patches Critical Third-Party Component Vulnerabilities – Source: www.securityweek.com – Author: Ionut Arghire –
Source: www.securityweek.com – Author: Ionut Arghire. Category & Tags: Vulnerabilities,Juniper,vulnerability – Vulnerabilities,Juniper,vulnerability Networking, cloud and cybersecurity solutions provider Juniper Networks this week published advisories detailing tens...
Cerbos Raises $7.5 Million for Authorization Platform – Source: www.securityweek.com – Author: Ionut Arghire –
Source: www.securityweek.com – Author: Ionut Arghire. Category & Tags: Cybersecurity Funding,Funding/M&A,authorization,funding – Cybersecurity Funding,Funding/M&A,authorization,funding Cerbos, a startup offering an open source authorization layer solution for software...
LockBit ransomware encryptors found targeting Mac devices
The LockBit ransomware gang has created encryptors targeting Macs for the first time, likely becoming the first major ransomware operation to ever specifically target macOS. The...
CISA warns of Android bug exploited by Chinese app to spy on users
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned today of a high-severity Android vulnerability believed to have been exploited by a Chinese e-commerce app Pinduoduo...
Australians report record $3.1bn losses to scams, with real amount even higher, ACCC says
Australians lost a record amount of more than $3.1bn to scams in 2022, up from the $2bn lost in 2021, a new report from the Australian...
Labour glitch put voting intentions data of millions at risk
The voting intentions of millions of Britons in local authority wards across the country could have been at risk of misuse as a result of a...