Hey, it’s double-Troy! I’m playing with the Insta360 Link cam, a gimbal-based model that can follow you around the room. It’s tiny and pretty awesome for...
Day: April 2, 2023
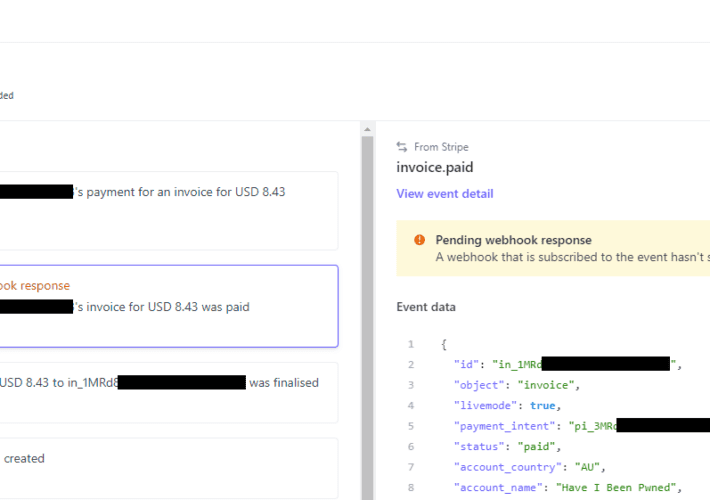
Down the Cloudflare / Stripe / OWASP Rabbit Hole: A Tale of 6 Rabbits Deep ? ? ? ? ? ?
I found myself going down a previously unexplored rabbit hole recently, or more specifically, what I thought was “a” rabbit hole but in actual fact was...
Weekly Update 335
No cyber. It’s literally a “cyber-free” week, as least far as the term relates to security things. Instead, I’m unboxing an armful of Insta360 goodies and...
LockBit leaks data stolen from the South Korean National Tax Service
The LockBit ransomware gang announced the publishing of data stolen from the South Korean National Tax Service. On March 29, 2023, The Lock Bit ransomware gang...
Italy’s Data Protection Authority temporarily blocks ChatGPT over privacy concerns
Italy’s data protection agency is temporarily blocking the popular chatbot ChatGPT due to a possible violation of the European data privacy regulation. The Italian Data Protection Authority, Garante...
CISA adds bugs exploited by commercial surveillance spyware to Known Exploited Vulnerabilities catalog
CISA has added nine flaws to its Known Exploited Vulnerabilities catalog, including bugs exploited by commercial spyware on mobile devices. U.S. Cybersecurity and Infrastructure Security Agency...
Hackers are actively exploiting a flaw in the Elementor Pro WordPress plugin
Threat actors are actively exploiting a high-severity flaw in the Elementor Pro WordPress plugin used by more than eleven million websites WordPress security firm PatchStack warns of a...
Cyber Police of Ukraine arrested members of a gang that defrauded EU citizens of $4.33M
The Cyber Police of Ukraine, with law enforcement officials from Czechia, has arrested several members of a gang responsible for $4.33 million scam. The Cyber Police...
Russian APT group Winter Vivern targets email portals of NATO and diplomats
Russian hacking group Winter Vivern has been actively exploiting Zimbra flaws to steal the emails of NATO and diplomats. A Russian hacking group, tracked Winter Vivern...
Super FabriXss vulnerability in Microsoft Azure SFX could lead to RCE
Researchers shared details about a flaw, dubbed Super FabriXss, in Azure Service Fabric Explorer (SFX) that could lead to unauthenticated remote code execution. Researchers from Orca...
New AlienFox toolkit harvests credentials for tens of cloud services
AlienFox is a novel comprehensive toolset for harvesting credentials for multiple cloud service providers, SentinelLabs reported. AlienFox is a new modular toolkit that allows threat actors...
3CX voice and video conferencing software victim of a supply chain attack
Popular voice and video conferencing software 3CX was the victim of a supply chain attack, SentinelOne researchers reported. As of Mar 22, 2023, SentinelOne observed a...
New Mélofée Linux malware linked to Chinese APT groups
Exatrack researchers warn of an unknown China-linked hacking group that has been linked to a new Linux malware, dubbed Mélofée. Cybersecurity researchers from ExaTrack recently discovered a...
Avoiding data backup failures – Week in security with Tony Anscombe
Today is World Backup Day, but maybe we also need a “did you test your backups” day? When did you last attempt to restore your data?...
World Backup Day: Avoiding a data disaster is a forever topic
By failing to prepare you are preparing to fail. Make sure you’re able to bounce back if, or when, a data disaster strikes. “Backup refers to...
ESET Research Podcast: A year of fighting rockets, soldiers, and wipers in Ukraine
ESET experts share their insights on the cyber-elements of the first year of the war in Ukraine and how a growing number of destructive malware variants...
Pig butchering scams: The anatomy of a fast‑growing threat
How fraudsters groom their marks and move in for the kill using tricks from the playbooks of romance and investment scammers Sometimes you have to say...
Staying safe on OnlyFans: The naked truth
How content creators and subscribers can embrace the social media platform without (overly) exposing themselves to the potentially toxic brew of NSFW content and privacy threats...
Highlights from TikTok CEO’s Congress grilling – Week in security with Tony Anscombe
Here are some of the key moments from the five hours of Shou Zi Chew’s testimony and other interesting news on the data privacy front As...
What TikTok knows about you – and what you should know about TikTok
As TikTok CEO attempts to placate U.S. lawmakers, it’s time for us all to think about the wealth of personal information that TikTok and other social...
Twitter ends free SMS 2FA: Here’s how you can protect your account now
Twitter’s ditching of free text-message authentication doesn’t mean that you should forgo using 2FA. Instead, switch to another – and, indeed, better – 2FA option. Starting...
Banking turmoil opens opportunities for fraud – Week in security with Tony Anscombe
Scammers are looking to cash in on the chaos that has set in following the startling meltdowns of Silicon Valley Bank and Signature Bank and the...
SVB’s collapse is a scammer’s dream: Don’t get caught out
How cybercriminals can exploit Silicon Valley Bank’s downfall for their own ends – and at your expense Big news events and major crises usually trigger an...
Not‑so‑private messaging: Trojanized WhatsApp and Telegram apps go after cryptocurrency wallets
ESET researchers analyzed Android and Windows clippers that can tamper with instant messages and use OCR to steal cryptocurrency funds ESET researchers have discovered dozens of...
The slow Tick‑ing time bomb: Tick APT group compromise of a DLP software developer in East Asia
ESET Research uncovered a campaign by APT group Tick against a data-loss prevention company in East Asia and found a previously unreported tool used by the...
5 signs you’ve fallen for a scam – and what to do next
Here’s how to know you have fallen victim to a scam – and what to do in order to undo or mitigate the damage. Online fraud...
APT hackers set a honeytrap to ensnare victims – Week in security with Tony Anscombe
A request to move an online conversation to a supposedly more secure platform may not be as well-meaning as it sounds Have you ever been asked...
Common WhatsApp scams and how to avoid them
Here’s a roundup of some of the most common tricks that fraudsters use to dupe their victims on WhatsApp – and what you can do to...
‘A woman from Mars’: Life in the pursuit of space exploration
An astrobiologist, analog astronaut, author and speaker, Dr. Michaela Musilova shares her experience as a woman at the forefront of space exploration and from her quest...
Love scam or espionage? Transparent Tribe lures Indian and Pakistani officials
ESET researchers analyze a cyberespionage campaign that distributes CapraRAT backdoors through trojanized and supposedly secure Android messaging apps – but also exfiltrates sensitive information ESET researchers...