UK parliament follows government by banning TikTok over cybersecurity concernsThe commissions of the House of Commons and House of Lords have followed the UK government by...
Day: March 24, 2023
Critical flaw in AI testing framework MLflow can lead to server and data compromise
Critical flaw in AI testing framework MLflow can lead to server and data compromiseMLflow, an open-source framework that's used by many organizations to manage their machine-learning...
Android-based banking Trojan Nexus now available as malware-as-a-service
Android-based banking Trojan Nexus now available as malware-as-a-serviceItalian cybersecurity firm Cleafy has found “Nexus”, a new Android Trojan capable of hijacking online accounts and siphoning funds...
Security Flaws Cost Fifth of Execs Business
Security Flaws Cost Fifth of Execs BusinessBusiness leaders still underestimate importance of security to growthRead MoreBusiness leaders still underestimate importance of security to growth
UK Parliament Bans TikTok from its Network and Devices
UK Parliament Bans TikTok from its Network and DevicesFurther blow for Chinese social media appRead MoreFurther blow for Chinese social media app
IRS Phishing Emails Used to Distribute Emotet
IRS Phishing Emails Used to Distribute EmotetMonster 500MB attachment hides a nasty surpriseRead MoreMonster 500MB attachment hides a nasty surprise
GitHub Updates Security Protocol For Operations Over SSH
GitHub Updates Security Protocol For Operations Over SSHThe move reportedly did not stem from a compromise of GitHub systems or customer informationRead MoreThe move reportedly did...
WooCommerce Patches Critical Plugin Flaw Affecting Half a Million Sites
WooCommerce Patches Critical Plugin Flaw Affecting Half a Million SitesThe vulnerability could allow an unauthenticated attacker to gain admin privileges and take over a websiteRead MoreThe...
CISA Unveils Ransomware Notification Initiative
CISA Unveils Ransomware Notification InitiativeProvides businesses with early warnings to evict threat actors before they can encrypt dataRead MoreProvides businesses with early warnings to evict threat...
Pwn2Own Vancouver 2023 Day 2: Microsoft Teams, Oracle VirtualBox, and Tesla hacked
Pwn2Own Vancouver 2023 Day 2: Microsoft Teams, Oracle VirtualBox, and Tesla hackedOn the second day of Pwn2Own Vancouver 2023, the organization awarded $475,000 for 10 unique...
Critical flaw in WooCommerce Payments plugin allows site takeover
Critical flaw in WooCommerce Payments plugin allows site takeoverA patch for a critical vulnerability in the WooCommerce Payments plugin for WordPress has been released for over...
Drive-by Download Attack – What It Is and How It Works
Drive-by Download Attack – What It Is and How It WorksIn today’s digital age, cybersecurity is more important than ever before. Unfortunately, cybercriminals are constantly finding...
The City of Toronto, Among This Week’s Victims of GoAnywhere Attacks
The City of Toronto, Among This Week’s Victims of GoAnywhere AttacksThe City of Toronto announced a data breach caused by GoAnywhere attacks. Clop ransomware, the gang...
Enhanced Version of the BlackGuard Stealer Spotted in the Wild
Enhanced Version of the BlackGuard Stealer Spotted in the WildA new variant of the BlackGuard stealer has been discovered in the wild, with new features such...
The Most Prevalent Types of Ransomware You Need to Know About
The Most Prevalent Types of Ransomware You Need to Know AboutCyberthieves of today are adaptable – they are excellent at finding new ways to survive and...
Chinese Hackers Infiltrate Middle Eastern Telecom Companies
Chinese Hackers Infiltrate Middle Eastern Telecom CompaniesNew cyber attacks against Middle Eastern telecommunications operators emerged in the first quarter of 2023. Based on technical overlaps, the...
Find Out What Is a Logic Bomb. Definition, Characteristics, and Protection Measures
Find Out What Is a Logic Bomb. Definition, Characteristics, and Protection MeasuresToday we are talking about one of the sneakiest cybersecurity threats out there: the logic...
What Is Quishing: QR Code Phishing Explained
What Is Quishing: QR Code Phishing ExplainedAre you aware of QR code phishing or “quishing”? This form of social engineering attack is gaining popularity among cybercriminals...
Exploding USB Sticks
Exploding USB SticksIn case you don’t have enough to worry about, people are hiding explosives—actual ones—in USB sticks: In the port city of Guayaquil, journalist Lenin...
Guidelines for building security policies
Guidelines for building security policiesPURPOSE These guidelines from TechRepublic Premium will help you define the necessary ingredients of a security policy and assist in its proper...
GitHub.com rotates its exposed private SSH key
GitHub.com rotates its exposed private SSH keyGitHub has rotated its private SSH key for GitHub.com after the secret was was accidentally published in a public GitHub repository. The software...
‘Bitter’ espionage hackers target Chinese nuclear energy orgs
'Bitter' espionage hackers target Chinese nuclear energy orgsA cyberespionage hacking group tracked as 'Bitter APT' was recently seen targeting the Chinese nuclear energy industry using phishing...
UK creates fake DDoS-for-hire sites to identify cybercriminals
UK creates fake DDoS-for-hire sites to identify cybercriminalsThe U.K.'s National Crime Agency (NCA) revealed today that they created multiple fake DDoS-for-hire service websites to identify cybercriminals who...
Procter & Gamble confirms data theft via GoAnywhere zero-day
Procter & Gamble confirms data theft via GoAnywhere zero-dayConsumer goods giant Procter & Gamble has confirmed a data breach affecting an undisclosed number of employees after...
How one CEO founded a successful cyber security company
How one CEO founded a successful cyber security companyAs we celebrate Women’s History Month, we’re recognizing the significant women who have played a role in shaping...
GitHub Replaces Private RSA SSH Key After Public Exposure
GitHub Replaces Private RSA SSH Key After Public Exposure'Abundance of Caution' Cited for Move; No System Compromise or Data Breach DetectedGitHub has replaced its private RSA...
Informe de Madurez de la Ciberseguridad de 2023 revela la falta de preparación de las organizaciones para los ataques cibernéticos
Informe de Madurez de la Ciberseguridad de 2023 revela la falta de preparación de las organizaciones para los ataques cibernéticosSolo en 2022, los ataques cibernéticos globales...
Russian hacktivists deploy new AresLoader malware via decoy installers
Russian hacktivists deploy new AresLoader malware via decoy installersSecurity researchers have started seeing attack campaigns that use a relatively new malware-as-a-service (MaaS) tool called AresLoader. The...
Cisco fixed multiple severe vulnerabilities in its IOS and IOS XE software
Cisco fixed multiple severe vulnerabilities in its IOS and IOS XE softwareCisco addressed tens of vulnerabilities in its IOS and IOS XE software, six of these...
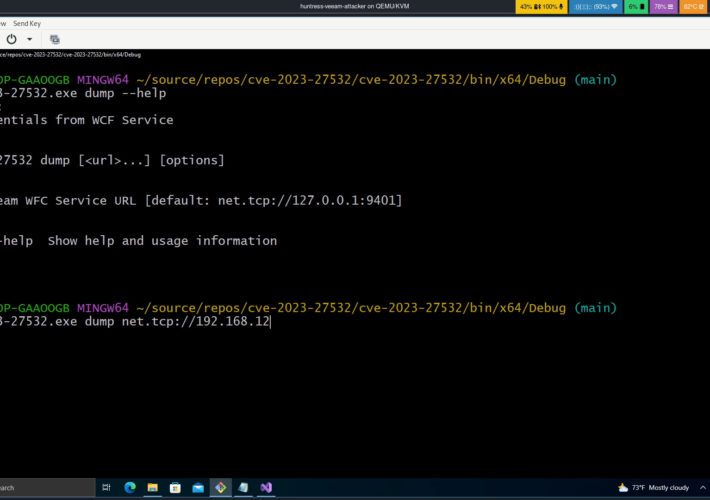
Experts published PoC exploit code for Veeam Backup & Replication bug
Experts published PoC exploit code for Veeam Backup & Replication bugResearchers released a PoC exploit code for a high-severity vulnerability in Veeam Backup & Replication (VBR)...