9 attack surface discovery and management toolsCyber asset attack surface management (CAASM) or external attack surface management (EASM) solutions are designed to quantify the attack surface...
Day: March 23, 2023
Developed countries lag emerging markets in cybersecurity readiness
Developed countries lag emerging markets in cybersecurity readinessOrganizations in developed countries are not as prepared for cybersecurity incidents compared to those in developing countries, according to...
BrandPost: Stop the Sprawl: How Vendor Consolidation Can Reduce Security Risks in the Cloud
BrandPost: Stop the Sprawl: How Vendor Consolidation Can Reduce Security Risks in the CloudManaging multiple security vendors is proving to be a significant challenge for organizations,...
As critical Microsoft vulnerabilities drop, attackers may adopt new techniques
As critical Microsoft vulnerabilities drop, attackers may adopt new techniquesWhile the total number of recorded Microsoft vulnerabilities was higher in 2022 than ever before, the number...
Ping Identity debuts decentralized access management system in early access
Ping Identity debuts decentralized access management system in early accessPing Identity, a Colorado-based IAM software vendor, is making a new product, PingOne Neo, available in a...
Sharing sensitive business data with ChatGPT could be risky
Sharing sensitive business data with ChatGPT could be riskyThe furor surrounding ChatGPT remains at a fever pitch as the ins and outs of the AI chatbot’s...
Backslash AppSec solution targets toxic code flows, threat model automation
Backslash AppSec solution targets toxic code flows, threat model automationBackslash Security has announced its launch with a new cloud-native application security (AppSec) solution designed to identify...
Average enterprise storage/backup device has 14 vulnerabilities, three high or critical risks
Average enterprise storage/backup device has 14 vulnerabilities, three high or critical risksThe average enterprise storage and backup device has 14 vulnerabilities, three of which are high...
Landmark UK-Israeli agreement to boost mutual cybersecurity development, tackle shared threats
Landmark UK-Israeli agreement to boost mutual cybersecurity development, tackle shared threatsThe UK and Israeli governments have signed a landmark agreement to define bilateral relations between the...
55 zero-day flaws exploited last year show the importance of security risk management
55 zero-day flaws exploited last year show the importance of security risk managementDeploying security patches as quickly as possible remains one of the best ways to...
Splunk adds new security and observability features
Splunk adds new security and observability featuresNew security and observability features will be added to Splunk Mission Control and its Observability Cloud to identify threats and...
How training and recognition can reduce cybersecurity stress and burnout
How training and recognition can reduce cybersecurity stress and burnoutCybersecurity is a demanding profession that comes with significant stress and burnout — it presents a complex...
New vulnerabilities found in industrial control systems of major vendors
New vulnerabilities found in industrial control systems of major vendorsThe US Cybersecurity and Infrastructure Security Agency (CISA) has issued advisories on 49 vulnerabilities in eight industrial...
Security at the core of Intel’s new vPro platform
Security at the core of Intel’s new vPro platformIntel has introduced its 13th Generation Core processor line, which the company claims is the first to build...
Understanding Managed Detection and Response – and what to look for in an MDR solution
Understanding Managed Detection and Response – and what to look for in an MDR solutionWhy your organization should consider an MDR solution and five key things...
Ransomware Attacks Double in Europe’s Transport Sector
Ransomware Attacks Double in Europe's Transport SectorENISA claims most threats are opportunisticRead MoreENISA claims most threats are opportunistic
Just 1% of Dot-Org Domains Are Fully DMARC Protected
Just 1% of Dot-Org Domains Are Fully DMARC ProtectedOrganizations are failing with their anti-phishing measuresRead MoreOrganizations are failing with their anti-phishing measures
Security Researchers Spot $36m BEC Attack
Security Researchers Spot $36m BEC AttackThreat actors impersonated target company's vendorRead MoreThreat actors impersonated target company's vendor
CISA and NSA Enhance Security Framework With New IAM Guide
CISA and NSA Enhance Security Framework With New IAM GuideGuidance includes best practices for identity governance, environmental hardening, SSO, MFA and IAM auditingRead MoreGuidance includes best...
New Android Banking Trojan ‘Nexus’ Promoted As MaaS
New Android Banking Trojan 'Nexus' Promoted As MaaSNexus offers overlay attacks and keylogging activities designed to steal victims' credentialsRead MoreNexus offers overlay attacks and keylogging activities...
BreachForums Shuts Down After Admin’s Arrest
BreachForums Shuts Down After Admin's ArrestThe forum's admin said the move might be temporary and that they will set up a new Telegram groupRead MoreThe forum's...
Irish Food Giant Dole Admits Employee Data Breach
Irish Food Giant Dole Admits Employee Data BreachIncident was linked to previously disclosed ransomware attackRead MoreIncident was linked to previously disclosed ransomware attack
Malicious ChatGPT Chrome Extension Hijacks Facebook Accounts
Malicious ChatGPT Chrome Extension Hijacks Facebook AccountsSoftware was unwittingly downloaded thousands of timesRead MoreSoftware was unwittingly downloaded thousands of times
UK Government Sets Out Vision for NHS Cybersecurity
UK Government Sets Out Vision for NHS CybersecurityPlans to boost cyber-resilience in the health service by 2030Read MorePlans to boost cyber-resilience in the health service by...
New Post-Exploitation Attack Method Found Affecting Okta Passwords
New Post-Exploitation Attack Method Found Affecting Okta PasswordsThe flaw derives from the way the Okta system records failed login attempts to instancesRead MoreThe flaw derives from...
SharePoint Phishing Scam Targets 1600 Across US, Europe
SharePoint Phishing Scam Targets 1600 Across US, EuropeCyber-criminals used the scam to steal the credentials for various email accountsRead MoreCyber-criminals used the scam to steal the...
China-Aligned “Operation Tainted Love” Targets Middle East Telecom Providers
China-Aligned "Operation Tainted Love" Targets Middle East Telecom ProvidersThe deployment of custom credential theft malware is the main novelty of the new campaignRead MoreThe deployment of...
Cisco Event Response: March 2023 Semiannual Cisco IOS and IOS XE Software Security Advisory Bundled Publication
Cisco Event Response: March 2023 Semiannual Cisco IOS and IOS XE Software Security Advisory Bundled PublicationPost ContentRead MoreCisco Event Responses
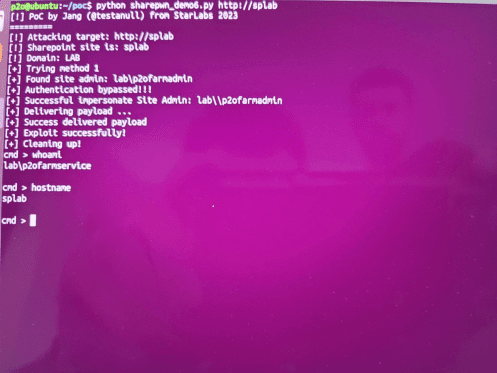
Pwn2Own Vancouver 2023 Day 1: Windows 11 and Tesla hacked
Pwn2Own Vancouver 2023 Day 1: Windows 11 and Tesla hackedOn the first day of Pwn2Own Vancouver 2023, the organization awarded $375,000 (and a Tesla Model 3)...
Dole discloses data breach after February ransomware attack
Dole discloses data breach after February ransomware attackDole Food Company confirmed that threat actors behind the recent ransomware attack had access to employees’ data. Dole Food...