CloudBees flaws in Jenkins server can lead to code executionCloudBees vulnerabilities in the Jenkins open-source automation server can be exploited to achieve code execution on targeted...
Day: March 10, 2023
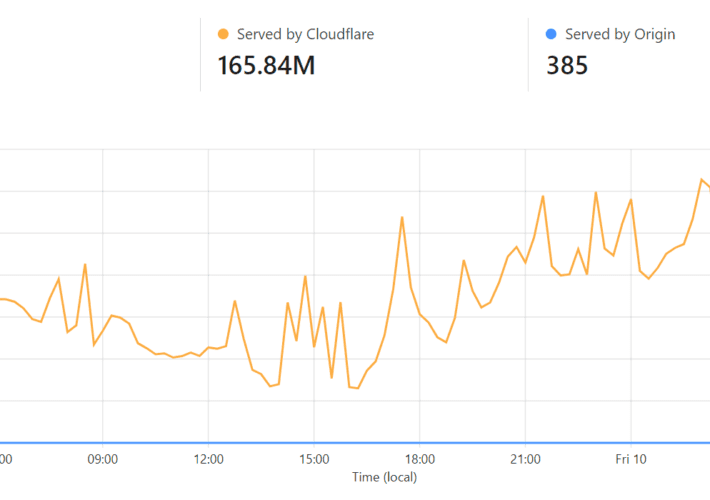
To Infinity and Beyond, with Cloudflare Cache Reserve
To Infinity and Beyond, with Cloudflare Cache ReserveWhat if I told you... that you could run a website from behind Cloudflare and only have 385 daily...
How to Get on the Dark Web: A Step-by-Step Guide
How to Get on the Dark Web: A Step-by-Step GuideDark web, deep web, clear web – just words or more? Well, in seeing just how many...
Top 5 Must-Watch XDR Videos from Heimdal®
Top 5 Must-Watch XDR Videos from Heimdal®As we have seen in our previous articles, news, and webinars, in this increasingly complex threat landscape, malicious actors employ...
Access Control-as-a-Service: What It Is and How Can Organizations Benefit from It?
Access Control-as-a-Service: What It Is and How Can Organizations Benefit from It?In today’s fast-paced digital world, identity and access management has become a critical concern for...
Warning! BMW Security Flaw Jeopardises Business Secrets and Clients` Data
Warning! BMW Security Flaw Jeopardises Business Secrets and Clients` DataThe famous BMW luxury cars brand unproperly secured its system and exposed extremely sensitive files to the...
5 Ways Heimdal® Protects Your Endpoints
5 Ways Heimdal® Protects Your EndpointsIn the book about cybersecurity, protecting your endpoints must be the first and one of the most important chapters. Once an...
The Intersection of Gender, Politics, and Cybersecurity: Iranian Hackers Target Women Advocating for Human Rights
The Intersection of Gender, Politics, and Cybersecurity: Iranian Hackers Target Women Advocating for Human RightsIranian state-sponsored actors continue to target researchers by impersonating US think tanks....
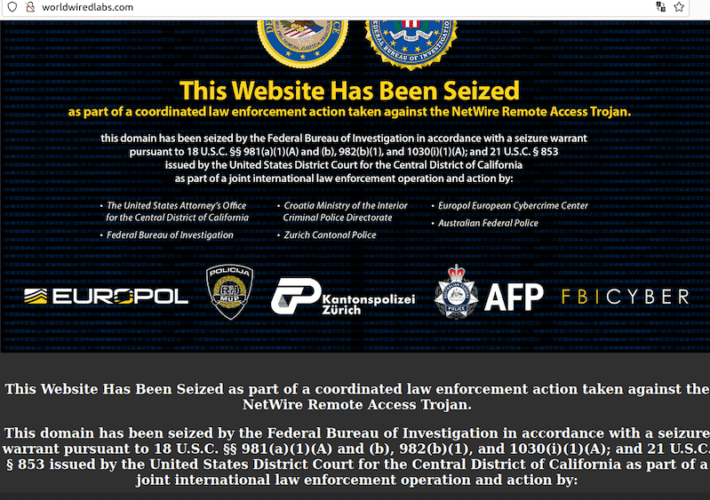
Netwire RAT Malware Infrastructure Seized Following Joint International Operation
Netwire RAT Malware Infrastructure Seized Following Joint International OperationAn internet domain that was being used by criminals to steal data from and take control of victims’...
Deep Web vs. Dark Web: What is Each and How Do They Work
Deep Web vs. Dark Web: What is Each and How Do They WorkYou may have heard these concepts being thrown around, but you don’t really know...
The Onion Patch – Best 20 Dark Web Websites You Shouldn’t Miss
The Onion Patch – Best 20 Dark Web Websites You Shouldn’t MissSo, you took my course on how to get on the dark web and want...
Pirated copies of Final Cut Pro infect Macs with cryptojacking malware
Pirated copies of Final Cut Pro infect Macs with cryptojacking malwareTorrents on The Pirate Bay which claim to contain Final Cut Pro are instead being used...
WhatsApp and UK government on collision course, as app vows not to remove end-to-end encryption
WhatsApp and UK government on collision course, as app vows not to remove end-to-end encryptionThe boss of WhatsApp, the most popular messaging platform in the UK,...
Protect the Whole Family with McAfee+ Ultimate Family Plan
Protect the Whole Family with McAfee+ Ultimate Family PlanDozens of content creators center their channels on highlighting the differences between today’s most prominent generations: the Silent...
Cloud security, hampered by proliferation of tools, has a “forest for trees” problem
Cloud security, hampered by proliferation of tools, has a “forest for trees” problemC-Suites executives have cybersecurity insecurities around cloud development, deployment and visibility, a Palo Alto...
Xenomorph Android malware now steals data from 400 banks
Xenomorph Android malware now steals data from 400 banksThe Xenomorph Android malware has released a new version that adds significant capabilities to conduct malicious attacks, including...
Mental health provider Cerebral alerts 3.1M people of data breach
Mental health provider Cerebral alerts 3.1M people of data breachHealthcare platform Cerebral is sending data breach notices to 3.18 million people who have interacted with its...
Blackbaud to pay $3M for misleading ransomware attack disclosure
Blackbaud to pay $3M for misleading ransomware attack disclosureCloud software provider Blackbaud has agreed to pay $3 million to settle charges brought by the Securities and Exchange Commission (SEC), alleging...
CISA warns of critical VMware RCE flaw exploited in attacks
CISA warns of critical VMware RCE flaw exploited in attacksCISA has added a critical severity vulnerability in VMware's Cloud Foundation to its catalog of security flaws...
Security researchers targeted with new malware via job offers on LinkedIn
Security researchers targeted with new malware via job offers on LinkedInA suspected North Korean hacking group is targeting security researchers and media organizations in the U.S. and...
ISMG Editors: Assessing the New US Cybersecurity Strategy
ISMG Editors: Assessing the New US Cybersecurity StrategyAlso: Panel Discusses Vendor Liability, Ransomware and the Rise of Check FraudIn the latest weekly update, ISMG editors discuss...
La nueva versión de Prometei Botnet infecta más de 10 000 sistemas en todo el mundo
La nueva versión de Prometei Botnet infecta más de 10 000 sistemas en todo el mundoUna versión actualizada de un malware de botnet llamado Prometei ha...
CloudBees flaws in Jenkins server can lead to code execution
CloudBees flaws in Jenkins server can lead to code executionCloudBees vulnerabilities in the Jenkins open-source automation server can be exploited to achieve code execution on targeted...
TSA tells US aviation industry to boost its cybersecurity
TSA tells US aviation industry to boost its cybersecurityThe US Transportation and Security Administration (TSA) has issued new requirements for airport and aircraft operators who, they...
Another Malware with Persistence
Another Malware with PersistenceHere’s a piece of Chinese malware that infects SonicWall security appliances and survives firmware updates. On Thursday, security firm Mandiant published a report...
Who’s Behind the NetWire Remote Access Trojan?
Who’s Behind the NetWire Remote Access Trojan?A Croatian national has been arrested for allegedly operating NetWire, a Remote Access Trojan (RAT) marketed on cybercrime forums since...
Amplifying Power to Customer Through Ecosystem Integrations
Amplifying Power to Customer Through Ecosystem IntegrationsTransformation to a SaaS-based cybersecurity vendorRead MoreTrend Micro Research, News, PerspectivesTransformation to a SaaS-based cybersecurity vendor
Remote access policy
Remote access policyPURPOSE This policy outlines guidelines and processes for requesting, obtaining, using and terminating remote access to organization networks, systems and data. It applies to...
GitHub rolling out two-factor authentication to millions of users
GitHub rolling out two-factor authentication to millions of usersOver the next nine months, the largest internet hosting service for software development and collaboration will make all...
Microsoft: Business email compromise attacks can take just hours
Microsoft: Business email compromise attacks can take just hoursMicrosoft's Security Intelligence team recently investigated a business email compromise (BEC) attack and found that attackers move rapidly,...