US Gov. Agencies Have 30 Days to Remove TikTok, Canada Follows SuitWithin 90 days, agencies must also cancel existing contracts that necessitate the app's useRead MoreWithin...
Day: February 28, 2023
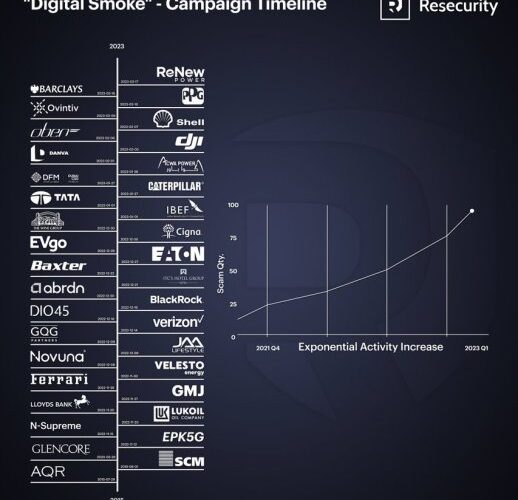
Resecurity identified the investment scam network ‘Digital Smoke’
Resecurity identified the investment scam network ‘Digital Smoke’Resecurity identified one of the largest investment fraud networks, tracked as Digital Smoke, by size and volume of operations....
CISA adds ZK Java Web Framework bug to Known Exploited Vulnerabilities Catalog
CISA adds ZK Java Web Framework bug to Known Exploited Vulnerabilities CatalogUS CISA added an actively exploited vulnerability in the ZK Java Web Framework to its...
U.S. Marshals Service suffers a ransomware attack
U.S. Marshals Service suffers a ransomware attackThe U.S. Marshals Service (USMS) was the victim of a ransomware attack, it is investigating the theft of sensitive information....
Exfiltrator-22, a New Post-exploitation Kit for Sale
Exfiltrator-22, a New Post-exploitation Kit for SaleExfiltrator-22 is a new post-exploitation kit that can spread ransomware undetected. Researchers speculate that the creators of this kit are...
What Is a Port Scan Attack? Definition and Prevention Measures for Enterprises
What Is a Port Scan Attack? Definition and Prevention Measures for EnterprisesA port scan attack is a technique that enables threat actors to find server vulnerabilities....
Major Ransomware Attack on U.S. Marshals Service Compromises Sensitive Information
Major Ransomware Attack on U.S. Marshals Service Compromises Sensitive InformationAccording to multiple senior U.S. law enforcement officials, the U.S. Marshals Service suffered a security breach more...
15M Allegedly Peruvian Tax Authority Records Leaked on Forum
15M Allegedly Peruvian Tax Authority Records Leaked on ForumPeruvian citizens are at risk of identity theft and financial fraud following the exposure of a database allegedly...
Busting Myths Around Cybersecurity Team Training
Busting Myths Around Cybersecurity Team TrainingNew Research Results from Omdia and Cybrary Point to Substantial ROI From Continuous Upskilling of Cybersecurity Teams. By Kevin Hanes, CEO,...
CredPump, HoaxPen, and HoaxApe Backdoor Detection: UAC-0056 Hackers Launch Disruptive Attacks Against Ukrainian Government Websites Planned Over One Year Earlier
CredPump, HoaxPen, and HoaxApe Backdoor Detection: UAC-0056 Hackers Launch Disruptive Attacks Against Ukrainian Government Websites Planned Over One Year Earlier Approaching the date of one-year anniversary...
Side-Channel Attack against CRYSTALS-Kyber
Side-Channel Attack against CRYSTALS-KyberCRYSTALS-Kyber is one of the public-key algorithms currently recommended by NIST as part of its post-quantum cryptography standardization process. Researchers have just published...
Hackers Claim They Breached T-Mobile More Than 100 Times in 2022
Hackers Claim They Breached T-Mobile More Than 100 Times in 2022 Image: Shutterstock.com Three different cybercriminal groups claimed access to internal networks at communications giant T-Mobile...
The Reviews are In—McAfee+ Earns Top Marks from Review Sites
The Reviews are In—McAfee+ Earns Top Marks from Review Sites We created McAfee+ so people can be safe and feel safe online, particularly in a time...
Our commitment to fighting invalid traffic on Connected TV
Our commitment to fighting invalid traffic on Connected TVPosted by Michael Spaulding, Senior Product Manager, Ad Traffic Quality Connected TV (CTV) has not only transformed the...
Microsoft adds AI-powered Bing Chat to Windows 11 taskbar
Microsoft adds AI-powered Bing Chat to Windows 11 taskbarMicrosoft announced today that it's integrating the new AI-powered Bing Chat into the Windows 11 search box with...
Windows 11 ‘Moment 2’ update released, here are the many new features
Windows 11 ‘Moment 2’ update released, here are the many new featuresMicrosoft has released the Windows 11 22H2 'Moment 2' update, bringing many new and long-awaited...
Microsoft Phone Link can now sync your iPhone with Windows 11
Microsoft Phone Link can now sync your iPhone with Windows 11Microsoft announced today an early preview of Phone Link for iPhone users available to Windows Insiders...
SCARLETEEL hackers use advanced cloud skills to steal source code, data
SCARLETEEL hackers use advanced cloud skills to steal source code, dataAn advanced hacking operation dubbed 'SCARLETEEL' targets public-facing web apps running in containers to infiltrate cloud...
Google: Gmail client-side encryption now publicly available
Google: Gmail client-side encryption now publicly availableGmail client-side encryption (CSE) is now generally available for Google Workspace Enterprise Plus, Education Plus, and Education Standard customers. [...]Read...
Google Chrome optimizations improve battery life on Macs
Google Chrome optimizations improve battery life on MacsThe latest version of Google Chrome for macOS (110.0.5481.100) includes new optimizations that increase battery life on MacBooks. [...]Read...
Dish Network confirms ransomware attack behind multi-day outage
Dish Network confirms ransomware attack behind multi-day outageSatellite broadcast provider and TV giant Dish Network has finally confirmed that a ransomware attack was the cause of...
CISO learning and training: Key insights for security leaders
CISO learning and training: Key insights for security leadersLiat Doron is the Vice President of Learning and Training at Check Point Software Technologies. In this exclusive...
GUEST ESSAY: Testing principles to mitigate real-world risks to ‘SASE’ and ‘Zero Trust’ systems
GUEST ESSAY: Testing principles to mitigate real-world risks to ‘SASE’ and ‘Zero Trust’ systemsA new generation of security frameworks are gaining traction that are much better...
Ransomware attack on US Marshals compromises sensitive information
Ransomware attack on US Marshals compromises sensitive informationFederal agency best known for tracking down fugitives suffered security breach on 17 February The US Marshals service fell...
Closing the Gap in Threat Visibility
Closing the Gap in Threat VisibilityThe Technologies You Need to See Into Those Dark CornersA lack of visibility makes it nearly impossible to protect an organization...
Validate, Verify and Authenticate your Customer Identity
Validate, Verify and Authenticate your Customer IdentityPost ContentRead MoreDataBreachToday.com RSS Syndication
Don’t Be Held Hostage: Detect and Intercept Pre-Ransomware Activity and Ransom Notes
Don't Be Held Hostage: Detect and Intercept Pre-Ransomware Activity and Ransom NotesPost ContentRead MoreDataBreachToday.com RSS Syndication
CyberMaxx Taps Ex-Threat Stack CEO to Aid Offensive Security
CyberMaxx Taps Ex-Threat Stack CEO to Aid Offensive SecurityBrian Ahern Plans to Infuse CyberMaxx's MDR Tool With Offensive Security ExpertiseCyberMaxx has landed the former CEO of...
Chinese State Hackers Level Up Their Abilities: CrowdStrike
Chinese State Hackers Level Up Their Abilities: CrowdStrikeBeijing Looks for Enterprise Software Zero-DaysA Chinese law requiring mandatory disclosure to the government of vulnerability reports appears to...
La nueva herramienta EX-22 permite a los piratas informáticos realizar ataques sigilosos de ransomware a empresas
La nueva herramienta EX-22 permite a los piratas informáticos realizar ataques sigilosos de ransomware a empresasHa surgido un nuevo marco posterior a la explotación llamado EXFILTRATOR-22...