Web3 IPFS Currently Used For PhishingWe discuss the use of the InterPlanetary File System (IPFS) in phishing attacks.Leer másTrend Micro Research, News, PerspectivesWe discuss the use...
Day: December 23, 2022
Diving into an Old Exploit Chain and Discovering 3 new SIP-Bypass Vulnerabilities
Diving into an Old Exploit Chain and Discovering 3 new SIP-Bypass VulnerabilitiesMore than two years ago, a researcher, A2nkF demonstrated the exploit chain from root privilege...
Hacking the JFK Airport Taxi Dispatch System
Hacking the JFK Airport Taxi Dispatch SystemTwo men have been convicted of hacking the taxi dispatch system at the JFK airport. This enabled them to reorder...
Raspberry Robin Malware Targets Telecom, Governments
Raspberry Robin Malware Targets Telecom, GovernmentsWe found samples of the Raspberry Robin malware spreading in telecommunications and government office systems beginning September. The main payload itself...
FIN7 hackers create auto-attack platform to breach Exchange servers
FIN7 hackers create auto-attack platform to breach Exchange serversThe notorious FIN7 hacking group uses an auto-attack system that exploits Microsoft Exchange and SQL injection vulnerabilities to...
Samsung and Google fix Microsoft Intune Android 13 enrollment issue
Samsung and Google fix Microsoft Intune Android 13 enrollment issueMicrosoft has confirmed today that Samsung and Google have fixed an Intune enrollment issue affecting Galaxy S22...
My Top Tips To Help Your Family Stay Safe Online This Holiday Period
My Top Tips To Help Your Family Stay Safe Online This Holiday Period ‘It’s the most wonderful time of year’ – we’ve all heard the jingles...
Conti Team One Splinter Group Resurfaces as Royal Ransomware with Callback Phishing Attacks
Conti Team One Splinter Group Resurfaces as Royal Ransomware with Callback Phishing AttacksFrom September to December, we detected multiple attacks from the Royal ransomware group. In...
Get 40% off Malwarebytes Premium for the holidays
Get 40% off Malwarebytes Premium for the holidaysMalwarebytes is running a holiday deal where you can get 40% off the Malwarebytes Premium antivirus software through the new year....
A Technical Analysis of CVE-2022-22583 and CVE-2022-32800
A Technical Analysis of CVE-2022-22583 and CVE-2022-32800This blog entry discusses the technical details of how we exploited CVE-2022-22583 using a different method. We also tackle the...
Uber’s latest data breach reveals how to improve third-party security…
Uber’s latest data breach reveals how to improve third-party security…EXECUTIVE SUMMARY: In Uber’s latest data breach, hackers managed to expose employee email addresses, corporate reports and...
Brave launches FrodoPIR, a privacy-focused database query system
Brave launches FrodoPIR, a privacy-focused database query systemBrave Software developers have created a new privacy-centric database query system called FrodoPIR that retrieves data from servers without disclosing...
Comcast Xfinity accounts hacked in widespread 2FA bypass attacks
Comcast Xfinity accounts hacked in widespread 2FA bypass attacksComcast Xfinity customers report their accounts being hacked in widespread attacks that bypass two-factor authentication. These compromised accounts...
A tell-all conversation: The biggest cloud security trends, challenges & solutions
A tell-all conversation: The biggest cloud security trends, challenges & solutionsEXECUTIVE SUMMARY: In this dynamic tell-all conversation, excerpted from The TechArena podcast, VP of Cloud Security...
Vice Society ransomware gang switches to new custom encryptor
Vice Society ransomware gang switches to new custom encryptorThe Vice Society ransomware operation has switched to using a custom ransomware encrypt that implements a strong, hybrid...
Detecting Windows AMSI Bypass Techniques
Detecting Windows AMSI Bypass TechniquesWe look into some of the implementations that cybercriminals use to bypass the Windows Antimalware Scan Interface (AMSI) and how security teams...
Payroll processing checklist
Payroll processing checklistSome operations and tasks don’t require painstaking attention to detail. Unfortunately, processing payroll isn’t one of them. With sensitive salary and wage information, bank...
DuckDuckGo now blocks Google sign-in pop-ups on all sites
DuckDuckGo now blocks Google sign-in pop-ups on all sitesDuckDuckGo apps and extensions are now blocking Google Sign-in pop-ups on all its apps and browser extensions, removing...
IcedID Botnet Distributors Abuse Google PPC to Distribute Malware
IcedID Botnet Distributors Abuse Google PPC to Distribute MalwareWe analyze the latest changes in IcedID botnet from a campaign that abuses Google pay per click (PPC)...
Proofpoint Nabs Illusive, Signaling a Sunset for Deception Tech
Proofpoint Nabs Illusive, Signaling a Sunset for Deception TechContenido de la entradaLeer másProofpoint News Feed
Leading sports betting firm BetMGM discloses data breach
Leading sports betting firm BetMGM discloses data breachLeading sports betting company BetMGM disclosed a data breach after a threat actor stole personal information belonging to an...
Ransomware, DDoS see major upsurge led by upstart hacker group
Ransomware, DDoS see major upsurge led by upstart hacker groupCyber threat actors Cuba and Royal are driving a 41% boom in ransomware and other attacks hitting...
Lastpass: Hackers stole customer vault data in cloud storage breach
Lastpass: Hackers stole customer vault data in cloud storage breachLastPass revealed today that attackers stole customer vault data after breaching its cloud storage earlier this year...
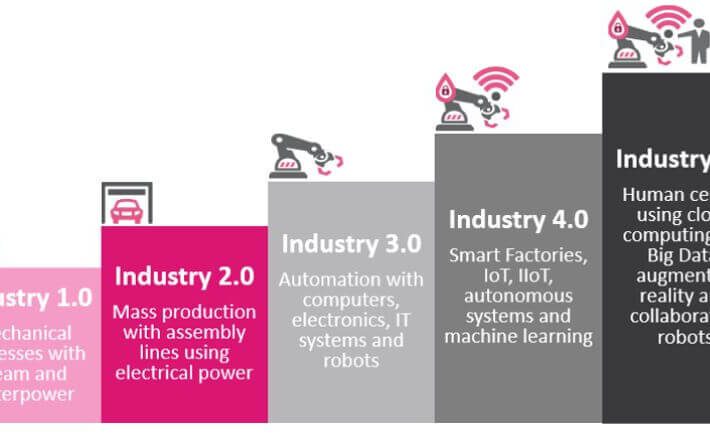
Bringing back the human in technology with Industry 5.0
Bringing back the human in technology with Industry 5.0By Antoinette Hodes, Check Point Solutions Architect EMEA, Office of the CTO. What was the industrial revolution? The...
Ghost CMS vulnerable to critical authentication bypass flaw
Ghost CMS vulnerable to critical authentication bypass flawA critical vulnerability in the Ghost CMS newsletter subscription system could allow external users to create newsletters or modify...
Iranian state-aligned threat actor targets new victims in cyberespionage and kinetic campaigns
Iranian state-aligned threat actor targets new victims in cyberespionage and kinetic campaignsContenido de la entradaLeer másProofpoint News Feed
Cisco Talos report: Threat actors use known Excel vulnerability
Cisco Talos report: Threat actors use known Excel vulnerabilityThe use of .XLL Excel files by threat actors to infect computers with malware is growing fast. Learn...
CPX 360 2023: The most important cyber security event of the year!
CPX 360 2023: The most important cyber security event of the year!EXECUTIVE SUMMARY: The premiere cyber security event of the year awaits you. Registration for CPX...
Massive Twitter data leak investigated by EU privacy watchdog
Massive Twitter data leak investigated by EU privacy watchdogThe Irish Data Protection Commission (DPC) has launched an inquiry following last month's news reports of a massive Twitter...
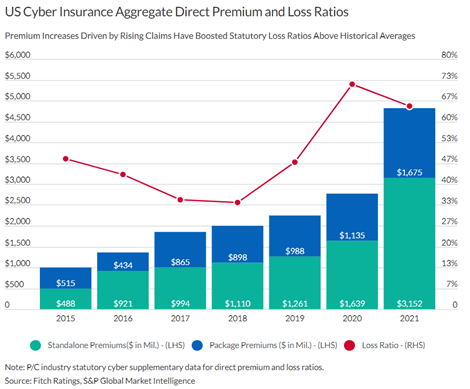
A prevention-first security strategy reduces insurance claims
A prevention-first security strategy reduces insurance claimsKeely Wilkins is an Evangelist with the Office of the CTO as well as a Pre-Sales Security Engineer in Virginia....