Operation Power Off: 50 DDoS-services taken offline in international crackdownLaw enforcement agencies in the United States, UK, Netherlands, Poland, and Germany have brought down the most...
Day: December 22, 2022
Smashing Security podcast #302: Lensa AI, and a dog called Bob
Smashing Security podcast #302: Lensa AI, and a dog called BobDrug dealers come unstuck while using the Encrochat encrypted-messaging app, and we put the Lensa AI’s...
Trojaned Windows Installer Targets Ukraine
Trojaned Windows Installer Targets UkraineMandiant is reporting on a trojaned Windows installer that targets Ukrainian users. The installer was left on various torrent sites, presumably ensnaring...
Backup saves the day after crime author loses laptop in blizzard
Backup saves the day after crime author loses laptop in blizzardCelebrated crime author Ann Cleeves turned to Twitter this week, desperate for help. The reason? The...
Microsoft approved and digitally-signed malicious drivers used in ransomware attacks
Microsoft approved and digitally-signed malicious drivers used in ransomware attacksMicrosoft has warned that malicious hackers were able to get the software giant to digitally sign their...
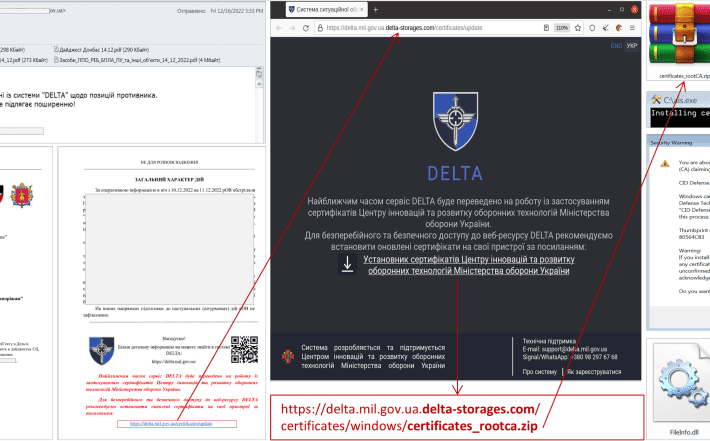
UAC-0142 APT targets Ukraine’s Delta military intelligence program
UAC-0142 APT targets Ukraine’s Delta military intelligence programUkraine’s CERT-UA revealed the national Delta military intelligence program has been targeted with a malware-based attack. On December 17,...
To Secure the Software Supply Chain, Start with a SBOM
To Secure the Software Supply Chain, Start with a SBOMHaving a SBOM can reduce the “fog of war” and enable businesses to assess risk and impact...
Ukraine Intercepting Russian Soldiers’ Cell Phone Calls
Ukraine Intercepting Russian Soldiers’ Cell Phone CallsThey’re using commercial phones, which go through the Ukrainian telecom network: “You still have a lot of soldiers bringing cellphones...
Data breach at Social Blade confirmed. Hacker offers to sell database on underground website
Data breach at Social Blade confirmed. Hacker offers to sell database on underground websiteSocial media analytics service Social Blade has confirmed that it is investigating a...
3 Trends Shaping the Future Of Attack Surface Management
3 Trends Shaping the Future Of Attack Surface ManagementBy David Monnier, Team Cymru Fellow Will your organization become the next big cyberattack reported in the news?...
Critical Microsoft Code-Execution Vulnerability
Critical Microsoft Code-Execution VulnerabilityA critical code-execution vulnerability in Microsoft Windows was patched in September. It seems that researchers just realized how serious it was (and is):...
FateGrab/StealDeal Detection: Phishing Attacks by the UAC-0142 Group Against Ukrainian Government Entities Targeting DELTA Users
FateGrab/StealDeal Detection: Phishing Attacks by the UAC-0142 Group Against Ukrainian Government Entities Targeting DELTA Users Phishing attacks on Ukrainian state bodies spreading diverse malware strains have...
Smashing Security podcast #303: Secret Roomba snaps, Christmas cab scams, and the future of AI
Smashing Security podcast #303: Secret Roomba snaps, Christmas cab scams, and the future of AIBeware your Roomba's roving eye, the Finns warn of AI threats around...
A Local Solution to A Global Problem: Why Cyber Security Operation Centres Should Be UK Based
A Local Solution to A Global Problem: Why Cyber Security Operation Centres Should Be UK BasedWhere you choose to base your SOC physically is a crucial...
67K Customers Had Their Data Leaked in a Credential Stuffing Attack over DraftKings
67K Customers Had Their Data Leaked in a Credential Stuffing Attack over DraftKings67,995 customers of the sports betting company DraftKings had their personal data exposed in...
New Microsoft Exchange Exploit Used by Ransomware Gang to Breach Servers
New Microsoft Exchange Exploit Used by Ransomware Gang to Breach ServersA group of threat actors known as Play ransomware is using a new exploit in Microsoft...
Ring Digital Cameras Used in a Widespread Police Prank
Ring Digital Cameras Used in a Widespread Police PrankThe US Department of Justice (DoJ) announced that two men were charged with hacking into Ring digital cameras...
What Is Identity Governance and Administration (IGA)?
What Is Identity Governance and Administration (IGA)?Identity Governance and Administration, also known as IGA in cybersecurity or identity security, is a strategic approach to security that...
Russian Hackers Targeted Petroleum Refinery in NATO Country
Russian Hackers Targeted Petroleum Refinery in NATO CountryDuring the ongoing Russo-Ukrainian conflict, the Russian-linked Gamaredon group attempted to break into a large petroleum refining company within...
Agenda Ransomware Steals Sensitive Data from Critical Infrastructure
Agenda Ransomware Steals Sensitive Data from Critical InfrastructureThis year, many ransomware-as-a-service groups, including Agenda and Qilin, have developed versions of their ransomware in Rust. Like its...
Raspberry Robin Worm Uses Fake Malware to Evade Detection
Raspberry Robin Worm Uses Fake Malware to Evade DetectionThreat actors started using fake malware to confuse researchers and avoid being analyzed by detection systems. The new...
Corsair Bug in Keyboard Causes Typing Without User’s Consent
Corsair Bug in Keyboard Causes Typing Without User’s ConsentA firmware bug in Corsair’s K100 keyboards, rather than malware, is causing previously entered text to be auto-typed...
BrandPost: Managing Risk Would be Easier if It Weren’t for People
BrandPost: Managing Risk Would be Easier if It Weren’t for PeopleBusinesses are as much at risk from human error as from threat actors. Typos, configuration errors,...
What Is System Hardening?
What Is System Hardening?In the cyber world, one of the most important things you can do is harden your system. System hardening is a key step...
Recently Discovered RisePro Malware Is a Vidar Stealer Derivative
Recently Discovered RisePro Malware Is a Vidar Stealer DerivativeRisePro, a new information-stealing malware, was recently observed on a dark web forum run by Russian cybercriminals. Since...
The Anatomy of Pharming and How to Prevent It
The Anatomy of Pharming and How to Prevent It‘Pharming’ is a type of cyberattack that uses malicious software to redirect traffic from a seemingly legitimate website...
GodFather, a New Android Banking Trojan
GodFather, a New Android Banking TrojanGodFather, a new Android banking trojan, is affecting over 400 banking and crypto apps and is active in 16 countries. The...
What Is Credential Management?
What Is Credential Management?If you’re responsible for keeping a high-profile organization or government institution with a large user base and workforce secure, your responsibilities are complicated....
Threat Actors Use Search Engine Ads for Ransomware and Phishing Attacks
Threat Actors Use Search Engine Ads for Ransomware and Phishing AttacksThreat actors use search engines to advertise websites that spread ransomware or steal login credentials. The...
Nation-state Hacking – What You Need to Know
Nation-state Hacking – What You Need to KnowNation-state actors operate at a higher level than regular cybercriminals, posing critical challenges to cybersecurity. Today we’ll explore their...