Hacking group abuses antivirus software to launch LODEINFO malwareThe Chinese Cicada hacking group, tracked as APT10, was observed abusing security software to install a new version...
Month: November 2022
3 simple, strategic measures to stop phishing attacks
3 simple, strategic measures to stop phishing attacksEXECUTIVE SUMMARY: To celebrate Cyber Security Awareness Month, CyberTalk.org is publishing dedicated blogs throughout October. Each week, we are...
Instagram confirms outage following stream of user suspensions
Instagram confirms outage following stream of user suspensionsInstagram users are currently experiencing issues signing into their accounts, some of them being notified their accounts have been...
A global CISO’s secrets to high-performing security awareness initiatives
A global CISO’s secrets to high-performing security awareness initiativesJonathan Fischbein is the Chief Information Security Officer for cyber security vendor Check Point Software. He has more...
Hackers selling access to 576 corporate networks for $4 million
Hackers selling access to 576 corporate networks for $4 millionA new report shows that hackers are selling access to 576 corporate networks worldwide for a total...
Security benefits of Hyperautomation
Security benefits of HyperautomationDevin Partida writes about cyber security and technology. She is also the Editor-in-Chief of ReHack.com. Hyperautomation is the next step in digital transformation. This...
Chegg sued by FTC after suffering four data breaches within 3 years
Chegg sued by FTC after suffering four data breaches within 3 yearsThe U.S. Federal Trade Commission (FTC) has sued education technology company Chegg after it exposed the sensitive information...
Single chip transfers the entire internet’s traffic in a second
Single chip transfers the entire internet’s traffic in a secondEXECUTIVE SUMMARY: A single chip has managed a transfer of over a petabit-per-second, according to new research...
NSA shares supply chain security tips for software suppliers
NSA shares supply chain security tips for software suppliersNSA, CISA, and the Office of the Director of National Intelligence (ODNI) have shared a new set of...
The art of cyber threat intelligence: How to identify & fight potential attackers
The art of cyber threat intelligence: How to identify & fight potential attackersDave is an experienced security engineer and business professional, leading Guardian Digital in providing...
Mozilla Firefox fixes freezes caused by new Windows 11 feature
Mozilla Firefox fixes freezes caused by new Windows 11 featureMozilla has fixed a known issue causing the Firefox web browser to freeze when copying text on...
How to become a revenue-generating CIO
How to become a revenue-generating CIOEXECUTIVE SUMMARY: Businesses are increasingly looking to IT leaders as C-suite entrepreneurs who can structure innovative efforts and scale emerging ideas....
States Spent Millions On Deloitte’s ‘Anti-Fraud’ Covid Unemployment Systems. They Suffered Billions In Fraud.
States Spent Millions On Deloitte’s ‘Anti-Fraud’ Covid Unemployment Systems. They Suffered Billions In Fraud.Contenido de la entradaLeer másProofpoint News Feed
Addressing the cyber security talent shortage: APAC and beyond
Addressing the cyber security talent shortage: APAC and beyondEXECUTIVE SUMMARY: Globally, in the last year, the cyber security workforce has seen the greatest growth in the...
Click or treat? Scary good security tips for a happy Halloween!
Click or treat? Scary good security tips for a happy Halloween!EXECUTIVE SUMMARY: Halloween is a widely celebrated holiday in the U.S. Ninety-three percent of Americans intend...
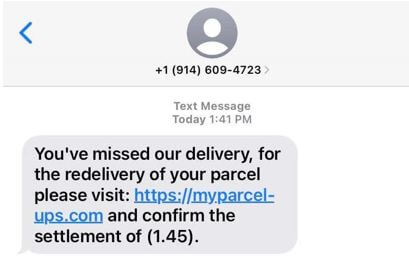
SMiShing: Short, sweet and evil
SMiShing: Short, sweet and evilBy Miguel Angulo, Channel Engineer and Evangelist, Check Point Software. Have you ever received a text message from someone you don’t know,...
Ordinary web access request or command to malware?
Ordinary web access request or command to malware?Cranefly group unleashes nasty little technique using Microsoft Internet Information Services (IIS) logs A threat group that targets corporate...
India’s Home Ministry cracks down on predatory lending apps following suicides
India's Home Ministry cracks down on predatory lending apps following suicidesLocal media say they're China backed, Ministry only mentions organized crime India's Home Ministry has asked...
Education tech giant gets an F for security after sensitive info on 40 million users stolen
Education tech giant gets an F for security after sensitive info on 40 million users stolenChegg it out: Four blunders in four years Sloppy data security...
The White House’s global ransomware summit couldn’t come at a better time
The White House's global ransomware summit couldn't come at a better timeAs cyber threats ramp up, businesses and organizations will be hoping for more than platitudes...
Unofficial fix emerges for Windows bug abused to infect home PCs with ransomware
Unofficial fix emerges for Windows bug abused to infect home PCs with ransomwareBroken code signature? LGTM, says Microsoft OS A cybersecurity firm has issued another unofficial...
German cops arrest student suspected of running infamous dark-web souk
German cops arrest student suspected of running infamous dark-web soukDeutschland im Deep Web destroyed A 22-year-old student German federal police believe to be the administrator of...
Education tech giant gets an F for security after sensitive info on 40 million users stolen
Education tech giant gets an F for security after sensitive info on 40 million users stolenChegg it out: Four blunders in four years Sloppy data security...
The White House’s global ransomware summit couldn’t come at a better time
The White House's global ransomware summit couldn't come at a better timeAs cyber threats ramp up, businesses and organizations will be hoping for more than platitudes...
Ordinary web access request or command to malware?
Ordinary web access request or command to malware?Cranefly group unleashes nasty little technique using Microsoft Internet Information Services (IIS) logs A threat group that targets corporate...
Unofficial fix emerges for Windows bug abused to infect home PCs with ransomware
Unofficial fix emerges for Windows bug abused to infect home PCs with ransomwareBroken code signature? LGTM, says Microsoft OS A cybersecurity firm has issued another unofficial...
India’s Home Ministry cracks down on predatory lending apps following suicides
India's Home Ministry cracks down on predatory lending apps following suicidesLocal media say they're China backed, Ministry only mentions organized crime India's Home Ministry has asked...
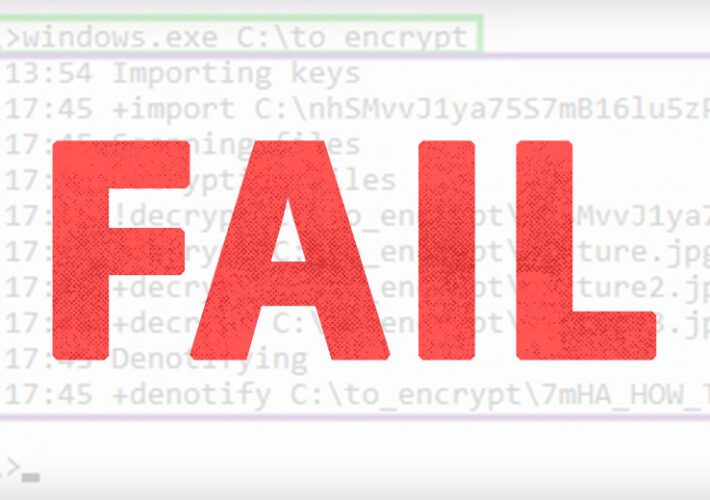
Ransomware: ‘Amateur’ Tactics Lead Fewer Victims to Pay
Ransomware: 'Amateur' Tactics Lead Fewer Victims to PayCriminals Shooting Themselves in the Foot With Faulty Decryptors, Re-ExtortionMany ransomware-wielding attackers - including big-name groups - have been...
North Korea Disguising Android Malware as Legitimate Apps
North Korea Disguising Android Malware as Legitimate AppsApps Masquerade as Google Security Plug-In and Document ViewerNorth Korean state hacking group Kimsuky is developing Android malware targeted...
German cops arrest student suspected of running infamous dark-web souk
German cops arrest student suspected of running infamous dark-web soukDeutschland im Deep Web destroyed A 22-year-old student German federal police believe to be the administrator of...