Single chip transfers the entire internet’s traffic in a secondEXECUTIVE SUMMARY: A single chip has managed a transfer of over a petabit-per-second, according to new research...
Month: November 2022
NSA shares supply chain security tips for software suppliers
NSA shares supply chain security tips for software suppliersNSA, CISA, and the Office of the Director of National Intelligence (ODNI) have shared a new set of...
The art of cyber threat intelligence: How to identify & fight potential attackers
The art of cyber threat intelligence: How to identify & fight potential attackersDave is an experienced security engineer and business professional, leading Guardian Digital in providing...
Mozilla Firefox fixes freezes caused by new Windows 11 feature
Mozilla Firefox fixes freezes caused by new Windows 11 featureMozilla has fixed a known issue causing the Firefox web browser to freeze when copying text on...
How to become a revenue-generating CIO
How to become a revenue-generating CIOEXECUTIVE SUMMARY: Businesses are increasingly looking to IT leaders as C-suite entrepreneurs who can structure innovative efforts and scale emerging ideas....
States Spent Millions On Deloitte’s ‘Anti-Fraud’ Covid Unemployment Systems. They Suffered Billions In Fraud.
States Spent Millions On Deloitte’s ‘Anti-Fraud’ Covid Unemployment Systems. They Suffered Billions In Fraud.Contenido de la entradaLeer másProofpoint News Feed
Addressing the cyber security talent shortage: APAC and beyond
Addressing the cyber security talent shortage: APAC and beyondEXECUTIVE SUMMARY: Globally, in the last year, the cyber security workforce has seen the greatest growth in the...
Click or treat? Scary good security tips for a happy Halloween!
Click or treat? Scary good security tips for a happy Halloween!EXECUTIVE SUMMARY: Halloween is a widely celebrated holiday in the U.S. Ninety-three percent of Americans intend...
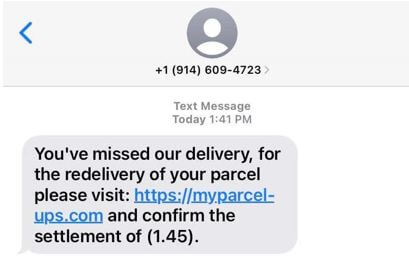
SMiShing: Short, sweet and evil
SMiShing: Short, sweet and evilBy Miguel Angulo, Channel Engineer and Evangelist, Check Point Software. Have you ever received a text message from someone you don’t know,...
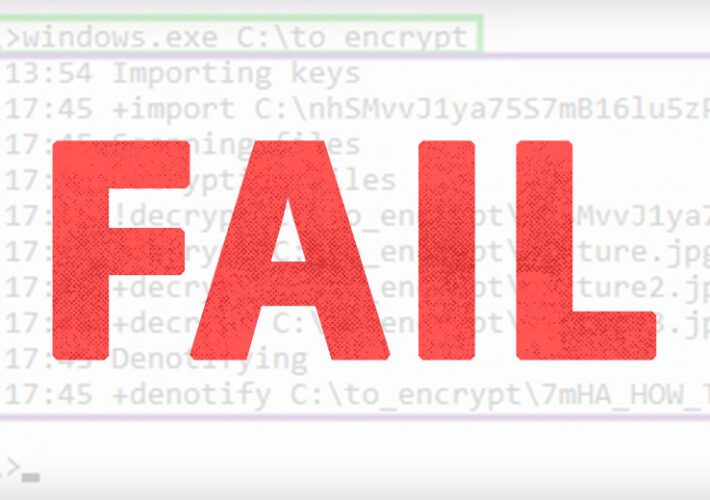
Ransomware: ‘Amateur’ Tactics Lead Fewer Victims to Pay
Ransomware: 'Amateur' Tactics Lead Fewer Victims to PayCriminals Shooting Themselves in the Foot With Faulty Decryptors, Re-ExtortionMany ransomware-wielding attackers - including big-name groups - have been...
North Korea Disguising Android Malware as Legitimate Apps
North Korea Disguising Android Malware as Legitimate AppsApps Masquerade as Google Security Plug-In and Document ViewerNorth Korean state hacking group Kimsuky is developing Android malware targeted...
Honeywell’s James DeLuccia on Product Security vs IT Defense
Honeywell's James DeLuccia on Product Security vs IT DefenseConsistency Is the Objective in IT Security, But Product Security Must Be FlexibleOrganizations expect the IT security landscape...
Second Health Entity Reports Breach Tied to Meta Pixel Use
Second Health Entity Reports Breach Tied to Meta Pixel UseNorth Carolina Organization Also Facing Pending Privacy Lawsuit Related to PixelA second healthcare entity is self-reporting its...
Cyberattack Hits German Copper Manufacturing Giant
Cyberattack Hits German Copper Manufacturing GiantAurubis Shuts Down IT Systems at Various Productions LocationsOne of the world's largest copper smelters disclosed it underwent a cyberattack, stating...