Chinese-Manufactured Cameras to Be Removed from UK Sensitive Government SitesOn November 24, 2022, the UK Parliament decided the ban from sensitive government sites of all surveillance...
Day: November 28, 2022
Belgian Police Under Fire After Major Ransomware Leak
Belgian Police Under Fire After Major Ransomware LeakCrime reports dating back 15 years are made publicLeer másCrime reports dating back 15 years are made public
US FCC bans the import of electronic equipment from Chinese firms
US FCC bans the import of electronic equipment from Chinese firmsThe U.S. Federal Communications Commission announced it will completely ban the import of electronic equipment from...
Spyware posing as VPN apps – Week in security with Tony Anscombe
Spyware posing as VPN apps – Week in security with Tony AnscombeThe Bahamut APT group distributes at least eight malicious apps that pilfer victims' data and...
Threat Actors #Giveaway: 5.4 Million Twitter User Data Exposed
Threat Actors #Giveaway: 5.4 Million Twitter User Data Exposed5,485,635 Twitter user records that contain personal data were released on November 24th, for free, on a hacker...
Security Affairs newsletter Round 395
Security Affairs newsletter Round 395A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in...
Ransomware gang targets Belgian municipality, hits police instead
Ransomware gang targets Belgian municipality, hits police insteadThe Ragnar Locker ransomware gang has published stolen data from what they thought was the municipality of Zwijndrecht, but turned out...
RansomBoggs Ransomware hit several Ukrainian entities, experts attribute it to Russia
RansomBoggs Ransomware hit several Ukrainian entities, experts attribute it to RussiaSeveral Ukrainian organizations were hit by Russia-based RansomBoggs Ransomware in the last week, ESET reports. Researchers...
Domain Hijacking vs DNS Poisoning: Do You Know the Difference?
Domain Hijacking vs DNS Poisoning: Do You Know the Difference?Domain hijacking and DNS poisoning are two methods used by threat actors to perform a DNS spoofing...
For Cybercriminals, the Game is On and They’re Playing to Win
For Cybercriminals, the Game is On and They’re Playing to WinWhy Football Clubs Need to Up their Cyber Defence By Ravi Pather, VP, Europe and Middle...
Weekly Update 323
Weekly Update 323Finally, after nearly 3 long years, I'm back in Norway! We're here at last, leaving our sunny paradise for a winter wonderland. It's almost...
Windows 11 is getting a VPN status indicator in the taskbar
Windows 11 is getting a VPN status indicator in the taskbarWindows 11 may soon show a system tray indicator notifying when your computer is connected to...
Ransomware Gang in Belgium Attacks Police Instead Of Belgian Municipality
Ransomware Gang in Belgium Attacks Police Instead Of Belgian MunicipalityThe Ragnar Locker ransomware gang published data that they thought was from the Zwijndrecht municipality in Belgium,...
Four Tips for Health-Care Providers to Stay Cyber Secure
Four Tips for Health-Care Providers to Stay Cyber SecureBy Aaron Sandeen, CEO and Co-Founder, CSW The number of attacks aimed at the health-care industry has increased...
Going ‘Passwordless’ Is Not a Simple Process and Should Not Be Rushed
Going ‘Passwordless’ Is Not a Simple Process and Should Not Be RushedBusinesses need to scope, plan, and implement with care By Alex Tupman, CEO, Espria Organisations...
BatLoader Malware Detection: Evasive Downloader on the Rise
BatLoader Malware Detection: Evasive Downloader on the Rise Security experts warn of the notorious stealthy malware dubbed BatLoader, which has been increasingly infecting instances worldwide over...
14 PCI Compliance security best practices for your business
14 PCI Compliance security best practices for your businessLooking for more information on PCI Compliance security? Read 14 security best practices for PCI (Payment Card Industry)...
The Cybersecurity Industry is Broken
The Cybersecurity Industry is BrokenThe security industry must transform. Tom Corn, Senior Vice President, Security Products at VMware, knows where to begin. Cloud can be the...
Operation Elaborate – UK police text 70,000 people thought to have fallen victim to iSpoof bank fraudsters
Operation Elaborate – UK police text 70,000 people thought to have fallen victim to iSpoof bank fraudstersUK police are texting 70,000 people who they believe have...
Security At The Forefront: A Spotlight On Zero Trust
Security At The Forefront: A Spotlight On Zero TrustVMware commissioned Forrester Consulting to evaluate how organizations are working to ensure a strong security posture via Zero...
How CIOs Should Think About Blockchain
How CIOs Should Think About BlockchainFrom a security standpoint, blockchain represents an opportunity to reinforce the foundation of your business, but it’s important to look at...
CIO Essential Guidance: CISO Security Threat landscape
CIO Essential Guidance: CISO Security Threat landscapeDespite massive spend to protect enterprise digital assets, security breaches are still on the rise. The disconnect between the level...
What is Antivirus and What Does It Really Protect?
What is Antivirus and What Does It Really Protect? Authored by Dennis Pang What is antivirus? That’s a good question. What does it really protect? That’s...
McAfee Personal Data Cleanup: Your Partner in Living a More Private Online Life
McAfee Personal Data Cleanup: Your Partner in Living a More Private Online Life Do yourself a favor: Open a new browser tab and head to your...
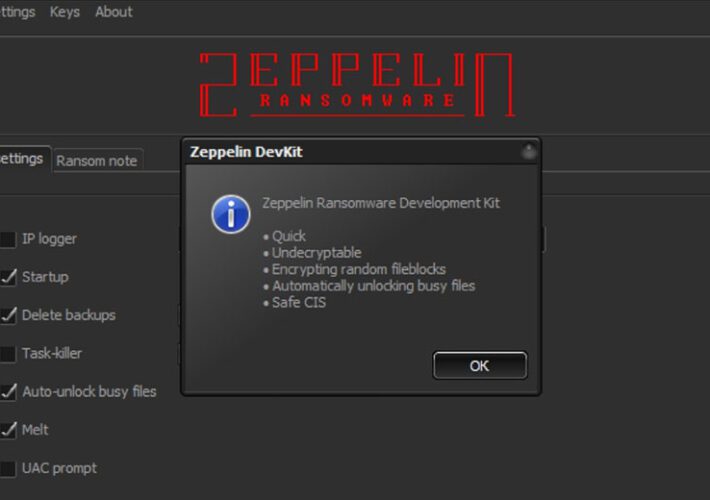
Zeppelin Ransomware Proceeds Punctured by Crypto Workaround
Zeppelin Ransomware Proceeds Punctured by Crypto WorkaroundCryptography Errors Exploited by Researchers for Recovery Without Paying a RansomAs the U.S. celebrates Thanksgiving, let's give thanks for this...
Solving The Cybersecurity Talent Crisis Demands Public-Private Sector Collaboration
Solving The Cybersecurity Talent Crisis Demands Public-Private Sector CollaborationContenido de la entradaLeer másProofpoint News Feed
Top 5 confidential computing uses in healthcare
Top 5 confidential computing uses in healthcareBig data meets private data in a perfect storm for healthcare. Confidential computing providers say they’ll make the cloud safer...
SocGholish finds success through novel email techniques
SocGholish finds success through novel email techniquesContenido de la entradaLeer másProofpoint News Feed
Cybercrime Carnage: Cryptocurrency-Targeting Attacks Abound
Cybercrime Carnage: Cryptocurrency-Targeting Attacks AboundFrom Cryptojacking to Exchange Hacks to Scam Token Contracts, Innovation AboundsWhile the cybercrime story for 2022 has yet to be fully written,...
GUEST ESSAY: What ‘self-sovereign-identities’ are all about — and how SSIs can foster public good
GUEST ESSAY: What ‘self-sovereign-identities’ are all about — and how SSIs can foster public goodGovernment assistance can be essential to individual wellbeing and economic stability. This...