Firms Spend $1197 Per Employee Yearly to Address Cyber-AttacksThe data excludes compliance fines, ransomware costs and losses from non-operational processesLeer másThe data excludes compliance fines, ransomware...
Day: November 22, 2022
Latest insights on APT activity – Week in security with Tony Anscombe
Latest insights on APT activity – Week in security with Tony AnscombeWhat have some of the world's most notorious APT groups been up to lately? A...
US Takes Down Domains Used in ‘Pig Butchering’ Cryptocurrency Scheme
US Takes Down Domains Used in 'Pig Butchering' Cryptocurrency SchemeThe US Attorney's Office for the Eastern District of Virginia made the announcement on MondayLeer másThe US...
AirAsia Falls Victim to Daixin Ransomware Gang
AirAsia Falls Victim to Daixin Ransomware GangThe Malaysian low-cost airline belonging to AirAsia had some of its data leaked by the cybercrime group known as Daixin Team,...
Expert published PoC exploit code for macOS sandbox escape flaw
Expert published PoC exploit code for macOS sandbox escape flawA researcher published details and proof-of-concept (PoC) code for High-Severity macOS Sandbox escape vulnerability tracked as CVE-2022-26696....
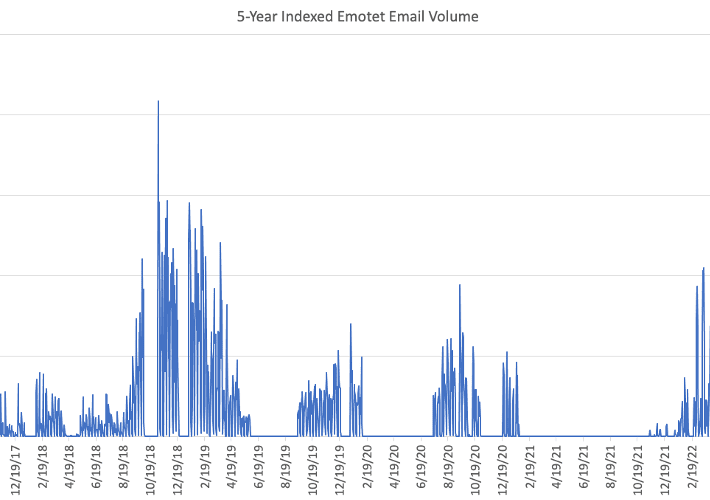
Emotet is back and delivers payloads like IcedID and Bumblebee
Emotet is back and delivers payloads like IcedID and BumblebeeThe Emotet malware is back and experts warn of a high-volume malspam campaign delivering payloads like IcedID...
PII Breach Discovered on Bahmni Hospital Management System
PII Breach Discovered on Bahmni Hospital Management SystemOn September 19th, 2022, a breach affecting Bahmni company was discovered. The Bahmni Hospital Management System was breached exposing...
Two Estonian citizens arrested in $575M cryptocurrency fraud scheme
Two Estonian citizens arrested in $575M cryptocurrency fraud schemeTwo Estonian citizens were arrested in Tallinn for allegedly running a $575 million cryptocurrency fraud scheme. Two Estonian...
Apps with Over 3 Million Downloads Leak Algolia API Keys
Apps with Over 3 Million Downloads Leak Algolia API KeysResearchers found 1,550 mobile apps that were leaking Algolia API credentials, putting private internal services and user...
Apps with over 3 million installs leak ‘Admin’ search API keys
Apps with over 3 million installs leak 'Admin' search API keysResearchers discovered 1,550 mobile apps leaking Algolia API keys, risking the exposure of sensitive internal services...
Aurora Stealer Malware is becoming a prominent threat in the cybercrime ecosystem
Aurora Stealer Malware is becoming a prominent threat in the cybercrime ecosystemResearchers warn of threat actors employing a new Go-based malware dubbed Aurora Stealer in attacks...
Sensitive Data From Nuclear Facilities Leaked on Dark Web
Sensitive Data From Nuclear Facilities Leaked on Dark WebCybercrime activities targeting the nuclear industry worldwide have risen during the past eight months, according to Cyble, a...
Google releases 165 YARA rules to detect Cobalt Strike attacks
Google releases 165 YARA rules to detect Cobalt Strike attacksThe Google Cloud Threat Intelligence team has open-sourced YARA Rules and a VirusTotal Collection of indicators of...
Blockchain Security: Can You Trust This Technology?
Blockchain Security: Can You Trust This Technology?Is Blockchain Technology Really Secure? By Alexandr Khomich, CEO at Andersen Blockchain is considered one of the most […] The...
What Is DNS Scavenging?
What Is DNS Scavenging?DNS scavenging is the process of removing stale DNS records, usually used together with DNS aging in order to free up space and...
Cybersecurity, Data Management and Insufficient Systems Listed as Top Concerns for Risk Professionals
Cybersecurity, Data Management and Insufficient Systems Listed as Top Concerns for Risk ProfessionalsDiligent is the global leader in modern governance providing SaaS solutions across governance, risk,...
SOC Prime’s Cyber Monday Deal 2022: Get Bonus Sigma Rules of Your Choice & Unlimited Hunting Capabilities
SOC Prime’s Cyber Monday Deal 2022: Get Bonus Sigma Rules of Your Choice & Unlimited Hunting Capabilities We are thrilled to announce our Cyber Monday promotion...
Continuous Exposure Management: Flipping the Script on Cybersecurity
Continuous Exposure Management: Flipping the Script on CybersecurityBy Brett Kelsey, CEO, Reveald Hackers recently exploited flaws in the Binance blockchain to steal $570 million and […]...
Google Chrome extension used to steal cryptocurrency, passwords
Google Chrome extension used to steal cryptocurrency, passwordsAn information-stealing Google Chrome browser extension named 'VenomSoftX' is being deployed by Windows malware to steal cryptocurrency and clipboard...
Earth Preta aka Mustang Panda Attack Detection: Abused Fake Google Accounts in Spear-Phishing Campaigns Targeting Governments Worldwide
Earth Preta aka Mustang Panda Attack Detection: Abused Fake Google Accounts in Spear-Phishing Campaigns Targeting Governments Worldwide The infamous China-linked Earth Preta (aka Mustang Panda, Bronze...
Ouch! Ransomware gang says it won’t attack AirAsia again due to the “chaotic organisation” and sloppy security of hacked company’s network
Ouch! Ransomware gang says it won’t attack AirAsia again due to the “chaotic organisation” and sloppy security of hacked company’s networkThe Daixin ransomware gang has given...
Black Friday deal: Get 50% off Malwarebytes Premium, Privacy VPN
Black Friday deal: Get 50% off Malwarebytes Premium, Privacy VPNMalwarebytes' Black Friday deal is now live, offering a 50% discount on the Malwarebytes Premium antivirus + Malwarebytes Privacy VPN bundle...
Apple’s Device Analytics Can Identify iCloud Users
Apple’s Device Analytics Can Identify iCloud UsersResearchers claim that supposedly anonymous device analytics information can identify users: On Twitter, security researchers Tommy Mysk and Talal Haj...
Hackers steal $300,000 in DraftKings credential stuffing attack
Hackers steal $300,000 in DraftKings credential stuffing attackSports betting company DraftKings said today that it would make whole customers affected by a credential stuffing attack that led to...
Attackers bypass Coinbase and MetaMask 2FA via TeamViewer, fake support chat
Attackers bypass Coinbase and MetaMask 2FA via TeamViewer, fake support chatA crypto-stealing phishing campaign is underway to bypass multi-factor authentication and gain access to accounts on...
9 VOIP security best practices to consider for your business
9 VOIP security best practices to consider for your businessIs VOIP secure? Can VOIP be hacked? Learn about why VOIP security is important and the best...
Microsoft Defender protects Mac and Linux from malicious websites
Microsoft Defender protects Mac and Linux from malicious websitesNow that attackers can phish employees on any device and try to extract credentials, endpoint protection has to...
Aurora infostealer malware increasingly adopted by cybergangs
Aurora infostealer malware increasingly adopted by cybergangsCybercriminals are increasingly turning to a new Go-based information stealer named 'Aurora' to steal sensitive information from browsers and cryptocurrency apps,...
How to minimize security risks: Follow these best practices for success
How to minimize security risks: Follow these best practices for successTo reduce security threats within your organization, you must prioritize security risk management. Here are some...
Two Estonians arrested for running $575M crypto Ponzi scheme
Two Estonians arrested for running $575M crypto Ponzi schemeTwo Estonian nationals were arrested in Tallinn, Estonia, on Sunday after being indicted in the U.S. for running a massive...