Researchers release exploit details for Backstage pre-auth RCE bugOlder versions of the Spotify Backstage development portal builder are vulnerable to a critical (CVSS score: 9.8) unauthenticated...
Day: November 16, 2022
MFA Fatigue attacks are putting your organization at risk
MFA Fatigue attacks are putting your organization at riskA common threat targeting businesses is MFA fatigue attacks—a technique where a cybercriminal attempts to gain access to a...
Windows 10 KB5020030 preview update released with ten improvements
Windows 10 KB5020030 preview update released with ten improvementsMicrosoft has released this month's optional KB5020030 Preview cumulative update for all editions of Windows 10 20H2, 21H1,...
Google to roll out Privacy Sandbox on Android 13 starting early 2023
Google to roll out Privacy Sandbox on Android 13 starting early 2023Google announced today that they will begin rolling out the Privacy Sandbox system on a...
Top 5 email newsletters that will make you smarter in the digital age
Top 5 email newsletters that will make you smarter in the digital ageContributed by George Mack, Content Marketing Manager, Check Point Software. Every day, we are...
The Harris Center for Mental Health & IDD ISO shares perspectives on cyber security
The Harris Center for Mental Health & IDD ISO shares perspectives on cyber securityWes Farris is the Director of Information Security and Enterprise Architecture at The...
What are eavesdropping attacks? Everything you need to know
What are eavesdropping attacks? Everything you need to knowEXECUTIVE SUMMARY: Eavesdropping attacks are easy to execute and exploit inherently insecure or vulnerable networks. Are your network...
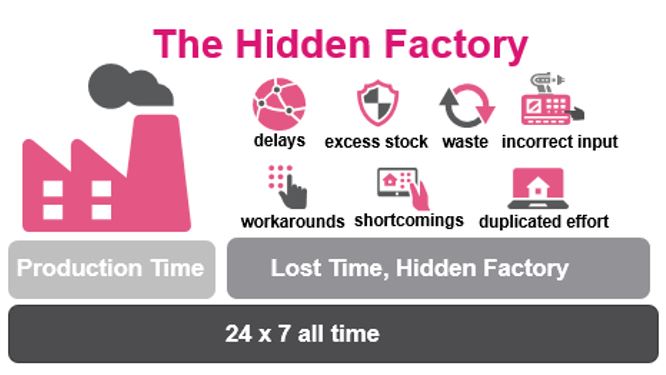
How addressing “Hidden Factory” can boost the transition to “Green Factory”
How addressing “Hidden Factory” can boost the transition to “Green Factory”Antoinette Hodes is a Check Point Solution Architect for the EMEA region and an Evangelist with...
North Korean hackers target European orgs with updated malware
North Korean hackers target European orgs with updated malwareNorth Korean hackers are using a new version of the DTrack backdoor to attack organizations in Europe and...
10 secrets for successful digital transformations
10 secrets for successful digital transformationsEXECUTIVE SUMMARY: Digitize to survive and thrive? Digital transformations account for 40% of all business technology spending, and the digital transformation...
How Do Recent CISA Directives Affect Private Firms?
How Do Recent CISA Directives Affect Private Firms?Complying with BOD 23-01 mandates can help prevent security breaches, compliance fines, and litigation damagesLeer másDataBreachToday.com RSS SyndicationComplying with...
FDA Updates Medical Device Cyber Response Playbook
FDA Updates Medical Device Cyber Response PlaybookNew Edition Emphasizes Regional, Cross-Functional Response PreparednessFederal officials released updated guidance for medical device cybersecurity incidents, including ransomware, as cyberattacks...
Twitter Two-Factor Authentication Has a Vulnerability
Twitter Two-Factor Authentication Has a VulnerabilityHackers Gain Path to Potential Account Takeover by Turning Off SMS Second FactorTwitter accounts that use SMS for two-factor authentication are...
Medibank chief defends company’s security processes amid shareholder anger at AGM
Medibank chief defends company’s security processes amid shareholder anger at AGMQuestions about cyber-attack dominate meeting as company says it is contacting 480,000 customers whose health claims...
Arrest of Ukrainian in Cybercrime Case Shows Patience Pays
Arrest of Ukrainian in Cybercrime Case Shows Patience PaysSuspect in Jabberzeus Banking Malware Gang Nabbed in GenevaThe arrest of a Ukrainian national long wanted on cybercrime...
US FTC Delays Safeguards Rule Deadlines by 6 Months
US FTC Delays Safeguards Rule Deadlines by 6 MonthsRegulators Heed Concerns Over Lack of Qualified Personnell in Private SectorThe U.S. Federal Trade Commission pushed until June...