Patch your iPhone now against mystery Mail crash bugiOS 16.0.3 has been pushed out by Apple, and my advice is that you should install it.Leer másGraham...
Month: October 2022
8 questions to ask yourself before getting a home security camera
8 questions to ask yourself before getting a home security cameraAs each new smart home device may pose a privacy and security risk, do you know...
Most Dangerous Ransomware Groups in 2022 You Should Know About
Most Dangerous Ransomware Groups in 2022 You Should Know AboutRansomware is a major threat that costs businesses, corporations, and infrastructure operators billions of dollars every year....
ESET Threat Report T2 2022
ESET Threat Report T2 2022A view of the T2 2022 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and...
Internet outages hit Ukraine following Russian missile strikes
Internet outages hit Ukraine following Russian missile strikesUkraine has seen internet outages this week following renewed missile attacks from Russian forces. With a combination of power...
How Underground Groups Use Stolen Identities and Deepfakes
How Underground Groups Use Stolen Identities and DeepfakesThe growing appearance of deepfake attacks is significantly reshaping the threat landscape. These fakes brings attacks such as business...
The need to change cybersecurity for the next generation
The need to change cybersecurity for the next generationHealthy habits that are instilled and nurtured at an early age bring lifelong benefits – the same applies...
Smashing Security podcast #293: Massive crypto bungle, and the slave scammers
Smashing Security podcast #293: Massive crypto bungle, and the slave scammersA couple unexpectedly find $10.5 million in their cryptocurrency account, and in Cambodia people are being...
New Ursnif Variant Likely Shifting Focus to Ransomware and Data Theft
New Ursnif Variant Likely Shifting Focus to Ransomware and Data TheftThe Ursnif malware has become the latest malware to shed its roots as a banking trojan...
Key takeaways from ESET Threat Report T2 2022 – Week in security with Tony Anscombe
Key takeaways from ESET Threat Report T2 2022 – Week in security with Tony AnscombeA look back on the key trends and developments that shaped the...
Brazilian Police Arrest Suspected Member of Lapsus$ Hacking Group
Brazilian Police Arrest Suspected Member of Lapsus$ Hacking GroupThe Federal Police of Brazil on Wednesday announced it had arrested an individual for purported links to the...
Not All Sandboxes Are for Children: How to Secure Your SaaS Sandbox
Not All Sandboxes Are for Children: How to Secure Your SaaS SandboxWhen creating a Sandbox, the mindset tends to be that the Sandbox is considered a...
DNS Best Practices: A Quick Guide for Organizations
DNS Best Practices: A Quick Guide for OrganizationsNowadays, the traditional on-site computing architecture is moved to remote facilities that are normally under the management of a...
These 16 Clicker Malware Infected Android Apps Were Downloaded Over 20 Million Times
These 16 Clicker Malware Infected Android Apps Were Downloaded Over 20 Million TimesAs many as 16 malicious apps with over 20 million cumulative downloads have been...
Steam account hacked? Here’s how to get it back
Steam account hacked? Here’s how to get it backWhat are the warning signs that someone has hijacked your Steam account? Here is what to look for...
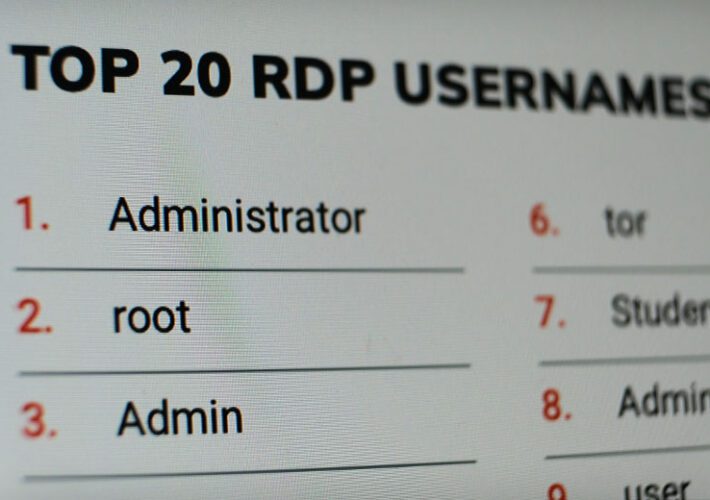
Why Are We So Stupid About Passwords? SSH and RDP Edition
Why Are We So Stupid About Passwords? SSH and RDP EditionPoor Credential Hygiene Leaves Remote Services at Risk of Brute Force AttacksIf remote access to corporate...
OldGremlin Ransomware Targeted Over a Dozen Russian Entities in Multi-Million Scheme
OldGremlin Ransomware Targeted Over a Dozen Russian Entities in Multi-Million SchemeA Russian-speaking ransomware group dubbed OldGremlin has been attributed to 16 malicious campaigns aimed at entities...
Stronger Cloud Security in Azure Functions Using Custom Cloud Container
Stronger Cloud Security in Azure Functions Using Custom Cloud ContainerIn this entry, we discuss how developers can use custom cloud container image and the distroless approach...
Hackers Using New Version of FurBall Android Malware to Spy on Iranian Citizens
Hackers Using New Version of FurBall Android Malware to Spy on Iranian CitizensThe Iranian threat actor known as Domestic Kitten has been attributed to a new...
Microsoft Confirms Server Misconfiguration Led to 65,000+ Companies’ Data Leak
Microsoft Confirms Server Misconfiguration Led to 65,000+ Companies' Data LeakMicrosoft this week confirmed that it inadvertently exposed information related to thousands of customers following a security...
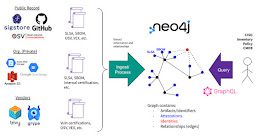
Google Launches GUAC Open Source Project to Secure Software Supply Chain
Google Launches GUAC Open Source Project to Secure Software Supply ChainGoogle on Thursday announced that it's seeking contributors to a new open source initiative called Graph...
POLONIUM targets Israel with Creepy malware
POLONIUM targets Israel with Creepy malwareESET researchers analyzed previously undocumented custom backdoors and cyberespionage tools deployed in Israel by the POLONIUM APT group The post POLONIUM...
Hackers Started Exploiting Critical “Text4Shell” Apache Commons Text Vulnerability
Hackers Started Exploiting Critical "Text4Shell" Apache Commons Text VulnerabilityWordPress security company Wordfence on Thursday said it started detecting exploitation attempts targeting the newly disclosed flaw in...
A Quick Look at the “Strengthening America’s Cybersecurity” Initiative
A Quick Look at the "Strengthening America's Cybersecurity" InitiativeAcknowledging that you have a problem is the first step to addressing the problem in a serious way....
What Is A Keylogger? Definition, Types, Examples and Prevention
What Is A Keylogger? Definition, Types, Examples and PreventionA keylogger is a software or hardware component that records everything typed on your computer’s keyboard. The term...
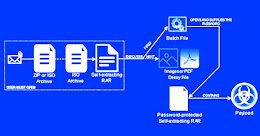
Emotet Botnet Distributing Self-Unlocking Password-Protected RAR Files to Drop Malware
Emotet Botnet Distributing Self-Unlocking Password-Protected RAR Files to Drop MalwareThe notorious Emotet botnet has been linked to a new wave of malspam campaigns that take advantage of password-protected...
Multiple Campaigns Exploit VMware Vulnerability to Deploy Crypto Miners and Ransomware
Multiple Campaigns Exploit VMware Vulnerability to Deploy Crypto Miners and RansomwareA now-patched vulnerability in VMware Workspace ONE Access has been observed being exploited to deliver both...
Why Ransomware in Education on the Rise and What That Means for 2023
Why Ransomware in Education on the Rise and What That Means for 2023The breach of LA Unified School District (LAUSD) highlights the prevalence of password vulnerabilities,...
10 common Zelle scams – and how to avoid them
10 common Zelle scams – and how to avoid themFraudsters use various tactics to separate people from their hard-earned cash on Zelle. Here’s how to keep...
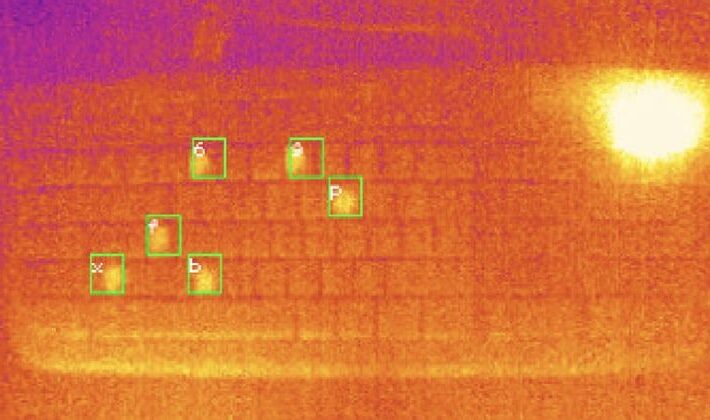
Heat left by users’ fingertips could help hackers crack passwords, researchers claim
Heat left by users’ fingertips could help hackers crack passwords, researchers claimBoffins at the University of Glasgow, in Scotland, have developed a system which they claim...