How Card Skimming Disproportionally Affects Those Most In NeedWhen people banking in the United States lose money because their payment card got skimmed at an ATM,...
Day: October 31, 2022
Sigma2SaveLives: Equip Yourself with Curated Sigma Rules While Donating to Save Lives in Ukraine
Sigma2SaveLives: Equip Yourself with Curated Sigma Rules While Donating to Save Lives in Ukraine On April 4, 2022, SOC Prime launched Sigma2SaveLives charity subscription with 100%...
Microsoft releases out-of-band updates to fix OneDrive crashes
Microsoft releases out-of-band updates to fix OneDrive crashesMicrosoft has released out-of-band updates today to address a known issue causing OneDrive and OneDrive for Business to crash...
Single chip transfers the entire internet’s traffic in a second
Single chip transfers the entire internet’s traffic in a secondEXECUTIVE SUMMARY: A single chip has managed a transfer of over a petabit-per-second, according to new research...
How To Protect Against The 83 million Cyber Attacks Detected In 2021
How To Protect Against The 83 million Cyber Attacks Detected In 2021The 4 Basic Cybersecurity Practices Experts Say Prevent Most Attacks By CyberLock Defense, Lockton Affinity...
Threat Actors Target AWS EC2 Workloads to Steal Credentials
Threat Actors Target AWS EC2 Workloads to Steal CredentialsWe found malicious samples attempting to steal Amazon Elastic Compute Cloud (EC2) Workloads' access keys and tokens via...
Raising the Alarm on DDoS Attacks
Raising the Alarm on DDoS AttacksBy Ivan Shefrin, Executive Director for Managed Security Services at Comcast Business Many organizations underappreciate the risk of […] The post...
Twilio reveals hackers compromised its systems a month earlier than previously thought
Twilio reveals hackers compromised its systems a month earlier than previously thoughtCloud communications firm Twilio reveals that it fell victim to a voice phishing attack in...
Apple Only Commits to Patching Latest OS Version
Apple Only Commits to Patching Latest OS VersionPeople have suspected this for a while, but Apple has made it official. It only commits to fully patching...
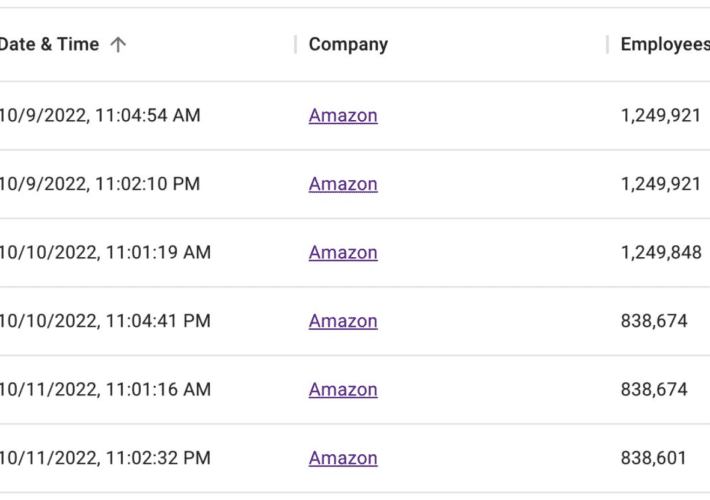
Battle with Bots Prompts Mass Purge of Amazon, Apple Employee Accounts on LinkedIn
Battle with Bots Prompts Mass Purge of Amazon, Apple Employee Accounts on LinkedInOn October 10, 2022, there were 576,562 LinkedIn accounts that listed their current employer...
Announcing GUAC, a great pairing with SLSA (and SBOM)!
Announcing GUAC, a great pairing with SLSA (and SBOM)!Posted by Brandon Lum, Mihai Maruseac, Isaac Hepworth, Google Open Source Security Team Supply chain security is at...
Cranefly uses new communication technique in attack campaigns
Cranefly uses new communication technique in attack campaignsA threat actor dubbed "Cranefly" uses a new technique for its communications on infected targets. The post Cranefly uses...
Why Employers Should Embrace Competency-Based Learning in Cybersecurity
Why Employers Should Embrace Competency-Based Learning in CybersecurityThere is a growing movement toward increasing the use of competency and skills-based education and hiring practices in both...
GUEST ESSAY: A roadmap to achieve a better balance of network security and performance
GUEST ESSAY: A roadmap to achieve a better balance of network security and performanceHere’s a frustrating reality about securing an enterprise network: the more closely you...
Online age-verification system could create ‘honeypot’ of personal data and pornography-viewing habits, privacy groups warn
Online age-verification system could create ‘honeypot’ of personal data and pornography-viewing habits, privacy groups warnAs the government develops online safety guidelines, digital rights groups says any...
Can a new form of cryptography solve the internet’s privacy problem?
Can a new form of cryptography solve the internet’s privacy problem?Techniques which allow the sharing of data whilst keeping it secure may revolutionise fields from healthcare...
Mobiles are inherently insecure, which might be a surprise to British politicians | Dan Sabbagh
Mobiles are inherently insecure, which might be a surprise to British politicians | Dan SabbaghWe may never know just what happened with Liz Truss’s mobile, but...
Government urged to investigate report Liz Truss’s phone was hacked
Government urged to investigate report Liz Truss’s phone was hackedBreach discovered during Tory leadership in summer but details suppressed, the Mail on Sunday reports The government...
‘Buying bad’: the black market where access to hacked Australian data can cost just $500
‘Buying bad’: the black market where access to hacked Australian data can cost just $500Some sites that mediate the sale of hacked data use Reddit-style upvoting...
Cyber-attack on Australian defence contractor may have exposed private communications between ADF members
Cyber-attack on Australian defence contractor may have exposed private communications between ADF membersDataset from communications platform ForceNet containing up to 40,000 records may be compromised after...
Ministers creating ‘wild west’ conditions with use of personal phones
Ministers creating ‘wild west’ conditions with use of personal phonesUnsecured mobiles, email accounts and WhatsApp chats could pose national security risk, intelligence experts warn Ministers risk...
Espionage Hackers Use Microsoft IIS to Plant Malware
Espionage Hackers Use Microsoft IIS to Plant MalwareHacking Group Uses a New Backdoor Called DanfuanThreat actors are using Internet Information Services - Microsoft's extensible web server...