Five Steps to Mitigate the Risk of Credential ExposureEvery year, billions of credentials appear online, be it on the dark web, clear web, paste sites, or...
Day: October 4, 2022
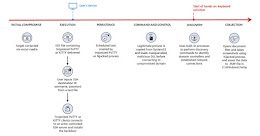
Researchers Uncover Covert Attack Campaign Targeting Military Contractors
Researchers Uncover Covert Attack Campaign Targeting Military ContractorsA new covert attack campaign singled out multiple military and weapons contractor companies with spear-phishing emails to trigger a...
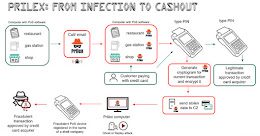
Brazilian Prilex Hackers Resurfaced With Sophisticated Point-of-Sale Malware
Brazilian Prilex Hackers Resurfaced With Sophisticated Point-of-Sale MalwareA Brazilian threat actor known as Prilex has resurfaced after a year-long operational hiatus with an advanced and complex malware to...
WARNING: New Unpatched Microsoft Exchange Zero-Day Under Active Exploitation
WARNING: New Unpatched Microsoft Exchange Zero-Day Under Active ExploitationSecurity researchers are warning of previously undisclosed flaws in fully patched Microsoft Exchange servers being exploited by malicious...
Microsoft Confirms 2 New Exchange Zero-Day Flaws Being Used in the Wild
Microsoft Confirms 2 New Exchange Zero-Day Flaws Being Used in the WildMicrosoft officially disclosed it investigating two zero-day security vulnerabilities impacting Exchange Server 2013, 2016, and...
North Korean Hackers Weaponizing Open-Source Software in Latest Cyber Attacks
North Korean Hackers Weaponizing Open-Source Software in Latest Cyber AttacksA "highly operational, destructive, and sophisticated nation-state activity group" with ties to North Korea has been weaponizing...
Cyber Attacks Against Middle East Governments Hide Malware in Windows Logo
Cyber Attacks Against Middle East Governments Hide Malware in Windows LogoAn espionage-focused threat actor has been observed using a steganographic trick to conceal a previously undocumented...
New Malware Campaign Targeting Job Seekers with Cobalt Strike Beacons
New Malware Campaign Targeting Job Seekers with Cobalt Strike BeaconsA social engineering campaign leveraging job-themed lures is weaponizing a years-old remote code execution flaw in Microsoft...
Why Organisations Need Both EDR and NDR for Complete Network Protection
Why Organisations Need Both EDR and NDR for Complete Network ProtectionEndpoint devices like desktops, laptops, and mobile phones enable users to connect to enterprise networks and...
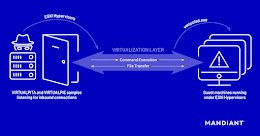
New Malware Families Found Targeting VMware ESXi Hypervisors
New Malware Families Found Targeting VMware ESXi HypervisorsThreat actors have been found deploying never-before-seen post-compromise implants in VMware's virtualization software to seize control of infected systems...
CISA Warns of Hackers Exploiting Critical Atlassian Bitbucket Server Vulnerability
CISA Warns of Hackers Exploiting Critical Atlassian Bitbucket Server VulnerabilityThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added a recently disclosed critical flaw impacting Atlassian's Bitbucket...
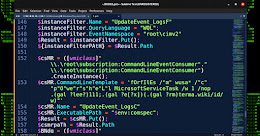
State-Sponsored Hackers Likely Exploited MS Exchange 0-Days Against ~10 Organizations
State-Sponsored Hackers Likely Exploited MS Exchange 0-Days Against ~10 OrganizationsMicrosoft on Friday disclosed that a single activity group in August 2022 achieved initial access and breached...
Pay What You Want for This Collection of White Hat Hacking Courses
Pay What You Want for This Collection of White Hat Hacking CoursesWhether you relish a mental challenge or fancy a six-figure paycheck, there are many good...
Ex-NSA Employee Arrested for Trying to Sell U.S. Secrets to a Foreign Government
Ex-NSA Employee Arrested for Trying to Sell U.S. Secrets to a Foreign GovernmentA former U.S. National Security Agency (NSA) employee has been arrested on charges of...
Hackers Exploiting Dell Driver Vulnerability to Deploy Rootkit on Targeted Computers
Hackers Exploiting Dell Driver Vulnerability to Deploy Rootkit on Targeted ComputersThe North Korea-backed Lazarus Group has been observed deploying a Windows rootkit by taking advantage of...
Researchers Link Cheerscrypt Linux-Based Ransomware to Chinese Hackers
Researchers Link Cheerscrypt Linux-Based Ransomware to Chinese HackersThe recently discovered Linux-Based ransomware strain known as Cheerscrypt has been outed as a handiwork of a Chinese cyber...
Comm100 Chat Provider Hijacked to Spread Malware in Supply Chain Attack
Comm100 Chat Provider Hijacked to Spread Malware in Supply Chain AttackA threat actor likely with associations to China has been attributed to a new supply chain...
Optus Hack Exposes Data of Nearly 2.1 Million Australian Telecom Customers
Optus Hack Exposes Data of Nearly 2.1 Million Australian Telecom CustomersAustralian telecom giant Optus on Monday confirmed that nearly 2.1 million of its current and former...
BEC Scammer Gets 25-Year Jail Sentence for Stealing Over $9.5 Million
BEC Scammer Gets 25-Year Jail Sentence for Stealing Over $9.5 MillionA 46-year-old man in the U.S. has been sentenced to 25 years in prison after being...
CISA Orders Federal Agencies to Regularly Track Network Assets and Vulnerabilities
CISA Orders Federal Agencies to Regularly Track Network Assets and VulnerabilitiesThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a new Binding Operational Directive (BOD)...
ProxyNotShell – the New Proxy Hell?
ProxyNotShell – the New Proxy Hell?Nicknamed ProxyNotShell, a new exploit used in the wild takes advantage of the recently published Microsoft Server-Side Request Forgery (SSRF) vulnerability...
Back to Basics: Cybersecurity’s Weakest Link
Back to Basics: Cybersecurity's Weakest LinkA big promise with a big appeal. You hear that a lot in the world of cybersecurity, where you're often promised...
Researchers Report Supply Chain Vulnerability in Packagist PHP Repository
Researchers Report Supply Chain Vulnerability in Packagist PHP RepositoryResearchers have disclosed details about a now-patched high-severity security flaw in Packagist, a PHP software package repository, that...
Popular YouTube Channel Caught Distributing Malicious Tor Browser Installer
Popular YouTube Channel Caught Distributing Malicious Tor Browser InstallerA popular Chinese-language YouTube channel has emerged as a means to distribute a trojanized version of a Windows...
Russian Hacker Arrested in India for Reportedly Helping Students Cheat in JEE-Main Exam
Russian Hacker Arrested in India for Reportedly Helping Students Cheat in JEE-Main ExamIndia's Central Bureau of Investigation (CBI) on Monday disclosed that it has detained a...