London Police Arrested 17-Year-Old Hacker Suspected of Uber and GTA 6 BreachesThe City of London Police on Friday revealed that it has arrested a 17-year-old teenager...
Month: September 2022
Reflections in your glasses can leak information while you’re on a Zoom call
Reflections in your glasses can leak information while you’re on a Zoom callBespectacled video conferencing participants have more to worry about than if their hair is...
What Is Data Exfiltration? MITRE ATT&CK® Exfiltration Tactic | TA0010
What Is Data Exfiltration? MITRE ATT&CK® Exfiltration Tactic | TA0010 The process of stealing data from a corporate system is also known as exfiltration. MITRE ATT&CK®...
OpIran: Anonymous declares war on Teheran amid Mahsa Amini’s death
OpIran: Anonymous declares war on Teheran amid Mahsa Amini’s deathOpIran: Anonymous launched Operation Iran against Teheran due to the ongoing crackdown on dissent after Mahsa Amini’s...
Smashing Security podcast #290: Uber, Rockstar, and crystal balls
Smashing Security podcast #290: Uber, Rockstar, and crystal ballsResearchers reveal how your eyeglasses could be leaking secrets when you’re on video conferencing calls, we take a...
Air Force Upgrades Digital Modernization Strategy to “As a Service” Model
Air Force Upgrades Digital Modernization Strategy to "As a Service" ModelThe transition will be carried out through three procurements to be awarded before the end of...
Weekly Update 313
Weekly Update 313I came so close to skipping this week's video. I'm surrounded by family, friends and my amazing wife to be in only a couple...
How to have fun negotiating with a ransomware gang
How to have fun negotiating with a ransomware gangThe Financial Times has created an imaginative ransomware negotiation simulator which lets you imagine you’re in the hot...
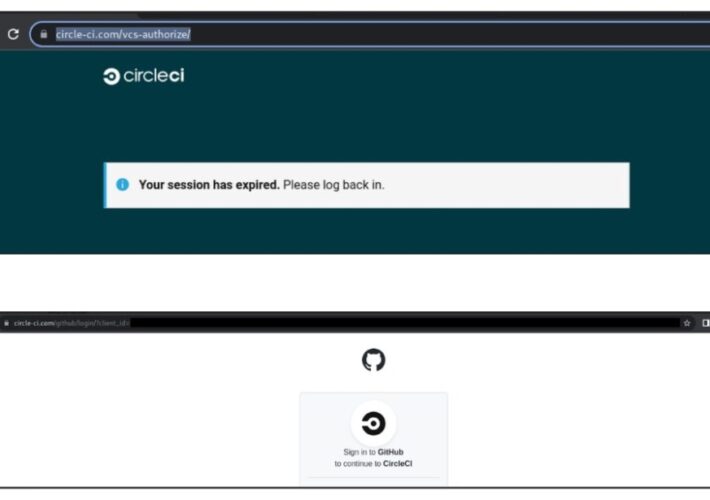
Attackers impersonate CircleCI platform to compromise GitHub accounts
Attackers impersonate CircleCI platform to compromise GitHub accountsThreat actors target GitHub users to steal credentials and two-factor authentication (2FA) codes by impersonating the CircleCI DevOps platform....
Avoiding the Risks of Ransomware Strikes in Life Sciences
Avoiding the Risks of Ransomware Strikes in Life SciencesBy Travis Tidwell, Business Development Lead, Rockwell Automation While Life Sciences companies have become even more important to...
Come to the National Information Security Conference in October, and see Smashing Security LIVE!
Come to the National Information Security Conference in October, and see Smashing Security LIVE!Between 5-7 October, I will be chairing the UK's National Information Security Conference...
Weekly Update 314
Weekly Update 314Wow, what a week! Of course there's lots of cyber / tech stuff in this week's update, but it was really only the embedded...
Building A Layered Plan for Battling Cybercrime
Building A Layered Plan for Battling CybercrimeBy Kimberly White, Senior Director, Fraud and Identity, LexisNexis® Risk Solutions As interactions with customers evolve over time, […] The...
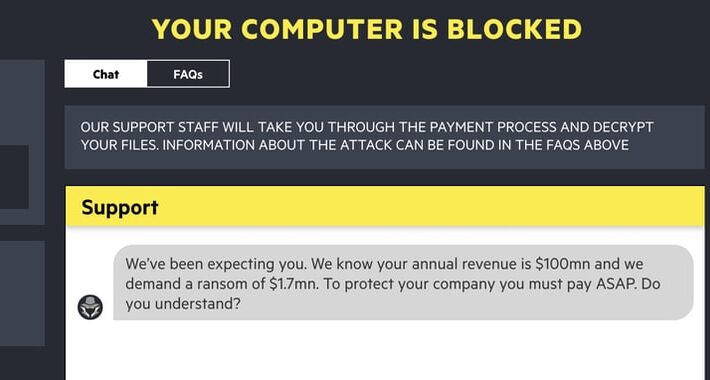
“Fake crypto millionaire” charged with alleged $1.7M cryptomining scam
“Fake crypto millionaire” charged with alleged $1.7M cryptomining scamA self-proclaimed cryptocurrency millionaire has been charged with multiple felonies for his alleged role in a scam that...
Prompt Injection/Extraction Attacks against AI Systems
Prompt Injection/Extraction Attacks against AI SystemsThis is an interesting attack I had not previously considered. The variants are interesting, and I think we’re just starting to...
Oxford teen arrested in UK on suspicion of hacking
Oxford teen arrested in UK on suspicion of hackingThe boy, who has not been named, was arrested as part of an investigation by the National Crime...
Leaking Screen Information on Zoom Calls through Reflections in Eyeglasses
Leaking Screen Information on Zoom Calls through Reflections in EyeglassesOkay, it’s an obscure threat. But people are researching it: Our models and experimental results in a...
Friday Squid Blogging: Another Giant Squid Washes Up on New Zealand Beach
Friday Squid Blogging: Another Giant Squid Washes Up on New Zealand BeachThis one has chewed-up tentacles. (Note that this is a different squid than the one...
Accused Russian RSOCKS Botmaster Arrested, Requests Extradition to U.S.
Accused Russian RSOCKS Botmaster Arrested, Requests Extradition to U.S.A 36-year-old Russian man recently identified by KrebsOnSecurity as the likely proprietor of the massive RSOCKS botnet has...
The top 20 cyber security movers and shakers 2022
The top 20 cyber security movers and shakers 2022Cyber Security Hub’s inaugural power list is live, profiling the achievements from cyber security leaders at Microsoft, Visa,...
How Often Should You Change Your Passwords?
How Often Should You Change Your Passwords? When it comes to passwords, most of us would love nothing more than to set it and forget it....
Protect Your Social Media Accounts from Hacks and Attacks
Protect Your Social Media Accounts from Hacks and Attacks Here’s to the hashtags, the likes, the followers, the DMs, and the LOLs—June 30th marks Social Media Day, a...
Windows 11 now warns when typing your password in Notepad, websites
Windows 11 now warns when typing your password in Notepad, websitesWindows 11 22H2 was just released, and with it comes a new security feature called Enhanced...
8 mistakes CIOs make and how to avoid them
8 mistakes CIOs make and how to avoid themFrom driving transformative change, to sharing insights into the political nature of the role, IT leaders and advisors...
Real Estate Phish Swallows 1,000s of Microsoft 365 Credentials
Real Estate Phish Swallows 1,000s of Microsoft 365 CredentialsContenido de la entradaLeer másProofpoint News Feed
Uber Ex-CSO’s Trial: Who’s Responsible for Breach Reporting?
Uber Ex-CSO's Trial: Who's Responsible for Breach Reporting?While Joe Sullivan Is Accused of Perpetrating Cover-Up, Where Should the Buck Stop?Should the now-former CSO of Uber have...
It’s 2022. Do You Know Where Your Old Hard Drives Are?
It's 2022. Do You Know Where Your Old Hard Drives Are?The latest edition of the ISMG Security Report discusses financial giant Morgan Stanley's failure to invest...
K28942395: OpenSSH vulnerability CVE-2018-15473
K28942395: OpenSSH vulnerability CVE-2018-15473OpenSSH vulnerability CVE-2018-15473 Security Advisory Security Advisory Description OpenSSH through 7.7 is prone to a user enumeration vulnerability due to not delaying bailout...
Malicious Apps With Millions of Downloads Found in Apple App Store, Google Play
Malicious Apps With Millions of Downloads Found in Apple App Store, Google PlayThe ongoing ad fraud campaign can be traced back to 2019, but recently expanded...
AFP investigates $1m ransom demand posted online for allegedly hacked Optus data
AFP investigates $1m ransom demand posted online for allegedly hacked Optus dataAttorney general Mark Dreyfus has been briefed by the privacy commissioner about hack and is...