Zyxel releases new NAS firmware to fix critical RCE vulnerabilityZyxel Corporation, the Taiwanese networking and data storage device maker, has issued a security advisory to warn...
Month: September 2022
Our Quest: Advancing Product Labels to Help Consumers Consider Cybersecurity
Our Quest: Advancing Product Labels to Help Consumers Consider CybersecurityFor many decades, consumers have relied on labels to help them make decisions about which products to...
FBI warns of Vice Society ransomware attacks on school districts
FBI warns of Vice Society ransomware attacks on school districtsFBI, CISA, and MS-ISAC warned today of U.S. school districts being increasingly targeted by the Vice Society ransomware group, with...
Minecraft is hackers’ favorite game title for hiding malware
Minecraft is hackers’ favorite game title for hiding malwareSecurity researchers have discovered that Minecraft is the most heavily abused game title by cybercriminals, who use it...
Moobot botnet is coming for your unpatched D-Link router
Moobot botnet is coming for your unpatched D-Link routerThe Mirai malware botnet variant known as 'MooBot' has re-emerged in a new attack wave that started early...
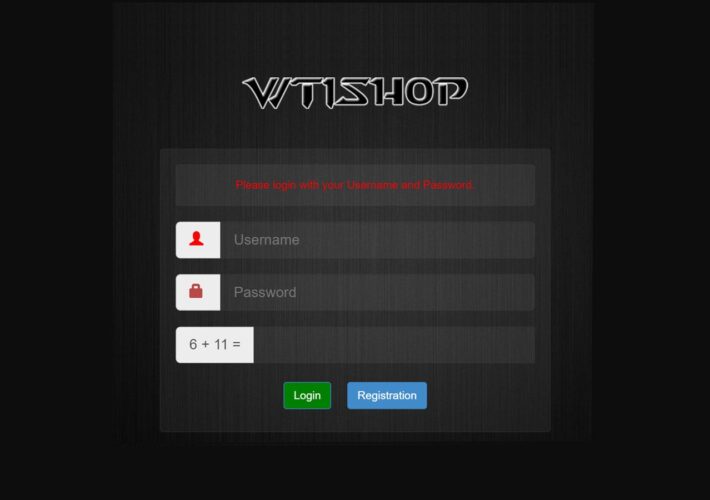
US seizes WT1SHOP market selling credit cards, credentials, and IDs
US seizes WT1SHOP market selling credit cards, credentials, and IDsAn international law enforcement operation has seized the website and domains for WT1SHOP, a criminal marketplace that...
Google: Former Conti cybercrime gang members now targeting Ukraine
Google: Former Conti cybercrime gang members now targeting UkraineGoogle says some former Conti cybercrime gang members, now part of a threat group tracked as UAC-0098, are...
Albania blames Iran for July cyberattack, severs diplomatic ties
Albania blames Iran for July cyberattack, severs diplomatic tiesAlbanian Prime Minister Edi Rama announced on Wednesday that the entire staff of the Embassy of the Islamic Republic of...
Ransomware gang’s Cobalt Strike servers DDoSed with anti-Russia messages
Ransomware gang's Cobalt Strike servers DDoSed with anti-Russia messagesSomeone is flooding Cobalt Strike servers operated by former members of the Conti ransomware gang with anti-Russian messages...
Are Default Passwords Hiding in Your Active Directory? Here’s how to check
Are Default Passwords Hiding in Your Active Directory? Here's how to checkOne of the biggest cybersecurity mistakes that an organization can make is failing to change...
New Iranian hacking group APT42 deploys custom Android spyware
New Iranian hacking group APT42 deploys custom Android spywareA new Iranian state-sponsored hacking group known as APT42 has been discovered using a custom Android malware to...
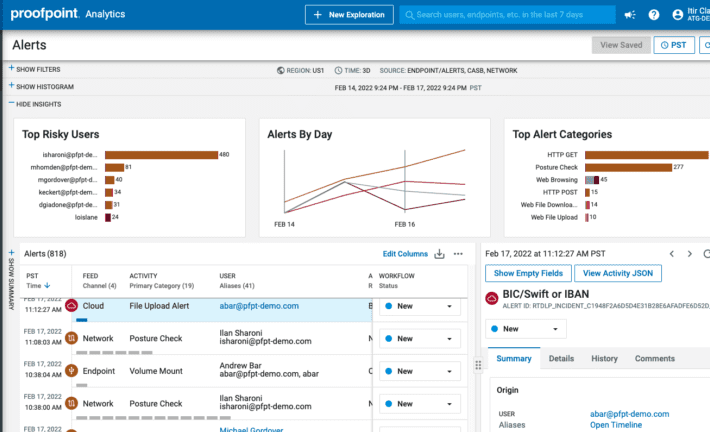
Summertime Blues: TA558 Ramps Up Attacks on Hospitality, Travel Sectors
Summertime Blues: TA558 Ramps Up Attacks on Hospitality, Travel SectorsContenido de la entradaLeer másProofpoint News Feed
Cloud attacks on the supply chain are a huge concern
Cloud attacks on the supply chain are a huge concernContenido de la entradaLeer másProofpoint News Feed
Cybercrime Group TA558 Ramps Up Email Attacks Against Hotels
Cybercrime Group TA558 Ramps Up Email Attacks Against HotelsContenido de la entradaLeer másProofpoint News Feed
Play Ransomware’s Attack Playbook Similar to that of Hive, Nokoyawa
Play Ransomware's Attack Playbook Similar to that of Hive, NokoyawaPlay is a new ransomware that takes a page out of Hive and Nokoyawa's playbook. The many...
Enhancing Cloud Security by Reducing Container Images Through Distroless Techniques
Enhancing Cloud Security by Reducing Container Images Through Distroless TechniquesWe analyzed the Distroless technique for reducing the size of container images and explored its capabilities to...
Cloud security: Increased concern about risks from partners, suppliers
Cloud security: Increased concern about risks from partners, suppliersContenido de la entradaLeer másProofpoint News Feed
Benefits of edge computing
Benefits of edge computingLearn more about how edge computing can reduce latency, boost performance and improve data security among other benefits. The post Benefits of edge...
Credential phishing prevention best practices
Credential phishing prevention best practicesCredential phishing prevention best practices can help your employees prevent cyber attacks that can harm your business. Information security is everyone’s job....
Best Data Security Solution | Proofpoint Information Protection
Best Data Security Solution | Proofpoint Information ProtectionContenido de la entradaLeer másProofpoint News Feed
200,000 North Face accounts hacked in credential stuffing attack
200,000 North Face accounts hacked in credential stuffing attackOutdoor apparel brand 'The North Face' was targeted in a large-scale credential stuffing attack that has resulted in...
Proofpoint Introduces a Smarter Way to Stay Compliant with New Intelligent Compliance Platform
Proofpoint Introduces a Smarter Way to Stay Compliant with New Intelligent Compliance PlatformContenido de la entradaLeer másProofpoint News Feed
Chinese hackers tied to attacks on South China Sea energy firms
Chinese hackers tied to attacks on South China Sea energy firmsContenido de la entradaLeer másProofpoint News Feed
Ukraine dismantles more bot farms spreading Russian disinformation
Ukraine dismantles more bot farms spreading Russian disinformationThe Cyber Department of the Ukrainian Security Service (SSU) dismantled two more bot farms that spread Russian disinformation on...
Three Sentenced in the UK for Selling Drugs on the Darkweb
Three Sentenced in the UK for Selling Drugs on the DarkwebThree drug dealers were sentenced to prison for producing and selling kilogram quantities of drugs on...
SilentHound – Quietly Enumerate An Active Directory Domain Via LDAP Parsing Users, Admins, Groups, Etc.
SilentHound – Quietly Enumerate An Active Directory Domain Via LDAP Parsing Users, Admins, Groups, Etc.Quietly enumerate an Active Directory Domain via LDAP parsing users, admins, groups,...
Chinese hackers target energy sector in Australia, South China Sea
Chinese hackers target energy sector in Australia, South China SeaContenido de la entradaLeer másProofpoint News Feed
Woman Heads to Prison for Hiring a "Hitman” on the Darkweb
Woman Heads to Prison for Hiring a "Hitman” on the DarkwebA Pelahatchie, Mississippi, woman will spend ten years in prison for trying to hire a hitman...
ESP32 Marauder v0.9.12 releases: suite of WiFi/Bluetooth offensive and defensive tools for the ESP32
ESP32 Marauder v0.9.12 releases: suite of WiFi/Bluetooth offensive and defensive tools for the ESP32ESP32 Marauder The ESP32 Marauder is a suite of WiFi/Bluetooth offensive and defensive...
The secret to managing deepfakes includes AI/DL & provenance
The secret to managing deepfakes includes AI/DL & provenanceKeely Wilkins is an Evangelist with the Office of the CTO as well as a Pre-Sales Security Engineer...