Classified NATO documents sold on darkweb after they were stolen from PortugalThreat actors claimed to have stolen classified NATO documents from the Armed Forces General Staff...
Month: September 2022
Our Statement of Condolence – Queen Elizabeth II – 1926 – 2022
Our Statement of Condolence - Queen Elizabeth II - 1926 - 2022We are deeply saddened by the passing of Her Majesty Queen Elizabeth II. We send...
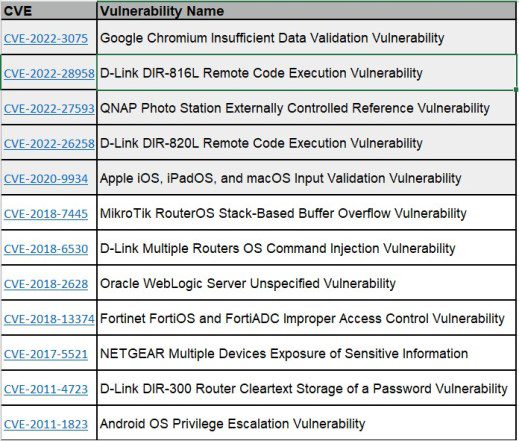
CISA adds 12 new flaws to its Known Exploited Vulnerabilities Catalog
CISA adds 12 new flaws to its Known Exploited Vulnerabilities CatalogCISA added 12 more security flaws to its Known Exploited Vulnerabilities Catalog including four D-Link vulnerabilities. The...
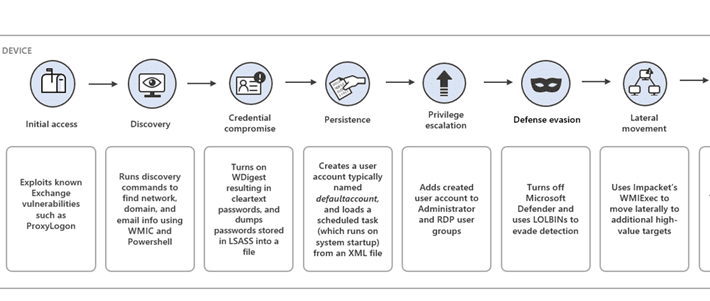
Iran-linked DEV-0270 group abuses BitLocker to encrypt victims’ devices
Iran-linked DEV-0270 group abuses BitLocker to encrypt victims’ devicesIran-linked APT group DEV-0270 (aka Nemesis Kitten) is abusing the BitLocker Windows feature to encrypt victims’ devices. Microsoft...
Experts warn of attacks exploiting zero-day in WordPress BackupBuddy plugin
Experts warn of attacks exploiting zero-day in WordPress BackupBuddy pluginThreat actors are exploiting a zero-day vulnerability in a WordPress plugin called BackupBuddy, Wordfence researchers warned. On September...
How To Design and Build Longer Lasting Drones
How To Design and Build Longer Lasting DronesOvercoming the limitations inherent in drone technology By Shaun Passley, Founder, Zenadrone Drones work. From search and rescue […]...
How To Increase User and Executive Participation In Security Awareness Training Programs
How To Increase User and Executive Participation In Security Awareness Training ProgramsBy Theo Zafirakos, CISO, Terranova Security The universal participation of an organization’s employees in security...
ZTNA and the Distributed Workforce: Hype vs. Reality
ZTNA and the Distributed Workforce: Hype vs. RealityBy Timothy Liu, CTO & Co-Founder, Hillstone Networks ZTNA, or zero-trust network access, seems to be one of […]...
Transacting in Person with Strangers from the Internet
Transacting in Person with Strangers from the InternetCommunities like Craigslist, OfferUp, Facebook Marketplace and others are great for finding low- or no-cost stuff that one can...
Summertime Blues: TA558 Ramps Up Attacks on Hospitality, Travel Sectors
Summertime Blues: TA558 Ramps Up Attacks on Hospitality, Travel SectorsContenido de la entradaLeer másProofpoint News Feed
Our Quest: Advancing Product Labels to Help Consumers Consider Cybersecurity
Our Quest: Advancing Product Labels to Help Consumers Consider CybersecurityFor many decades, consumers have relied on labels to help them make decisions about which products to...
Cloud attacks on the supply chain are a huge concern
Cloud attacks on the supply chain are a huge concernContenido de la entradaLeer másProofpoint News Feed
Cybercrime Group TA558 Ramps Up Email Attacks Against Hotels
Cybercrime Group TA558 Ramps Up Email Attacks Against HotelsContenido de la entradaLeer másProofpoint News Feed
CISA orders agencies to patch Chrome, D-Link flaws used in attacks
CISA orders agencies to patch Chrome, D-Link flaws used in attacksCISA has added 12 more security flaws to its list of bugs exploited in attacks, including...
Cloud security: Increased concern about risks from partners, suppliers
Cloud security: Increased concern about risks from partners, suppliersContenido de la entradaLeer másProofpoint News Feed
Best Data Security Solution | Proofpoint Information Protection
Best Data Security Solution | Proofpoint Information ProtectionContenido de la entradaLeer másProofpoint News Feed
GIFShell attack creates reverse shell using Microsoft Teams GIFs
GIFShell attack creates reverse shell using Microsoft Teams GIFsA new attack technique called 'GIFShell' allows threat actors to abuse Microsoft Teams for novel phishing attacks and...
Proofpoint Introduces a Smarter Way to Stay Compliant with New Intelligent Compliance Platform
Proofpoint Introduces a Smarter Way to Stay Compliant with New Intelligent Compliance PlatformContenido de la entradaLeer másProofpoint News Feed
Chinese hackers tied to attacks on South China Sea energy firms
Chinese hackers tied to attacks on South China Sea energy firmsContenido de la entradaLeer másProofpoint News Feed
Bumblebee malware adds post-exploitation tool for stealthy infections
Bumblebee malware adds post-exploitation tool for stealthy infectionsA new version of the Bumblebee malware loader has been spotted in the wild, featuring a new infection chain...
Warning of ransomware attacks on schools, here’s how to prepare…
Warning of ransomware attacks on schools, here’s how to prepare…EXECUTIVE SUMMARY: Earlier today, US agencies released a joint advisory pertaining to ransomware attacks on American schools....
Chinese hackers target energy sector in Australia, South China Sea
Chinese hackers target energy sector in Australia, South China SeaContenido de la entradaLeer másProofpoint News Feed
14 ways to secure business data, in layman’s language
14 ways to secure business data, in layman’s languageMazhar Hamayun is a cyber security professional with over 20 years of hands-on technology and leadership experience. At...
Multi-Cloud Networking and Security Makes a Splash at VMware Explore 2022
Multi-Cloud Networking and Security Makes a Splash at VMware Explore 2022The cloud has taken over the way enterprises do everything, from data storage to application development....
Multi-cloud with Continuous Risk-driven Security and Compliance
Multi-cloud with Continuous Risk-driven Security and ComplianceWe reviewed Zero Trust in a series of blogs earlier this month. In this blog, we are discussing a new...
A Pragmatic Response to the Quantum Threat
A Pragmatic Response to the Quantum ThreatYou certainly don't need to panic, but you do need to form a plan to prepare for the post-quantum reality.Leer...
Darktrace Shares Plunge After Thoma Bravo Acquisition Falls Apart
Darktrace Shares Plunge After Thoma Bravo Acquisition Falls ApartNo agreement could be reached on terms of a firm offer, the provider of AI-based cybersecurity products says.Leer...
Report Highlights Prevalence of Software Supply Chain Risks
Report Highlights Prevalence of Software Supply Chain RisksMulticlient research report shows organizations are significantly increasing efforts to secure their supply chains in response to software supply...
EvilProxy Bypasses MFA by Capturing Session Cookies
EvilProxy Bypasses MFA by Capturing Session CookiesThe latest ISMG Security Report discusses a new phishing-as-a-service toolkit designed to bypass multi-factor authentication, the decision by Lloyd's of...
Multi-Cloud Networking and Security Makes a Splash at VMware Explore 2022
Multi-Cloud Networking and Security Makes a Splash at VMware Explore 2022The cloud has taken over the way enterprises do everything, from data storage to application development....