Report: The state of secure identity 2022A new report from Okta has found that credential stuffing as a means of breaching Customer Identity and Access Management...
Month: September 2022
Authorized Push Payments Surge to 75% of Banking Fraud
Authorized Push Payments Surge to 75% of Banking FraudSocial engineering tactics bear fruit for digital scammersLeer másSocial engineering tactics bear fruit for digital scammers
You never walk alone: The SideWalk backdoor gets a Linux variant
You never walk alone: The SideWalk backdoor gets a Linux variantESET researchers have uncovered another tool in the already extensive arsenal of the SparklingGoblin APT group:...
Former Broadcom engineer gets eight months in prison for trade secrets theft
Former Broadcom engineer gets eight months in prison for trade secrets theftPeter Kisang Kim admitted to stealing Broadcom data related to its Trident family of network...
Cisco Event Response: September 2022 Semiannual Cisco IOS XR Software Security Advisory Bundled Publication
Cisco Event Response: September 2022 Semiannual Cisco IOS XR Software Security Advisory Bundled PublicationContenido de la entradaLeer másCisco Event Responses
SparklingGoblin deploys new Linux backdoor – Week in security, special edition
SparklingGoblin deploys new Linux backdoor – Week in security, special editionESET Research first spotted this variant of the SideWalk backdoor in the network of a Hong...
Third‑party cookies: How they work and how to stop them from tracking you across the web
Third‑party cookies: How they work and how to stop them from tracking you across the webCross-site tracking cookies have a bleak future but can still cause...
Rising to the challenges of secure coding – Week in security with Tony Anscombe
Rising to the challenges of secure coding – Week in security with Tony AnscombeThe news seems awash this week with reports of both Microsoft and Apple...
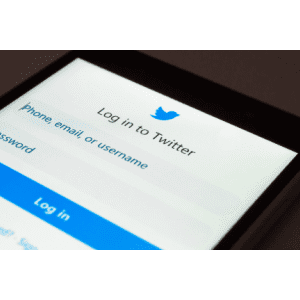
Twitter Password Reset Bug Exposed User Accounts
Twitter Password Reset Bug Exposed User AccountsSocial media firm fixes issue that left sessions openLeer másSocial media firm fixes issue that left sessions open
Multi-factor authentication fatigue attacks are on the rise: How to defend against them
Multi-factor authentication fatigue attacks are on the rise: How to defend against themCredential compromise has been one of the top causes for network security breaches for...
Can your iPhone be hacked? What to know about iOS security
Can your iPhone be hacked? What to know about iOS securityHere are some of the most common ways that an iPhone can be compromised with malware,...
D&O insurance not yet a priority despite criminal trial of Uber’s former CISO
D&O insurance not yet a priority despite criminal trial of Uber’s former CISOThe trial of former Uber CISO Joe Sullivan marks the first time a cybersecurity...
Critical Remote Hack Flaws Found in Dataprobe’s Power Distribution Units
Critical Remote Hack Flaws Found in Dataprobe's Power Distribution UnitsThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday released an industrial control systems (ICS) advisory...
Product Review: Stellar Cyber Open XDR Platform
Product Review: Stellar Cyber Open XDR PlatformAlmost every vendor, from email gateway companies to developers of threat intelligence platforms, is positioning themselves as an XDR player....
S3 Ep100: Browser-in-the-Browser – how to spot an attack [Audio + Text]
S3 Ep100: Browser-in-the-Browser – how to spot an attack [Audio + Text]Latest episode - listen now! Cosmic rockets, zero-days, spotting cybercrooks, and unlocking the DEADBOLT...Leer másNaked...
Why Zero Trust Should be the Foundation of Your Cybersecurity Ecosystem
Why Zero Trust Should be the Foundation of Your Cybersecurity EcosystemFor cybersecurity professionals, it is a huge challenge to separate the “good guys” from the “villains”....
Serious Security: Browser-in-the-browser attacks – watch out for windows that aren’t!
Serious Security: Browser-in-the-browser attacks – watch out for windows that aren’t!Simple but super-sneaky - use a picture of a browser, and convince people it's real...Leer másNaked...
U.S. Adds 2 More Chinese Telecom Firms to National Security Threat List
U.S. Adds 2 More Chinese Telecom Firms to National Security Threat ListThe U.S. Federal Communications Commission (FCC) has added Pacific Network Corp, along with its subsidiary...
Record DDoS Attack with 25.3 Billion Requests Abused HTTP/2 Multiplexing
Record DDoS Attack with 25.3 Billion Requests Abused HTTP/2 MultiplexingCybersecurity company Imperva has disclosed that it mitigated a distributed denial-of-service (DDoS) attack with a total of...
Hackers Targeting Unpatched Atlassian Confluence Servers to Deploy Crypto Miners
Hackers Targeting Unpatched Atlassian Confluence Servers to Deploy Crypto MinersA now-patched critical security flaw affecting Atlassian Confluence Server that came to light a few months ago...
LastPass source code breach – incident response report released
LastPass source code breach – incident response report releasedWondering how you'd handle a data breach report if the worst happened to you? Here's a useful example.Leer...
Over 39,000 Unauthenticated Redis Instances Found Exposed on the Internet
Over 39,000 Unauthenticated Redis Instances Found Exposed on the InternetAn unknown attacker targeted tens of thousands of unauthenticated Redis servers exposed on the internet in an...
S3 Ep100.5: Uber breach – an expert speaks [Audio + Text]
S3 Ep100.5: Uber breach – an expert speaks [Audio + Text]Chester Wisniewski on what we can learn from Uber: "Just because a big company didn't have...
UBER HAS BEEN HACKED, boasts hacker – how to stop it happening to you
UBER HAS BEEN HACKED, boasts hacker – how to stop it happening to youUber is all over the news for a widely-publicised data breach. We help...
Crypto Trading Firm Wintermute Loses $160 Million in Hacking Incident
Crypto Trading Firm Wintermute Loses $160 Million in Hacking IncidentIn what's the latest crypto heist to target the decentralized finance (DeFi) space, hackers have stolen digital...
15-Year-Old Unpatched Python Vulnerability Potentially Affects Over 350,000 Projects
15-Year-Old Unpatched Python Vulnerability Potentially Affects Over 350,000 ProjectsAs many as 350,000 open source projects are believed to be potentially vulnerable to exploitation as a result...
Interested in cybersecurity? Join us for Security SOS Week 2022!
Interested in cybersecurity? Join us for Security SOS Week 2022!Four one-on-one interviews with experts who are passionate about sharing their expertise with the community.Leer másNaked SecurityFour...
Our Quest: Advancing Product Labels to Help Consumers Consider Cybersecurity
Our Quest: Advancing Product Labels to Help Consumers Consider CybersecurityFor many decades, consumers have relied on labels to help them make decisions about which products to...
Microsoft 365 phishing attacks impersonate U.S. govt agencies
Microsoft 365 phishing attacks impersonate U.S. govt agenciesAn ongoing phishing campaign targeting U.S. government contractors has expanded its operation to push higher-quality lures and better-crafted documents....
American Airlines discloses data breach after employee email compromise
American Airlines discloses data breach after employee email compromiseAmerican Airlines has notified customers of a recent data breach after attackers compromised an undisclosed number of employee email accounts...