Government, Union-Themed Lures Used to Deliver Cobalt Strike PayloadsCisco Talos discovered the malicious campaign in August 2022Leer másCisco Talos discovered the malicious campaign in August 2022
Day: September 29, 2022
Researchers Uncover Covert Attack Campaign Targeting Military Contractors
Researchers Uncover Covert Attack Campaign Targeting Military ContractorsA new covert attack campaign singled out multiple military and weapons contractor companies with spear-phishing emails to trigger a...
Optus breach – Aussie telco told it will have to pay to replace IDs
Optus breach – Aussie telco told it will have to pay to replace IDsLicence compromised? Passport number burned? Need a new one? Who's going to pay?Leer...
WhatsApp “zero-day exploit” news scare – what you need to know
WhatsApp “zero-day exploit” news scare – what you need to knowIs WhatsApp currently under active attack by cybercriminals? Is this a clear and current danger? How...
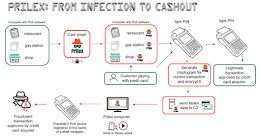
Brazilian Prilex Hackers Resurfaced With Sophisticated Point-of-Sale Malware
Brazilian Prilex Hackers Resurfaced With Sophisticated Point-of-Sale MalwareA Brazilian threat actor known as Prilex has resurfaced after a year-long operational hiatus with an advanced and complex malware to...
S3 Ep102: Cutting through cybersecurity news hype [Audio + Transcript]
S3 Ep102: Cutting through cybersecurity news hype [Audio + Transcript]Latest episode - listen now! Tell fact from fiction in hyped-up cybersecurity news...Leer másNaked SecurityLatest episode -...
Researchers Discover Chaos, a Golang Multipurpose Botnet
Researchers Discover Chaos, a Golang Multipurpose BotnetThe tool was written in Chinese and seemed China-based due to its C2 infrastructureLeer másThe tool was written in Chinese...
8 mistakes CIOs make and how to avoid them
8 mistakes CIOs make and how to avoid themFrom driving transformative change, to sharing insights into the political nature of the role, IT leaders and advisors...
CloudBees CEO: Software delivery is now ‘release orchestration’
CloudBees CEO: Software delivery is now ‘release orchestration’Enterprise software delivery company CloudBees has a new SaaS offering to discuss, and the firm's CEO gets philosophical. The...
Essential best practices: Securing critical national infrastructure
Essential best practices: Securing critical national infrastructureBy Deryck Mitchelson, Field CISO EMEA, Check Point Software Technologies. Last week, news reports indicated that a European government agency...
The Troublemaker CISO: How Much Profit Equals One Life?
The Troublemaker CISO: How Much Profit Equals One Life?Security Director Ian Keller Rants About Hospital Networks Being Internet-Connected"It's stupid and adds zero value," writes Ian Keller,...
Launch an IT career after taking these eight courses for under $50
Launch an IT career after taking these eight courses for under $50Get a great deal on 110 hours of IT training in these online courses focused...
American Airlines learns breach caused by phishing
American Airlines learns breach caused by phishingEXECUTIVE SUMMARY: The US airline, which reportedly owns the world’s largest fleet of aircraft, has fallen prey to a phishing...
Stronger Cloud Security in Azure Functions Using Custom Cloud Container
Stronger Cloud Security in Azure Functions Using Custom Cloud ContainerIn this entry, we discuss how developers can use custom cloud container image and the distroless approach...
How hardware impacts cyber security
How hardware impacts cyber securityBy Zac Amos, Features Editor, Rehack.com. Cyber security has been an important topic for over two decades, but as data breaches continue to...
Report finds women are declining CISO/CSO roles
Report finds women are declining CISO/CSO rolesProfessional risk factors into career decisions, and successful women need to encourage other women to accept the risks, says Accenture....
Cyberwar: Assessing the Geopolitical Playing Field
Cyberwar: Assessing the Geopolitical Playing FieldThe United States is arguably involved in a cyberwar against Russia and China - and appears to be losing. In this...
Adware installed 13 million times + how to uninstall it
Adware installed 13 million times + how to uninstall itEXECUTIVE SUMMARY: Cyber security researchers have discovered and disrupted a mobile ad fraud campaign involving nearly 100...
Hacker breaches Fast Company, sending offensive notifications
Hacker breaches Fast Company, sending offensive notificationsEXECUTIVE SUMMARY: The business publication known as Fast Company has confirmed that an unauthorized person recently compromised the company’s technology...
Fired admin cripples former employer’s network using old credentials
Fired admin cripples former employer's network using old credentialsAn IT system administrator of a prominent financial company based in Hawaii, U.S., used a pair of credentials...
Examining What Went Wrong for Optus
Examining What Went Wrong for OptusThe latest edition of the ISMG Security Report discusses what went wrong for Optus in the wake of one of Australia's...
Remote work security statistics in 2022
Remote work security statistics in 2022By Pete Nicoletti, Field CISO Americas, Check Point Software. After two years of having our businesses and lives impacted by the...
Live Webinar | Cybersecurity Best Practices for Remoter Workforce
Live Webinar | Cybersecurity Best Practices for Remoter WorkforceContenido de la entradaLeer másDataBreachToday.com RSS Syndication
2023: Leveraging Defender and Sentinel
2023: Leveraging Defender and SentinelContenido de la entradaLeer másDataBreachToday.com RSS Syndication
The Country Where You Live Impacts Password Choices
The Country Where You Live Impacts Password ChoicesLiteracy, levels of personal freedom, and other macro-social factors help determine how strong average passwords are in a given...
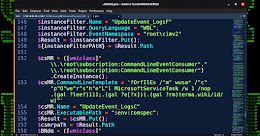
Threat Research: New Method of Volume Shadow Backup Deletion Seen in Recent Ransomware
Threat Research: New Method of Volume Shadow Backup Deletion Seen in Recent RansomwareVMware Threat Analysis Unit (TAU) researchers have recently observed a new technique for the...
Sophisticated attack or human error? How Optus lost control of your data
Sophisticated attack or human error? How Optus lost control of your dataIn the days since Optus first reported that potentially millions of its customers’ private information...
MSA-22-0027: Quiz sequential navigation bypass using web services
MSA-22-0027: Quiz sequential navigation bypass using web servicesby Michael Hawkins. Insufficient limitations in some quiz web services made it possible for students to bypass sequential navigation...
Anthony Albanese says ‘Optus should pay’ for new passports for data breach victims
Anthony Albanese says ‘Optus should pay’ for new passports for data breach victimsPush comes day after states suggest telco will pick up multi-million dollar tab for...
Optus customers, not the company, are the real victims of massive data breach | Justin Warren
Optus customers, not the company, are the real victims of massive data breach | Justin WarrenOptus executives are paid millions to ensure that, among other things,...