NSA and CISA: What To Do When Hackers Target Critical SystemsThe National Security Agency (NSA) together with the Cybersecurity and Infrastructure Agency (CISA) have issued an...
Day: September 27, 2022
Data Corruption, A Potential New Trend in Ransomware Attacks
Data Corruption, A Potential New Trend in Ransomware AttacksExmatter, a well-known data exfiltration malware used by the BlackMatter ransomware group, has been spotted operating a new...
Adware Found in 75 Apps on Google Play and App Store
Adware Found in 75 Apps on Google Play and App StoreIn a recent investigation, security researchers have discovered 75 applications on Google Play and other ten...
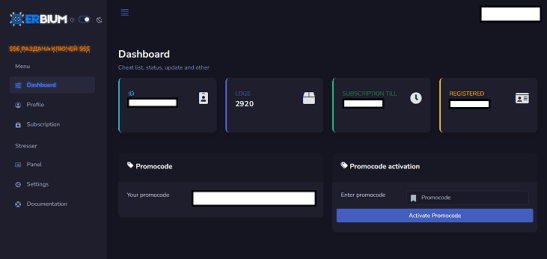
Erbium, A New InfoStealer Malware on the Market
Erbium, A New InfoStealer Malware on the MarketErbium is a new Malware-as-a-Service (MaaS) designed to steal login credentials and cryptocurrency wallets. The Malware circulates at the...
Lorenz Ransomware Detection: The Group Leverages CVE-2022-29499 Vulnerability in Mitel VoIP Devices
Lorenz Ransomware Detection: The Group Leverages CVE-2022-29499 Vulnerability in Mitel VoIP Devices The Lorenz security threat group has been targeting corporate networks across the U.S., China,...
What Is Data Exfiltration? MITRE ATT&CK® Exfiltration Tactic | TA0010
What Is Data Exfiltration? MITRE ATT&CK® Exfiltration Tactic | TA0010 The process of stealing data from a corporate system is also known as exfiltration. MITRE ATT&CK®...
Uber Breach 2022: Detect the Destructive Cyber-Attack Causing the Complete Organization’s System Takeover
Uber Breach 2022: Detect the Destructive Cyber-Attack Causing the Complete Organization’s System Takeover On September 15, Uber officially confirmed an attack resulting in an organization-wide cybersecurity...
TeamTNT Hijacking Servers: Criminal Gang Specializing in Attacking Cloud Environments is Back
TeamTNT Hijacking Servers: Criminal Gang Specializing in Attacking Cloud Environments is Back Honeypot activity spotted by one of the cybersecurity vendors confirmed that the cryptojacking TeamTNT...
Shikitega Malware Detection: Executes Multistage Infection Chain, Grants Full Control
Shikitega Malware Detection: Executes Multistage Infection Chain, Grants Full Control A new stealthy Linux malware named Shikitega is on the prowl for its victims. Its operators...
Mandiant identifies 3 hacktivist groups working in support of Russia
Mandiant identifies 3 hacktivist groups working in support of RussiaResearchers are tracking multiple self-proclaimed hacktivist groups working in support of Russia, and identified 3 groups linked...
What Is Initial Access? MITRE ATT&CK® Initial Access Tactic | TA0001
What Is Initial Access? MITRE ATT&CK® Initial Access Tactic | TA0001 What Is Initial Access? MITRE ATT&CK® Initial Access Tactic | TA0001 Some MITRE ATT&CK tactics...
Heimdal™ Featured in High Performer Quadrant Across Several Categories in G2 Fall Reports 2022
Heimdal™ Featured in High Performer Quadrant Across Several Categories in G2 Fall Reports 2022COPENHAGEN, September 27th, 2022 – After breaking being included in G2’s Summer Reports...
Erbium info-stealing malware, a new option in the threat landscape
Erbium info-stealing malware, a new option in the threat landscapeThe recently discovered Erbium information-stealer is being distributed as fake cracks and cheats for popular video games....
Top Challenges for MSSPs and MDRs and How to Overcome Them
Top Challenges for MSSPs and MDRs and How to Overcome Them Some things never grow old. In the world of security providers, there will always be...
Can Cloud Telephony Services with Military Grade Security Enable Organizations to Create High Brand Value?
Can Cloud Telephony Services with Military Grade Security Enable Organizations to Create High Brand Value?By Shubham Patidar, Research Consultant at Fact.MR In today’s technology driven world,...
CVE-2022-35405 Detection: CISA Warns of Adversaries Leveraging ManageEngine RCE Flaw
CVE-2022-35405 Detection: CISA Warns of Adversaries Leveraging ManageEngine RCE Flaw Shields up! On September 22, 2022, The Cybersecurity and Infrastructure Security Agency (CISA) released a directive...
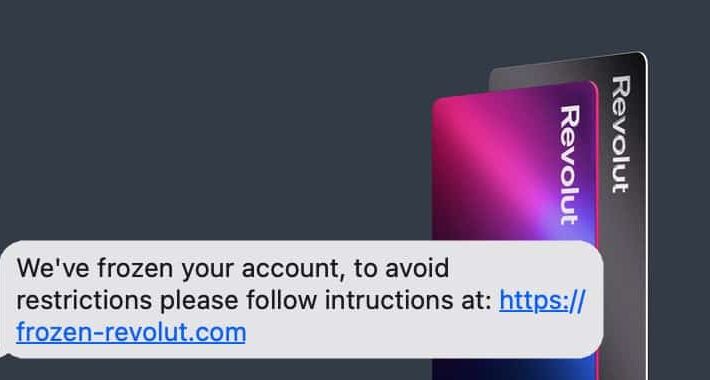
Beware Revolut frozen card scams sent via SMS text
Beware Revolut frozen card scams sent via SMS textUsers of Revolut, the popular banking app, would be wise to be on their guard - as scammers...
Australia Thinking About Tougher Cybersecurity Laws
Australia Thinking About Tougher Cybersecurity LawsThe Australian government says that it’s considering adopting tougher cybersecurity laws for companies in the telecommunication sector following the recent Optus...
NullMixer Malware Detection: Hackers Spread a Dropper Using SEO to Deploy Multiple Trojans at Once
NullMixer Malware Detection: Hackers Spread a Dropper Using SEO to Deploy Multiple Trojans at Once Cybersecurity researchers have recently revealed a new wave of adversary campaigns...
Crack The Code
Crack The CodeCybersecurity Workforce Certificate Program By Stephen Patrick, Marketing Coordinator at the University of Louisville According to the Identity […] The post Crack The Code...
TAP Air Portugal confirms hack, as Ragnar Locker gang leaks data – including that of Portugese president
TAP Air Portugal confirms hack, as Ragnar Locker gang leaks data – including that of Portugese presidentPoliticians including Portugese president Marcelo Rebelo de Sousa are amongst...
New Report on IoT Security
New Report on IoT SecurityThe Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to...
Windows 11 22H2 blocked due to blue screens on some Intel systems
Windows 11 22H2 blocked due to blue screens on some Intel systemsMicrosoft is now blocking the Windows 11 22H2 update from being offered on some systems...
Windows 11 22H2 blocked due to blue screens on some Intel systems
Windows 11 22H2 blocked due to blue screens on some Intel systemsMicrosoft is now blocking the Windows 11 22H2 update from being offered on some systems...
American Airlines learns breach caused by phishing
American Airlines learns breach caused by phishingEXECUTIVE SUMMARY: The US airline, which reportedly owns the world’s largest fleet of aircraft, has fallen prey to a phishing...
We’re Thinking About SaaS the Wrong Way
We're Thinking About SaaS the Wrong WayMany enterprise applications are built outside of IT, but we still treat the platforms they're built with as point solutions.Leer...
FIRESIDE CHAT: Why ‘digital resiliency’ has arisen as the Holy Grail of IT infrastructure
FIRESIDE CHAT: Why ‘digital resiliency’ has arisen as the Holy Grail of IT infrastructureDigital resiliency has arisen as something of a Holy Grail in the current...
How Quantum Physics Leads to Decrypting Common Algorithms
How Quantum Physics Leads to Decrypting Common AlgorithmsYouTuber minutephysics explains how Shor's algorithm builds on existing formulae like Euclid's algorithm and Fourier transforms to leverage quantum...
Should Hacking Have a Code of Conduct?
Should Hacking Have a Code of Conduct?For white hats who play by the rules, here are several ethical tenets to consider.Leer másDark ReadingFor white hats who...
Samsung Fails Consumers in Preventable Back-to-Back Data Breaches, According to Federal Lawsuit
Samsung Fails Consumers in Preventable Back-to-Back Data Breaches, According to Federal LawsuitCompany unnecessarily collected consumers' personal data and failed to safeguard it, suit alleges, leading to...