HIVE Ransomware Claims Responsibility for NYRA AttackThe New York Racing Association disclosed that, on June 30th, a cyberattack impacted IT operations, website availability, and compromised member...
Day: September 23, 2022
Fake Zoom Sites Deploying Vidar Malware
Fake Zoom Sites Deploying Vidar MalwareCyble Research and Intelligence Labs (CRIL) discovered multiple fake Zoom sites created to spread malware among Zoom users. The sites were...
2K Games’ Help Deck Platform Hacked
2K Games’ Help Deck Platform HackedAmerican video game publishing house 2K Games confirms that they have been the victims of a cyberattack. The hackers targeted 2K’s...
Phishing Scams Are Targeting Netflix Users
Phishing Scams Are Targeting Netflix UsersNetflix is one of the most popular video streaming platforms in the world, with over 200 million paying subscribers. The large...
SIEM vs Log Management – Definitions, Features, Capabilities, and Deployment
SIEM vs Log Management – Definitions, Features, Capabilities, and DeploymentIn an ideal setup, statistics should favor the defender and not the attacker. However, since cybersecurity, as...
What Is DNSSEC?
What Is DNSSEC?As its name implies, DNS security refers to the set of practices employed by an individual or an organization to prevent attacks that are...
LockBit Ransomware Builder Leaks Online
LockBit Ransomware Builder Leaks OnlineThe LockBit ransomware operation takes a severe blow after a developer has leaked online the builder of their newest ransomware encryptor. The...
Phishing Campaign Abuses LinkedIn Smart Link
Phishing Campaign Abuses LinkedIn Smart LinkLinkedIn Smart Link feature is used by threat actors to launch a phishing campaign with the purpose of stealing credit card...
BlackCat’s Ransomware Tool Gets an Upgrade
BlackCat’s Ransomware Tool Gets an UpgradeBlackCat ransomware isn’t showing signs of slowing down. The gang has released a new version of their data exfiltration tool, used...
Can I Tell You a Secret, episode 1: the beginning – podcast
Can I Tell You a Secret, episode 1: the beginning - podcastIn the first part of a new series, the Guardian journalist Sirin Kale takes us...
Intermittent Encryption Analysis
Intermittent Encryption AnalysisTo outwit cybersecurity measures, malicious actors are continually enhancing their attack techniques. This sometimes entails developing brand-new malware; other times, it entails iteratively modifying...
Can I tell you a secret? Episode two: the widening circle
Can I tell you a secret? Episode two: the widening circleAs the cyberstalker spreads his net wider, anyone could be a target. The fast-changing world of...
Can I tell you a secret? Episode one: the beginning
Can I tell you a secret? Episode one: the beginningGuardian journalist Sirin Kale takes us to a small town in the north of England to uncover...
Can I tell you a secret? Episode four: a reckoning
Can I tell you a secret? Episode four: a reckoningMatthew’s victims come face to face with him as an attempt is made to stop his torment...
K28942395: OpenSSH vulnerability CVE-2018-15473
K28942395: OpenSSH vulnerability CVE-2018-15473OpenSSH vulnerability CVE-2018-15473 Security Advisory Security Advisory Description OpenSSH through 7.7 is prone to a user enumeration vulnerability due to not delaying bailout...
Can I tell you a secret? Episode three: the man upstairs
Can I tell you a secret? Episode three: the man upstairsWho is Matthew? Journalist Sirin Kale looks for clues about who this cyberstalker really is and...
Can I tell you a secret? Episode five: a mother’s love – podcast
Can I tell you a secret? Episode five: a mother’s love – podcastJournalist Sirin Kale meets Matthew’s mother to uncover more about his past, and find...
Can I tell you a secret? Episode six: the winding clock
Can I tell you a secret? Episode six: the winding clockAs the years tick by, journalist Sirin Kale speaks to victims and those who know Matthew...
Optus cyber-attack could involve customers dating back to 2017
Optus cyber-attack could involve customers dating back to 2017CEO says company has not yet confirmed how many people were affected by hack, but 9.8 million was...
Optus cyber-attack could involve customers dating back to 2017
Optus cyber-attack could involve customers dating back to 2017CEO says company has not yet confirmed how many people were affected by hack, but 9.8 million was...
Optus cyber-attack: how do you know if your identity has been stolen and what will happen to your data?
Optus cyber-attack: how do you know if your identity has been stolen and what will happen to your data?After a massive data breach potentially exposed the...
Optus Falls Victim to Security Breach
Optus Falls Victim to Security BreachAustralian mobile operator Optus is investigating a security breach after they spotted “unauthorized access” to former and current customers’ personal data....
8 mistakes CIOs make and how to avoid them
8 mistakes CIOs make and how to avoid themFrom driving transformative change, to sharing insights into the political nature of the role, IT leaders and advisors...
Standards: The CPSO’s Best Friend
Standards: The CPSO’s Best FriendWorkshop Shines Light on Role of Standards in Cybersecurity for IoT What do Chief Product Security Officers (CPSOs) want to make their...
Morgan Stanley Sanctioned for Exposing Information of 15 Million Customers
Morgan Stanley Sanctioned for Exposing Information of 15 Million CustomersOn Tuesday, September 20, 2022, The Securities and Exchange Commission (SEC) revealed that Morgan Stanley financial services...
Telepathic Declassification
Telepathic DeclassificationFormer President Trump recently suggested that the sitting President simply needs to “think” something is declassified in order to declassify it. Is there a cascade...
Multi-Million Dollar Global Credit Card Scam Exposed
Multi-Million Dollar Global Credit Card Scam ExposedA massive global multi-million dollar scam, operating since 2019, has been uncovered. The number of victims is in the range...
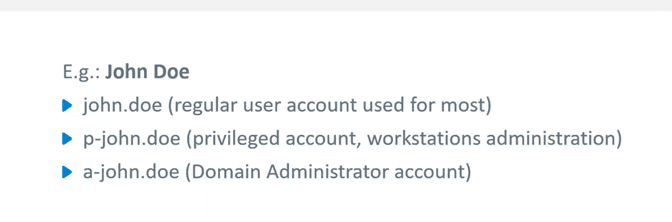
Active Directory Attack Scenarios: The Path from Printer to Domain Admin
Active Directory Attack Scenarios: The Path from Printer to Domain AdminThe post Active Directory Attack Scenarios: The Path from Printer to Domain Admin appeared first on...
How Russians Are Reacting to Putin’s Conscription Gamble
How Russians Are Reacting to Putin’s Conscription GambleReal-time data from Russian social media platforms and related illicit communities is vital to understanding the domestic public response...
WEBINAR: Bundling Up: The Importance of Layering Offensive Security Solutions
WEBINAR: Bundling Up: The Importance of Layering Offensive Security SolutionsThe post WEBINAR: Bundling Up: The Importance of Layering Offensive Security Solutions appeared first on Digital Defense....