Our Quest: Advancing Product Labels to Help Consumers Consider CybersecurityFor many decades, consumers have relied on labels to help them make decisions about which products to...
Day: September 21, 2022
Microsoft 365 phishing attacks impersonate U.S. govt agencies
Microsoft 365 phishing attacks impersonate U.S. govt agenciesAn ongoing phishing campaign targeting U.S. government contractors has expanded its operation to push higher-quality lures and better-crafted documents....
American Airlines discloses data breach after employee email compromise
American Airlines discloses data breach after employee email compromiseAmerican Airlines has notified customers of a recent data breach after attackers compromised an undisclosed number of employee email accounts...
MFA Fatigue: Hackers’ new favorite tactic in high-profile breaches
MFA Fatigue: Hackers’ new favorite tactic in high-profile breachesHackers are more frequently using social engineering attacks to gain access to corporate credentials and breach large networks....
Microsoft Defender for Endpoint will turn on tamper protection by default
Microsoft Defender for Endpoint will turn on tamper protection by defaultMicrosoft says tamper protection will soon be turned on by default for all enterprise customers in...
Top 8 takeaways from the VMWare Cybersecurity Threat Report
Top 8 takeaways from the VMWare Cybersecurity Threat ReportVMware has recently released the 2022 edition of its annual Global Incident Response Threat Report. It is critically...
Hackers steal $162 million from Wintermute crypto market maker
Hackers steal $162 million from Wintermute crypto market makerDigital assets trading firm Wintermute has been hacked and lost $162.2 million in DeFi operations, the company CEO, Evgeny Gaevoy,...
2K game support hacked to email RedLine info-stealing malware
2K game support hacked to email RedLine info-stealing malwareHackers have compromised the support system of American video game publisher 2K and now are sending support tickets...
Windows 11 22H2 is released, here are the new features
Windows 11 22H2 is released, here are the new featuresMicrosoft has released the next version of Windows 11 called "22H2," otherwise known as the Windows 11 2022...
Hive ransomware claims attack on New York Racing Association
Hive ransomware claims attack on New York Racing AssociationThe Hive ransomware operation claimed responsibility for an attack on the New York Racing Association (NYRA), which previously...
Windows 11 22H2 adds kernel exploit protection to security baseline
Windows 11 22H2 adds kernel exploit protection to security baselineMicrosoft has released the final version of security configuration baseline settings for Windows 11, version 22H2, downloadable...
Windows 10 KB5017380 preview update released with new FIDO2 features
Windows 10 KB5017380 preview update released with new FIDO2 featuresMicrosoft has released the optional KB5017380 Preview cumulative update for Windows 10 20H2, Windows 10 21H1, and...
2K Games says hacked help desk targeted players with malware
2K Games says hacked help desk targeted players with malwareAmerican video game publisher 2K has confirmed that its help desk platform was hacked and used to...
Uber exposes Lapsus$ extortion group for security breach
Uber exposes Lapsus$ extortion group for security breachIn last week’s security breach against Uber, the attackers downloaded internal messages from Slack as well as information from...
Did hackers gain full access to Uber’s critical IT systems?
Did hackers gain full access to Uber’s critical IT systems?EXECUTIVE SUMMARY: Last week, Uber Technologies Inc. experienced a high-impact cyber attack. “They pretty much have full...
Imperva mitigated long-lasting, 25.3 billion request DDoS attack
Imperva mitigated long-lasting, 25.3 billion request DDoS attackInternet security company Imperva has announced its DDoS (distributed denial of service) mitigation solution has broken a new record,...
The prevention-first approach for SOC that your team needs to adopt
The prevention-first approach for SOC that your team needs to adoptAlon Bar, Product Marketing, Threat Prevention at Check Point Software Technologies Your SOC team works around...
Revolut cyber attack exposes data belonging to thousands of customers
Revolut cyber attack exposes data belonging to thousands of customersEXECUTIVE SUMMARY: The London-based FinTech startup known as Revolut recently confirmed a breach that affected a “small...
Crypto biz Wintermute loses $160m in cyber-heist, tells us not to stress out
Crypto biz Wintermute loses $160m in cyber-heist, tells us not to stress outThe other Tessier-Ashpool AIs are surely disappointed Cryptocurrency market maker Wintermute says $160 million...
Crypto biz Wintermute loses $160m in cyber-heist, tells us not to stress out
Crypto biz Wintermute loses $160m in cyber-heist, tells us not to stress outThe other Tessier-Ashpool AIs are surely disappointed Cryptocurrency market maker Wintermute says $160 million...
What is Managed Detection and Response (MDR)?
What is Managed Detection and Response (MDR)?The term managed detection and response (MDR) refers to a cybersecurity service that employs advanced technologies and human expertise to...
What Is Privileged Identity Management (PIM)?
What Is Privileged Identity Management (PIM)?When we talk about Privileged Access Management (PAM), Privileged Identity Management (PIM), Identity and Access Management (IAM), and other access management...
Starbucks Singapore Customer Data Accessed Illegally in Data Leak
Starbucks Singapore Customer Data Accessed Illegally in Data LeakStarbucks Singapore notifies members of its Rewards loyalty programme that personal information, including phone numbers, addresses, and birthdays...
Malware vs. Ransomware: Do You Know the Difference?
Malware vs. Ransomware: Do You Know the Difference?When it comes to cybersecurity, few domains can match its ever-growing lexicon and branching categories. It is no wonder...
Empress EMS Discloses Data Breach Following Ransomware Attack
Empress EMS Discloses Data Breach Following Ransomware AttackNew York-based company, Empress EMS (Emergency Medical Services), has disclosed through an official notification that it’s been the victim...
The European Union Prepares New Cybersecurity Regulations for IoT Devices
The European Union Prepares New Cybersecurity Regulations for IoT DevicesThe European Commission has suggested a new “EU Cyber Resilience Act.” The act intends to protect customers...
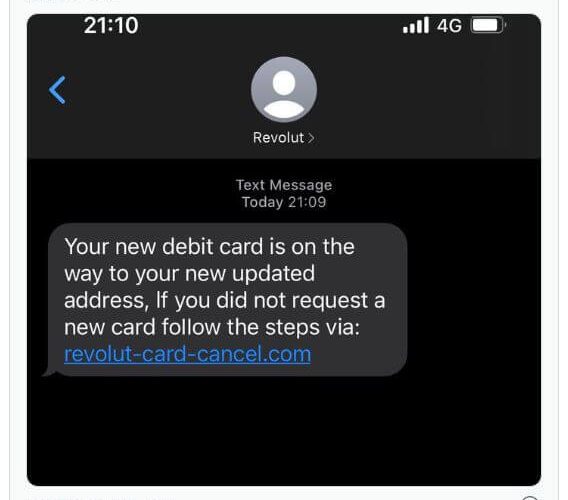
Revolut Suffers Data Breach
Revolut Suffers Data BreachOver 50,000 people’s personal information was compromised as a result of a cyberattack on Revolut. After a Revolut employee fell for a phishing...
Allies Warn of Iranian Ransom Attacks Using Log4Shell
Allies Warn of Iranian Ransom Attacks Using Log4ShellUS authorities indict and sanction in fresh crackdownLeer másUS authorities indict and sanction in fresh crackdown
No Customer Data or Encrypted Password Vaults Were Breached in LastPass Incident
No Customer Data or Encrypted Password Vaults Were Breached in LastPass IncidentIn an update to the notification regarding the cyberattack suffered in August, LastPass, one of...
CISA Expands Vulnerabilities Catalog With Old, Exploited Flaws
CISA Expands Vulnerabilities Catalog With Old, Exploited FlawsFour of the CVEs posted are from 2013, and one is from 2010Leer másFour of the CVEs posted are...