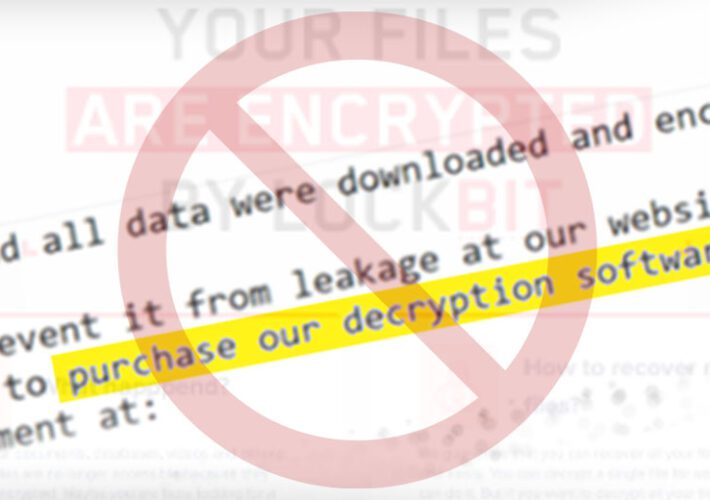
Karma Calling: LockBit Disrupted After Leaking Entrust FilesRansomware Group's Site Hit by Days-Long Distributed-Denial-of-Service AttackRansomware karma: The notorious LockBit 3.0 ransomware gang's site has been disrupted...
Day: September 5, 2022
Twitter Security Allegations: Cybersecurity Experts Respond
Twitter Security Allegations: Cybersecurity Experts RespondTakeaway: Behind-the-Scenes Security Reality at Well-Known Brands Not Always PrettyCybersecurity experts have been reacting to industry veteran Peiter Zatko's allegations of...
As States Ban Ransom Payments, What Could Possibly Go Wrong?
As States Ban Ransom Payments, What Could Possibly Go Wrong?North Carolina Ban Affects State/Local Governments, Public Schools and UniversitiesAs ransomware continues to pummel organizations left, right...
The Key To Compliance? Third-Party Management
The Key To Compliance? Third-Party ManagementGetting a Grip on Third-Party AccessThey’re necessary contributors to the business ecosystem, but there’s risk associated with third-party remote access, including...
Addressing Security Risks of Mounting Legacy Health Data
Addressing Security Risks of Mounting Legacy Health DataIn many healthcare entities, the amount of data that is being generated and retained continues to grow - and...
Reducing Risks by Optimizing Your Cybersecurity Workflow
Reducing Risks by Optimizing Your Cybersecurity WorkflowCISOs have enough tools to identify security weaknesses, says Yoran Sirkis, but they need a way to make the information...
Banning Ransoms: The Evolving State of Ransomware Response
Banning Ransoms: The Evolving State of Ransomware ResponseThe latest edition of the ISMG Security Report explores the possible unintended consequences of banning ransom payments, the challenges...
Overcoming Zero Trust Obstacles in Healthcare
Overcoming Zero Trust Obstacles in HealthcareThe sheer number of connected devices in healthcare environments is one of the top challenges healthcare entities face in adopting a...
Navigating Obstacles on the Road to Zero Trust with John Kindervag
Navigating Obstacles on the Road to Zero Trust with John KindervagContenido de la entradaLeer másDataBreachToday.com RSS Syndication
Simplified Approach to Solving Modern Security Complexities
Simplified Approach to Solving Modern Security ComplexitiesContenido de la entradaLeer másDataBreachToday.com RSS Syndication
How Machine Identity Management Protects Your Digital Identities
How Machine Identity Management Protects Your Digital IdentitiesContenido de la entradaLeer másDataBreachToday.com RSS Syndication
MSP Conversation | Tactics Cyber Attackers Use to Gain Access
MSP Conversation | Tactics Cyber Attackers Use to Gain AccessContenido de la entradaLeer másDataBreachToday.com RSS Syndication
ENISA: Software vulnerability prevention initiatives
ENISA: Software vulnerability prevention initiativesThe European Network and Information Security Agency, ENISA, has compiled a list of existing initiatives focused on finding and preventing software vulnerabilities.Leer...
Accounting of Disclosures Under the HITECH Act
Accounting of Disclosures Under the HITECH ActA notice of proposed rulemaking from the HHS Office for Civil Rights that would modify the HIPAA Privacy Rule standard...
FFIEC Final Authentication Guidance
FFIEC Final Authentication GuidanceThe Final FFIEC Guidance has been issued and its main intent is to reinforce the 2005 Guidance's risk management framework and update the...
Annual Report to Congress on Breaches of Unsecured Protected Health Information
Annual Report to Congress on Breaches of Unsecured Protected Health InformationThe Department of Health and Human Services' Office for Civil Rights provided a report to Congress...
HelpSystems Buys Red-Teaming Firm for Offensive Security
HelpSystems Buys Red-Teaming Firm for Offensive SecurityPurchase of Outflank Marks Security Software Firm's 10th Acquisition in 20 MonthsHelpSystems acquired Dutch red-teaming startup Outflank to help critical...
Cybercriminal Service ‘EvilProxy’ Seeks to Hijack Accounts
Cybercriminal Service ‘EvilProxy’ Seeks to Hijack AccountsEvilProxy Bypasses MFA By Capturing Session CookiesOne of the biggest challenges for cybercriminals is how to defeat multifactor authentication. New...
San Francisco 49ers Cybersecurity Incident Affected 20,000
San Francisco 49ers Cybersecurity Incident Affected 20,000BlackByte Ransomware-as-a-Service Group Claimed 49ers as Victims in FebruaryThe NFL's San Francisco 49ers will notify more than 20,000 Americans that...
New SharkBot Trojan Spread Via Mobile Security Apps
New SharkBot Trojan Spread Via Mobile Security AppsNow-Removed Apps Have 60K Downloads; Target Victims in Australia, USThe operators behind banking Trojan SharkBot are distributing an updated...
Anonymous hacked Yandex taxi causing a massive traffic jam in Moscow
Anonymous hacked Yandex taxi causing a massive traffic jam in MoscowThe popular collective Anonymous and the IT Army of Ukraine hacked the Yandex Taxi app causing...
Fake Antivirus and Cleaner Apps Caught Installing SharkBot Android Banking Trojan
Fake Antivirus and Cleaner Apps Caught Installing SharkBot Android Banking TrojanThe notorious Android banking trojan known as SharkBot has once again made an appearance on the Google Play...
Microsoft mistakenly rated Chromium, Electron, as malware
Microsoft mistakenly rated Chromium, Electron, as malwareWindows Defender update fixed the mess after a weekend of false positive weirdness Microsoft appears to have fixed a problem...
IRS Leaks 120,000 Taxpayers’ Personal Details
IRS Leaks 120,000 Taxpayers' Personal DetailsUS government still working out what went wrongLeer másUS government still working out what went wrong
Samsung Reveals New US Data Breach
Samsung Reveals New US Data BreachPersonal info of "certain customers" was affectedLeer másPersonal info of "certain customers" was affected
New Rules for Crypto Exchanges to Stop Sanctions Evaders
New Rules for Crypto Exchanges to Stop Sanctions EvadersUK Treasury demands exchanges report suspected breachesLeer másUK Treasury demands exchanges report suspected breaches
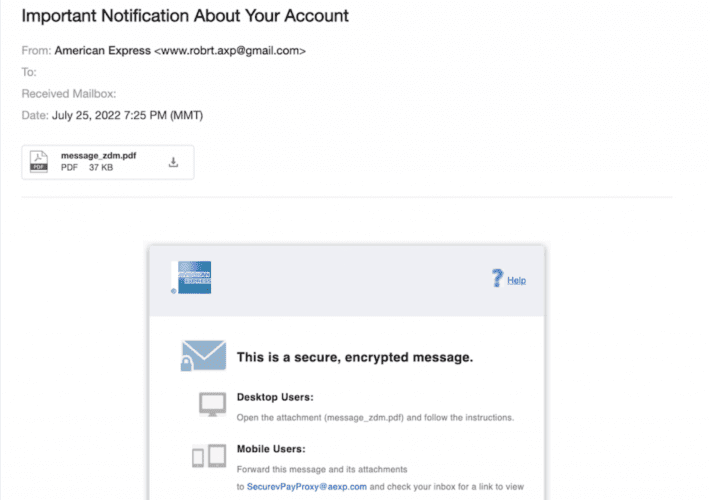
A new phishing scam targets American Express cardholders
A new phishing scam targets American Express cardholdersCybersecurity firm Armorblox discovered a new phishing campaign aimed at American Express customers. Armorblox researchers uncovered a new phishing campaign that is targeting...
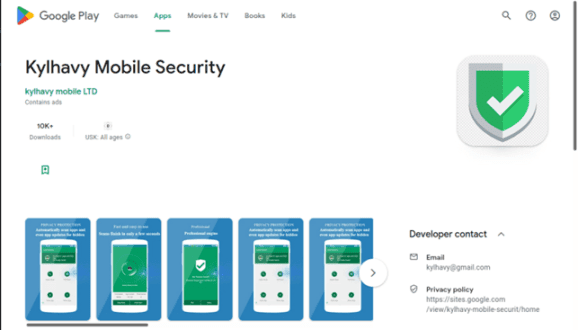
A new SharkBot variant bypassed Google Play checks again
A new SharkBot variant bypassed Google Play checks againExperts spotted an upgraded version of the SharkBot malware that was uploaded to the official Google Play Store....
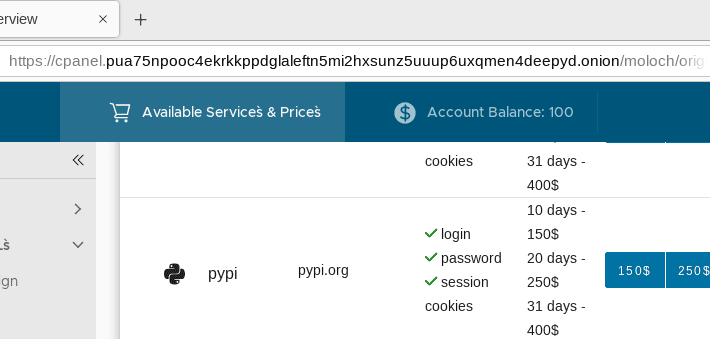
EvilProxy Phishing-As-A-Service With MFA Bypass Emerged In Dark Web
EvilProxy Phishing-As-A-Service With MFA Bypass Emerged In Dark WebResecurity researchers discovered a new Phishing-as-a-Service (PhaaS) called EvilProxy advertised on the Dark Web. Original post: https://resecurity.com/blog/article/evilproxy-phishing-as-a-service-with-mfa-bypass-emerged-in-dark-web Following the recent...
GDPR: Four Years After Its Enactment, Where Do We Stand?
GDPR: Four Years After Its Enactment, Where Do We Stand?By Kevin Kelly is the VP and GM, Global Compliance Solutions, Skillsoft More than 15 years ago,...