I’ll update my smartphone tomorrow: The impact of Zero-Day attacks on mobile devicesBy Peter Elmer, Principle Security Expert – EMEA, Member of the Office of the...
Day: July 24, 2022
Understanding a particular Zero Trust journey from the lens of a CISO at an American healthcare payer
Understanding a particular Zero Trust journey from the lens of a CISO at an American healthcare payerEXECUTIVE SUMMARY: In this interview, the CISO of a healthcare...
AI-based social engineering is the next-generation of hacking humans
AI-based social engineering is the next-generation of hacking humansKeely Wilkins has been in the technology industry for nearly thirty years. She has worked in corporate, higher...
7 key considerations: Zero Trust Network Architecture
7 key considerations: Zero Trust Network ArchitectureEXECUTIVE SUMMARY: Explore seven key considerations for when you and your team evaluate a Zero Trust Network Access (ZTNA) solution...
The end of DDoS attacks is near, with these mitigation measures
The end of DDoS attacks is near, with these mitigation measuresDavid Hobbs currently serves in the Office of the CTO at Check Point while also managing...
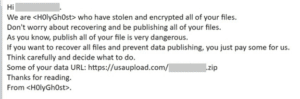
How to prevent Holy Ghost ransomware attacks on small businesses
How to prevent Holy Ghost ransomware attacks on small businessesEXECUTIVE SUMMARY: Holy Ghost ransomware operators have styled themselves as a legitimate corporate entity that tries to...
8 highly effective insider fraud prevention tips for 2022
8 highly effective insider fraud prevention tips for 2022EXECUTIVE SUMMARY: While some threat actors sequester themselves in their parents’ basements or operate out of unmarked buildings...
Security considerations for telehealth businesses
Security considerations for telehealth businessesDevin Partida writes about cyber security and technology. She is also the Editor-in-Chief of ReHack.com. During the pandemic, telehealth garnered extensive attention due...
Darkweb Vendor "Dragoncove” Indicted in New York
Darkweb Vendor "Dragoncove” Indicted in New YorkA three-count indictment accuses a man living in New York of selling heroin and cocaine through vendor accounts on darkweb......
CVE-2022-35741: Apache CloudStack SAML Single Sign-On XXE Vulnerability
CVE-2022-35741: Apache CloudStack SAML Single Sign-On XXE VulnerabilityRecently, A vulnerability that allows attackers to execute XML external entity (XXE) injection has been patched in Apache CloudStack....
Woman Allegedly Tried to Hire a Hitman to Kill Her Coworker
Woman Allegedly Tried to Hire a Hitman to Kill Her CoworkerA 26-year-old allegedly tried to hire a hitman on the darkweb to kill a colleague “when...
pretender: relaying attacks featuring DHCPv6 DNS takeover
pretender: relaying attacks featuring DHCPv6 DNS takeoverpretender pretender is a tool developed by RedTeam Pentesting to obtain machine-in-the-middle positions via spoofed local name resolution and DHCPv6......
CVE-2022-26138: Hard-Coded Password Confluence Server and Data Center
CVE-2022-26138: Hard-Coded Password Confluence Server and Data CenterAtlassian has released security updates to address three critical-severity vulnerabilities in its products that could be exploited to cause...
Pinecone – A WLAN Red Team Framework
Pinecone – A WLAN Red Team FrameworkPinecone is a WLAN networks auditing tool, suitable for red team usage. It is extensible via modules, and it is......
Finnish Customs Sold Almost 1,900 BTC for $47.5 Million
Finnish Customs Sold Almost 1,900 BTC for $47.5 MillionFinnish Customs announced the sale of 1,889 Bitcoins seized during investigations into drug crimes. According to a press...
pycrate v0.5.5 releases: Python library to ease the development of encoders and decoders
pycrate v0.5.5 releases: Python library to ease the development of encoders and decodersPycrate is a French word for qualifying bad wine. The present software library has...
doenerium: Fully undetected grabber
doenerium: Fully undetected grabberdoenerium Fully undetected grabber (grabs wallets, passwords, cookies, modifies discord client, etc.) Features Stealer Discord Token Discord Info – Username,... The post doenerium:...
Amazon might own your doctor’s office after this latest acquisition
Amazon might own your doctor’s office after this latest acquisitionEXECUTIVE SUMMARY: Amazon is set to buy One Medical, a group that operates over 180 medical offices...
LiveTargetsFinder – Generates Lists Of Live Hosts And URLs For Targeting, Automating The Usage Of MassDNS, Masscan And Nmap To Filter Out Unreachable Hosts And Gather Service Information
LiveTargetsFinder – Generates Lists Of Live Hosts And URLs For Targeting, Automating The Usage Of MassDNS, Masscan And Nmap To Filter Out Unreachable Hosts And Gather...
Candiru spyware exploited Chrome 0-day flaw to attack journalists
Candiru spyware exploited Chrome 0-day flaw to attack journalistsOn July 4, 2022, the Google Chrome stable channel was updated to version 103.0.5060.114. The vulnerabilities fixed by...
VLANPWN: VLAN attacks toolkit
VLANPWN: VLAN attacks toolkitVLANPWN VLAN attacks toolkit DoubleTagging.py – This tool is designed to carry out a VLAN Hopping attack. VLAN hopping is... The post VLANPWN:...
modDetective – Tool That Chronologizes Files Based On Modification Time In Order To Investigate Recent System Activity
modDetective – Tool That Chronologizes Files Based On Modification Time In Order To Investigate Recent System ActivitymodDetective is a small Python tool that chronologizes files based...
How new encryption standards can protect your data from the next breach
How new encryption standards can protect your data from the next breachTilo Weigandt is an entrepreneur who makes it his mission to combat hacks and leaks....
Phishing Bonanza: Social-Engineering Savvy Skyrockets as Malicious Actors Cash In
Phishing Bonanza: Social-Engineering Savvy Skyrockets as Malicious Actors Cash InContenido de la entradaLeer másProofpoint News Feed