Source: heimdalsecurity.com – Author: Cristian Neagu
The Importance of Choosing the Right Privilege Identity Management Solution
The essence of effective Privileged Identity Management (PIM) lies not in identity or management but in privilege. A robust PIM system focuses on identifying those who should, and equally importantly, those who should not, have administrative access to important accounts and systems. This access empowers users with capabilities like accessing secure data, altering configurations, installing software, and modifying accounts.
Privileged Access Management (PAM) and PIM are part of Identity Access Management, specifically designed to safeguard privileged accounts. These accounts are given to a select few users who require access to critical systems and databases with highly sensitive information.
PIM aims to prevent unauthorized or malicious use of these accounts. Additionally, PIM can manage and secure all user identities in an organization by regulating access to privileged accounts and providing just-in-time access to trusted users.
Implementing PIM solutions is key for companies, allowing them to enforce access policies strictly on a need-to-know basis.
Here are some benefits of a strong privileged identity management solution.
- Track who can access accounts and make sure it’s secure when roles change.
- Keep important passwords safe and track their use to stop any misuse.
- Manage accounts all in one place, making it simpler across devices and systems.
- Utilize real-time audits and detailed reports to enforce security controls, identifying and stopping suspicious user behavior and misuse of privileged accounts.
- Get instant alerts about any risky actions for quick responses to security threats.
- Ensure compliance with industry regulations, including HIPAA, PCI DSS, GDPR, NERC-CIP, SOX, and others.
Privileged Identity Management vs. Privileged Access Management
PIM and PAM deal with how companies control access to their most important resources, such as servers, databases, applications, and Kubernetes clusters. They follow the principle of least privilege to restrict both the number of users and their level of access to secure systems and sensitive data.
PIM looks closely at a user’s access, concentrating on identity and detailing existing permissions. On the other hand, PAM is about managing root access and monitoring access in real-time as users request it.
In simple terms, PIM outlines given permissions, while PAM deals with immediate access requests to resources.
How to Choose the Right Privileged Identity Management Solution for Your Business
When selecting privileged identity management solutions, ensure it offers features that align with your organization’s needs. Here are some key features to consider:
- Opt for “just-in-time” or “zero standing privilege” (ZSP) access in your PIM solution to limit user privileges for tasks.
- Assess your organization’s specific requirements for managing privileged identities, considering user numbers, system types, and compliance.
- Choose a PIM solution that scales with your business, accommodating user and system growth.
- Configure custom real-time alerts for immediate notification of suspicious behaviors or privileged session activity.
- Evaluate features like multi-factor authentication and encryption for enhanced protection.
- Ensure seamless integration with existing IT infrastructure, applications, and security tools.
The Top Privileged Identity Management Tools
Listed below are ten top Privileged Identity Management tools that you can consider for your organization.
Heimdal®
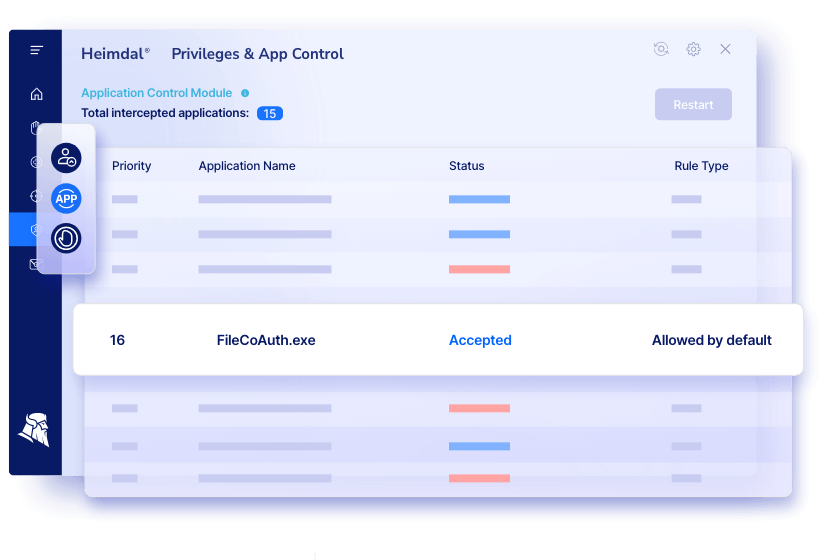
Heimdal®’s Privilege Elevation and Delegation Management & Application Control solution provides unparalleled control and flexibility to IT professionals, system administrators, and security teams.
It is the world’s only bundled product that combines the functionalities of Access Management and Application Control. The line-up proactively secures your entire environment, ensuring compliance with the most common industry standards such as Cyber Essentials, NIST, HIPAA, PCI-DSS, and many more. Moreover, it helps in boosting the productivity of users and admins while being completely transparent.
Heimdal® Top Features
- Total Privilege Management: Define and manage role-based access control and delegation policies with ease.
- Just-in-Time Secured Privilege Access: Mitigate the risk of prolonged exposure to privileged access and reduce the attack surface significantly by implementing JIT access to grant temporarily elevated privileged to users only when necessary.
- Reporting and Compliance: Generate comprehensive reports, track privileged access/session activities, and effortlessly demonstrate compliance with international or regional regulatory requirements.
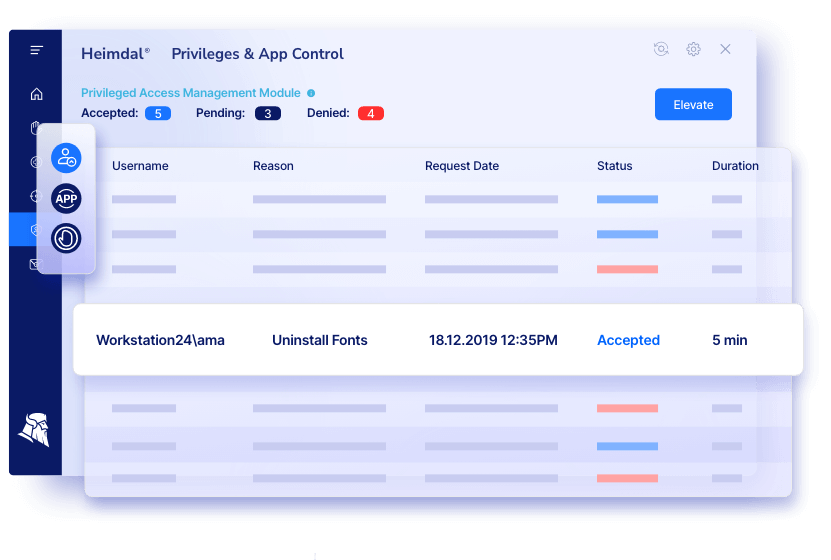
The Privileges and Application Control line-up secures effectively all three major areas of your IT access infrastructure: management of privileges, application control, and auditing, ensuring everything works smoothly and threats are kept away.
Heimdal® Pros
- Heimdal®’s solution is infinitely customizable. You can set filters, create white and blacklists, engage passive mode as defined by admins, and more.
- User-friendly interface.
- Heimdal® incorporates and easy to enable Passive Mode for system indexing.
- Easy to enable Auto-approval flow with defined rules and automatic de-escalation on threat.
- Heimdal® lets you expand your suite with cross-functional modules, that you can control all in a single interface and dashboard.
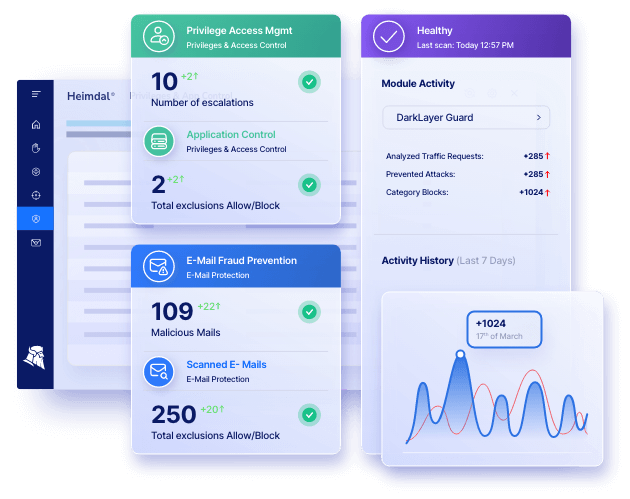
Heimdal®’s Privileged Access Management supports PEDM-type non-privileged user account curation features for AD (Active Directory), Azure AD, or hybrid setups.
Under PEDM, the PAM solution allows for the retention of administrative permissions for specific users and/or domain groups that can be traced back to specific endpoints or groups. Its TIL (Time-to-Live) feature acts as JIT (Just-in-Time).
Heimdal® Cons
Heimdal®’s solution is not yet able to send real-time alerts in case of anomalies for user activities. The requests have to be be reviewed case-by-case by the admins who will decide whether to approve it or not.
Heimdal® Pricing
Book a demo with Heimdal® experts and take the solution for a spin! Then receive an offer tailored specifically on your organization’s needs and size.
CyberArk Privileged Access Manager
CyberArk holds the largest market share of privileged access management customers in various polls and research. Their solution works well for a variety of needs, catering to customers of all sizes. In addition to being reliable, CyberArk provides flexible deployment options, including SaaS and on-premise solutions.
CyberArk Top Features
- Allows managing privileged credentials for humans and machines across thousands of endpoints.
- Can use CyberArk’s adaptive MFA and SSO for user validation.
- Option to implement just-in-time access for users to support a Zero-Trust security model.
- Offers automation capabilities that integrate into various team workflows.
CyberArk Pros
- 350+ software integrations on the CyberArk Marketplace.
- Choice between cloud-based SaaS and on-premises self-hosted deployment options.
- Record user sessions for compliance reporting and auditing purposes.
CyberArk Cons
- Challenging to set up and navigate.
- Threat detection and response features limited to self-hosted setups.
- Not tailored for cloud-native environments or modern infrastructure tools.
- Limited flexibility as it relies on CyberArk’s proprietary tools for credential management.
CyberArk Pricing
CyberArk’s pricing can be challenging as it varies across products. The platform encourages reaching out to their sales team for a personalized quote.
ManageEngine PAM360
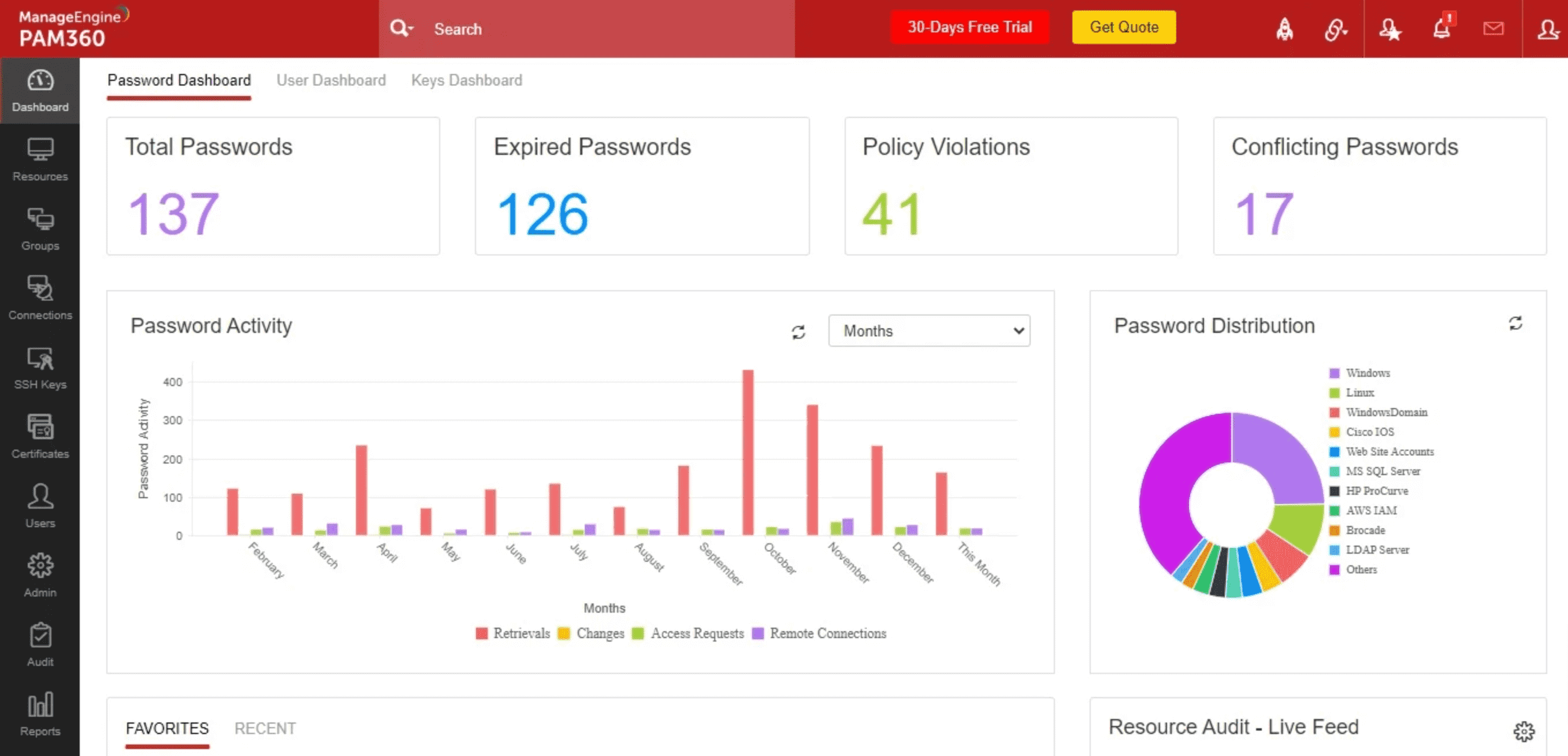
PAM360 from ManageEngine is part of Zoho Corp’s lineup of security products. This privileged access management solution stands out in finding accounts across a company’s IT setup. The user-friendly, all-in-one platform provides control and monitoring for network resources, with a focus on safeguarding assets during development.
ManageEngine PAM360 Top Features
- PAM360 discovers and onboards privileged users and resources for immediate identification of standing privileges.
- Admins set up just-in-time access with least workflows after onboarding.
- The platform securely stores all credentials in an encrypted vault with role-based access.
ManageEngine PAM360 Pros
- AI-driven security features for detecting, preventing, and addressing breaches.
- Robust discoverability feature locates accounts across the IT infrastructure.
- Simple deployment and maintenance processes for ease of use.
ManageEngine PAM360 Cons
- Exclusive availability in an on-premises deployment model.
- Limited options for adding organizational policies to enhance password management requirements.
- Not suitable for cloud-native environments or data containers.
- Session management restricted to resource-intensive HTML5 browser session emulation.
ManageEngine PAM360 Pricing
- Standard – US$ 12 / technician / month
- Professional – US$ 23 / technician / month
- Enterprise – US$ 58 / technician / month
Microsoft Entra ID
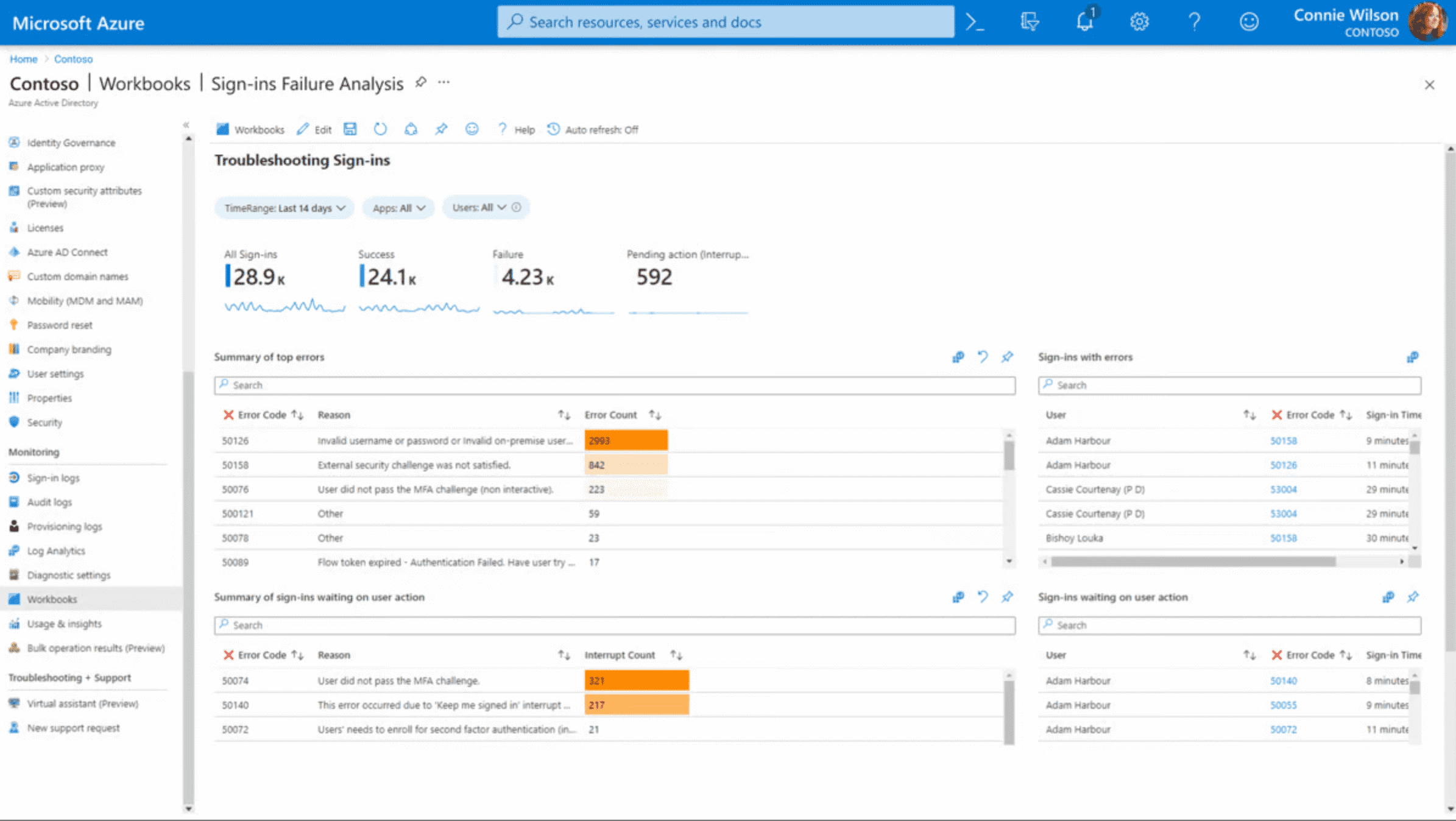
Entra ID is an identity and access management solution with built-in security. It links individuals to their applications, devices, and data, contributing to safeguarding against identity compromise.
Microsoft Entra ID Top Features
- Reliable adaptive access featuring multi-factor authentication and Conditional Access policies.
- Effortless user experience with single sign-on, password-less, and a user portal.
- Unified identity management connecting both privileged users and external individuals to all applications and devices.
Microsoft Entra ID Pros
- Seamless integration of authentication into both cloud-based and on-premises applications.
- Easily accessible customer support.
- User friendly interface
Microsoft Entra ID Cons
- Need to visit 3-4 websites for tool access.
- The extensive features can make system administration complex.
- Complexity, insufficient documentation, and limited on-premises support may deter some data engineers.
Microsoft Entra ID Pricing
- Microsoft Entra ID Free
- Microsoft Entra ID P1 – US $6 user/month
- Microsoft Entra ID P2 – US $9 user/month
- Microsoft Entra ID Governance – US $7 user/month
Delinea Secret Server
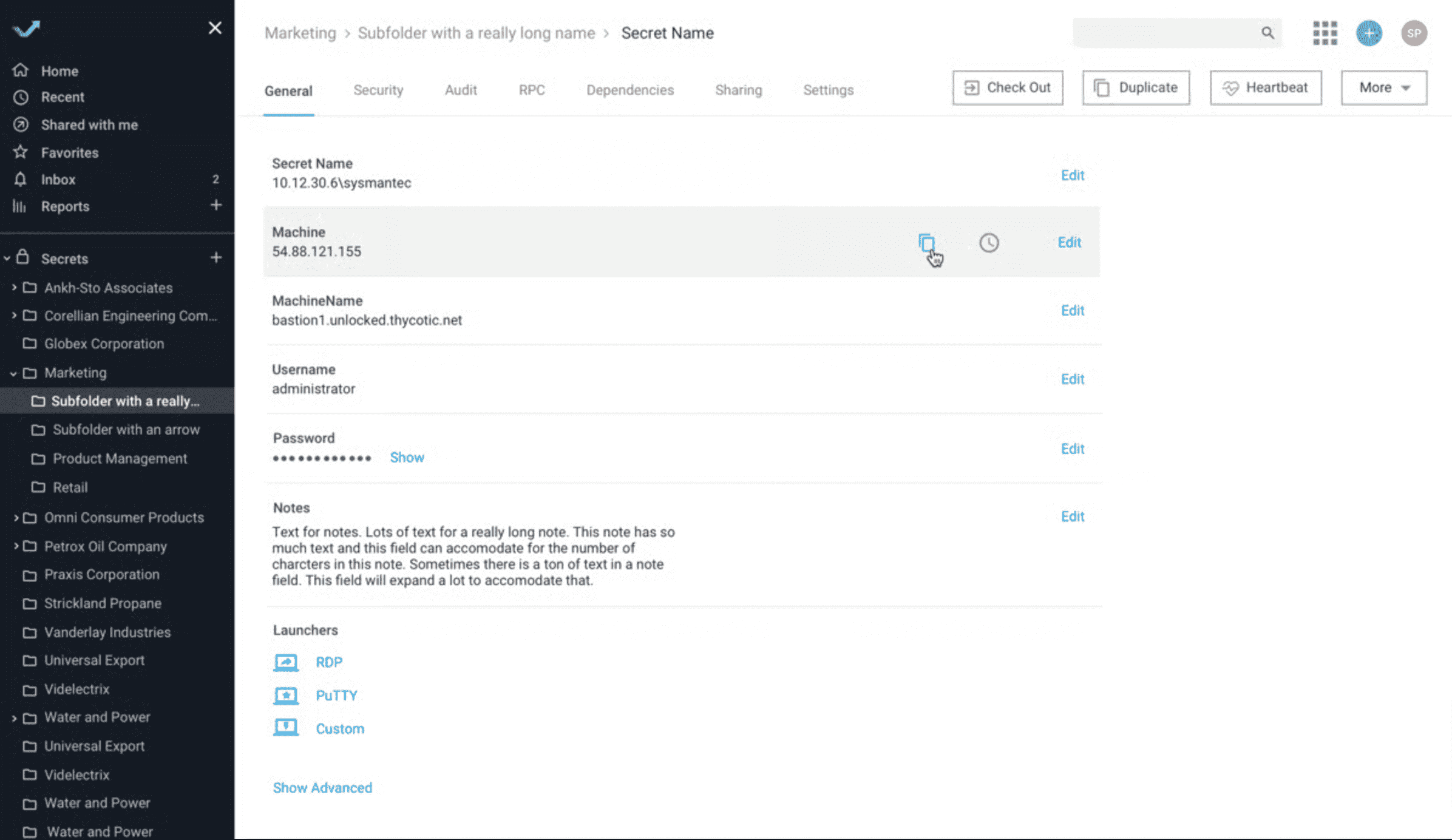
Secret Server, Delinea’s tool for managing special access, helps organizations keep an eye on, control, and secure access to important corporate databases, applications, hypervisors, security tools, and network devices. With its security features and session monitoring feature, Secret Server ensures businesses protect sensitive data from account takeover attacks and follow data protection regulations.
Delinea Secret Server Top Features
- Delinea’s Secret Server is an encrypted vault for credentials, storing up to 10,000 secrets in the cloud or an unlimited number on-premises.
- Seamless integration with Active Directory and LDAP, implementing least-privilege policy with RBAC for identity management.
- Features robust reporting and automation, including automatic password changes and active password checks.
Delinea Secret Server Pros
- Offers in both on-premise and cloud versions.
- Simple installation, configuration, and management processes.
- Provides both cloud-based SaaS and self-hosted on-premises deployment models.
Delinea Secret Server Cons
- Does not secure access to cloud-native databases or modern infrastructure tools.
- Primarily designed to support Windows-based environments and legacy databases.
- Lacks native agentless recording functionality for RDP session management.
Delinea Secret Server Pricing
Delinea Secret Server encourages reaching out to their sales team for a personalized quote.
StrongDM
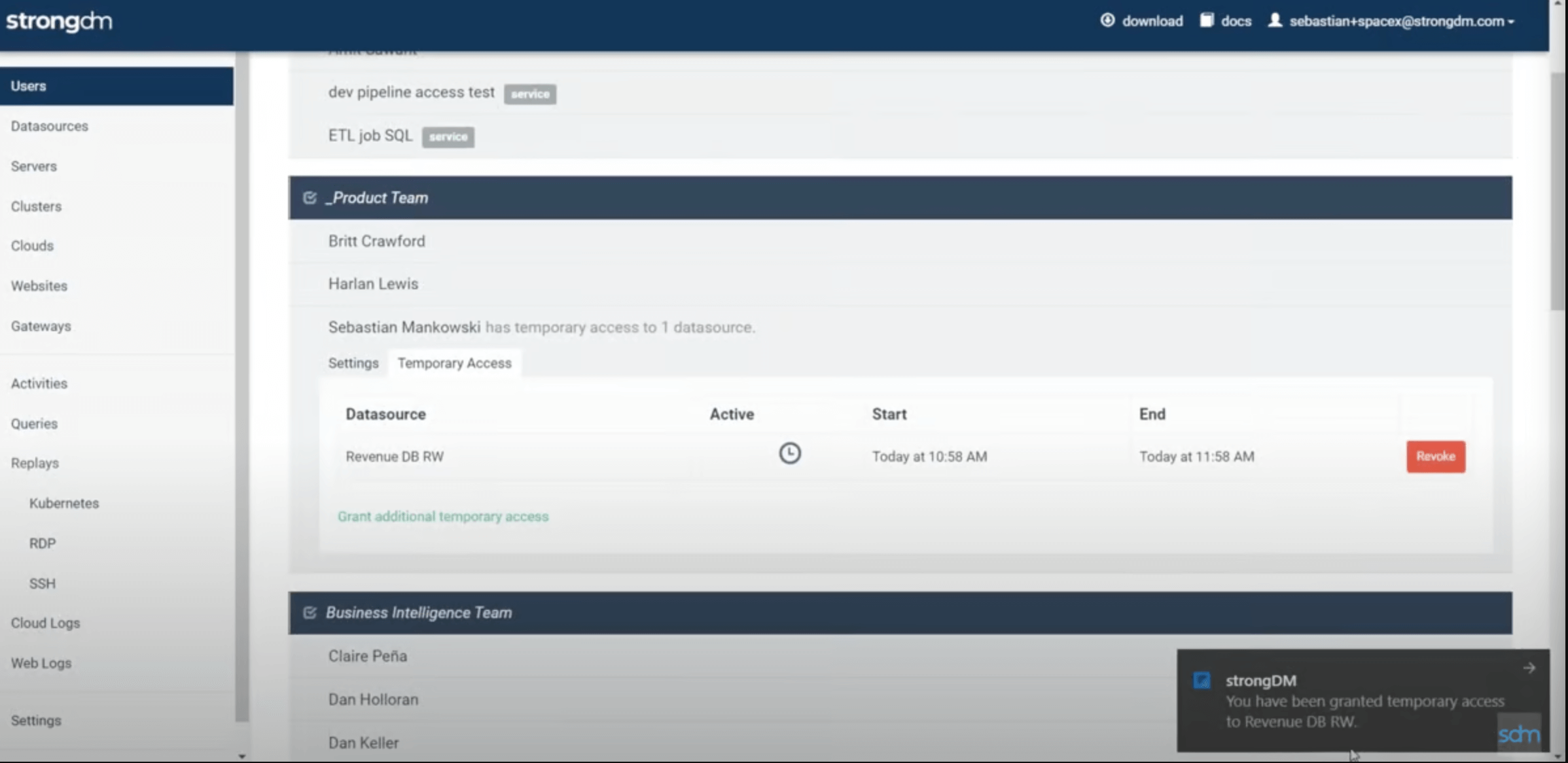
StrongDM is a platform for managing access dynamically. It prioritizes people, providing technical staff a direct path to the critical infrastructure they need for maximum productivity. End users enjoy quick, user-friendly, and auditable access to the resources they need, while administrators use simplified workflows to manage access and improve security and compliance.
StrongDM Top Features
- Cloud-first IAP simplifies monitoring and managing access to databases, servers, Kubernetes clusters, and web apps.
- Offers complete access control, capturing precise details of all user sessions.
- Acts as a single source of truth for access data, ensuring regulatory compliance and facilitating comprehensive reporting and log searches.
StrongDM Pros
- Embraces zero trust principles through an all-inclusive, cloud-native infrastructure access platform.
- Provides complete visibility for thorough monitoring and logging.
- Boasts extensive automation capabilities for smooth permissions management.
StrongDM Cons
- Available exclusively as a SaaS offering.
- Requires continual access to the StrongDM API for accessing managed resources.
- An expensive option.
StrongDM Pricing
- Essentials – US $70 user/month
- Enterprise – Contact sales
- GovCloud – Contact sales
Senhasegura
Senhasegura is a privileged access management solution that helps companies put strict and complex controls on access to important credentials in an automated and centralized way. The solution protects IT infrastructure from data breaches and potential compliance issues, meeting requirements like LGPD, GDPR, PCI DSS, SOX, NIST, HIPAA, ISO 27001, and ISA 62443.
Senhasegura Top Features
- Senhasegura’s Scan Discovery maps all assets, including digital certificates.
- The solution integrates devices, credentials, containers, playbooks, certificates, and SSH keys.
- Administrators configure access groups and define users for physical or remote access once assets are identified.
Senhasegura Pros
- Creates access flows based on time and authorization, maintaining real-time traceability and auditing for credentials and remote sessions.
- Builds knowledge and problem resolution bases for agile issue resolution through session auditing.
- Quick technical support and responsive company for customer suggestions.
Senhasegura Cons
- Limited integration options with other security tools for vault usage.
- The interface can be confusing for users.
- Management may seem complex, attributed to tags and group settings.
Senhasegura Pricing
Senhasegura encourages reaching out to their sales team for a personalized quote.
JumpCloud Open Directory Platform
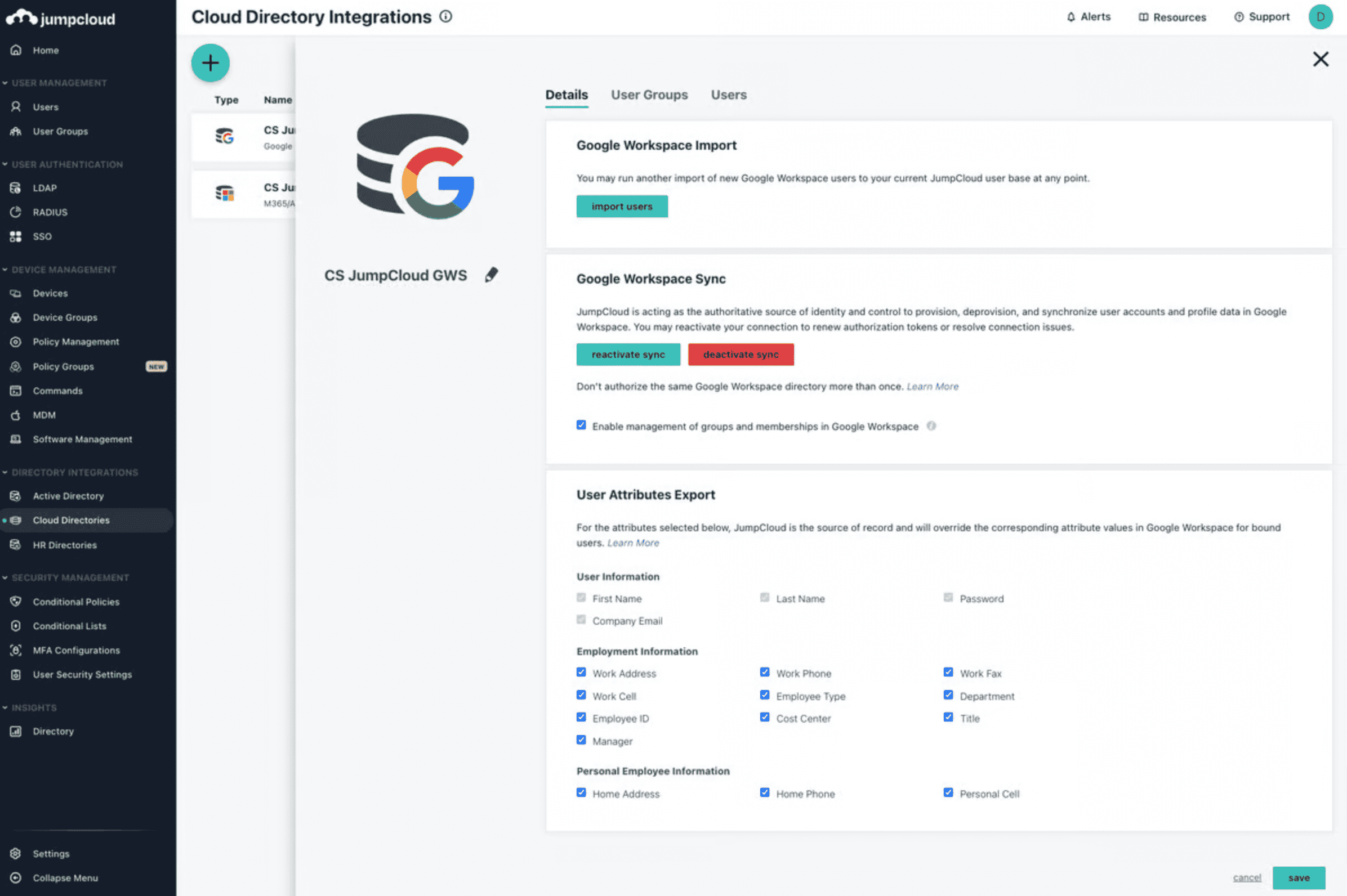
JumpCloud’s Open Directory Platform™ securely connects important users to essential systems, applications, files, and networks. It provides a clear view and control over important user accounts, enforcing strong authentication through Multi-Factor Authentication (MFA). Integrated with single sign-on (SSO), administrators can set specific policies governing resource access for important accounts and individual users based on their identity.
JumpCloud Top Features
- JumpCloud’s Open Directory Platform has robust password and SSH Key management for privileged accounts, including granular controls and alerts for expiries and brute force attempts.
- Device management prompts privileged users to rotate passwords at intervals, automatically updating access across MacOS, Windows, and Linux devices, reducing risks from static passwords and credential phishing.
- Highly scalable and flexible solution.
JumpCloud Pros
- User-friendly interface.
- Comprehensive visibility and control.
- Device management automates password rotation for added security.
JumpCloud Cons
- Limited integration options with other security tools.
- Exclusive availability as Software as a Service (SaaS).
- Continuous API access requirements may raise security concerns.
JumpCloud Pricing
- JumpCloud Free
- A La Carte Monthly Pricing – US 3 /user/month
SecureLink
SecureLink ensures company security by verifying individual identities through separate accounts. Users can conveniently grant third parties just enough access to relevant information. The solution supports various protocols and connectivity requirements, including RDP, VNC, SSH, Telnet, HTTPS, and other TCP or UDP-based protocols.
SecureLink Top Features
- Users can conveniently grant third parties access to relevant information as needed.
- Compatible with a variety of protocols and connectivity requirements for vendors.
- Supports protocols like RDP, VNC, SSH, Telnet, HTTPS, and others for secure connections.
SecureLink Pros
- Enhances security by verifying individual identities through separate accounts.
- Allows users to provide third parties with just enough access to relevant information easily.
- Compatible with various protocols and connectivity requirements for vendors.
SecureLink Cons
- The platform has a learning curve for new users.
- Potential challenges in integrating with certain systems.
- Pricing may be a factor for budget-sensitive organizations.
SecureLink Pricing
SecureLink encourages reaching out to their sales team for a personalized quote.
BeyondTrust Remote Support
BeyondTrust offers different solutions that provide a high level of visibility and security across various environments like computers, servers, cloud services, DevOps, and network devices. Their Privileged Remote Access solution efficiently handles and checks both the internal and external threats and third-party remote special access without needing a VPN. This design ensures that employees can be productive from any location while keeping unauthorized users from accessing critical business systems.
BeyondTrust Top Features
- Privileged Remote Access securely stores passwords in a vault.
- Integration with Password Safe enables secure credential injection.
- Robust monitoring, tracking, and auditing in a single interface with customizable admin alerts.
BeyondTrust Pros
- Efficient access management with secure control.
- Comprehensive visibility across diverse environments.
- Strong monitoring through one interface.
BeyondTrust Cons
- Initial complexity and learning curve for new users.
- Potential integration challenges.
- Cost considerations for budget constraints.
BeyondTrust Pricing
BeyondTrust encourages reaching out to their sales team for a personalized quote.
Conclusion
Privileged Identity Management (PIM) and Privileged Access Management (PAM) are crucial elements in today’s cybersecurity systems. They focus on safeguarding a company’s key assets by overseeing and securing privileged accounts with elevated permissions and access rights can’t be overlooked.
Choosing the right privileged identity management tool can help you add structure to your organization’s information and security.
Frequently Asked Questions (FAQ)
What do you need to do to set up a Privileged Access Management tool?
To successfully deploy a Privileged Access Management tool, two key elements are essential. First, there needs to be a clear understanding of the locations of privileged accounts, coupled with a roadmap outlining how to secure them. Additionally, organizational process changes are necessary to enhance the effectiveness of privileged access controls.
What should organizations focus on when deploying Privileged Access Management?
A key reason for using PAM is to safeguard the business by minimizing the potential areas for cyberattacks. To achieve success in PAM goals, organizations should concentrate on the following practices:
- Keep a record and ensure the security of each privileged account.
- Govern and control access.
- Record and audit privileged activity.
- Operationalize privileged tasks.
How many ways are there to manage privileged access?
Privileged access management solutions are categorized into three types:
- PASM: Actively manages privileged account credentials, changing them at defined intervals or specific events. Also handles privileged credentials for service accounts.
- PEDM: Grants specific privileges to logged-in users on managed systems, providing command control and privilege elevation for servers, along with file integrity monitoring features.
- Secrets Management: Often used in agile environments like IaaS or PaaS, it stores and manages credentials through APIs and SDKs, also supporting application-to-application password management (AAPM).
Original Post URL: https://heimdalsecurity.com/blog/privileged-identity-management-tools/
Category & Tags: Access Management – Access Management
Views: 24





















































