Source: www.darkreading.com – Author: Edge Editors Source: Panther Media GmbH via Alamy Stock Photo Question: What value do public relations experts bring to a company during...
Author: CISO2CISO Editor 2
It’s Near-Unanimous: AI, ML Make the SOC Better – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Only 9% of cybersecurity professionals said that new artificial intelligence (AI) and machine learning (ML) tools have not improved...
Job termination scam warns staff of phony Employment Tribunal decision – Source: www.csoonline.com
Source: www.csoonline.com – Author: Phishing campaign preys on the worries of employees, says expert Creators of phishing messages usually want to create anxiety in their targets...
Finastra investigates breach potentially affecting top global banks – Source: www.csoonline.com
Source: www.csoonline.com – Author: Alleged theft involved 400 GB of customer and internal data presumably containing sensitive financial details. Popular financial software and services provider, Finastra,...
North Korean fake IT workers up the ante in targeting tech firms – Source: www.csoonline.com
Source: www.csoonline.com – Author: North Korean groups are now leveraging deepfake technologies when trying to scam companies into hiring fake IT workers, while adding exfiltration and...
What CISOs need to know about the SEC’s breach disclosure rules – Source: www.csoonline.com
Source: www.csoonline.com – Author: Feature 21 Nov 20247 mins ComplianceCSO and CISOGovernment Security leaders can face personal liability peril for security fails or misleading disclosures to...
Act fast to snuff out employee curiosity over ‘free’ AI apps – Source: www.csoonline.com
Source: www.csoonline.com – Author: Criminals are taking advantage of interest in AI to persuade users to download malware in the guise of useful apps. The word...
CSO30 ASEAN 2024: The top 30 cybersecurity leaders in Southeast Asia and Hong Kong – Source: www.csoonline.com
Source: www.csoonline.com – Author: The fourth CSO30 ASEAN Awards programme recognises the top 30 cybersecurity leaders driving business value, demonstrating leadership, and influencing rapid change across...
N-able Strengthens Cybersecurity via $266M Adlumin Purchase – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Managed Detection & Response (MDR) , Open XDR , Security Operations Security Operations Purchase Brings Cloud-Native XDR, MDR to IT Management Platform...
Feds Seize PopeyeTools Marketplace, Charge Alleged Operators – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cybercrime , Fraud Management & Cybercrime , ID Fraud Justice Department Dismantles Cybercrime Hub, Announces Charges and Seizes Crypto Chris Riotta (@chrisriotta)...
Nightwing CEO on Post-Raytheon Independence, Cyber Expertise – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance Nightwing’s John DeSimone Talks Growth, Threats,...
Coast Guard Warns of Continued Risks in Chinese Port Cranes – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Critical Infrastructure Security Military Says Ship-to-Shore Cranes Made in China Include Dangerous Security Flaws Chris Riotta (@chrisriotta) • November 20, 2024 ...
AI-nt Nothing Gonna Break My Defense: Securing Against Automated Attacks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: The Future of AI & Cybersecurity Presented by Palo Alto Networks x Google Cloud 60 minutes As AI...
Live Webinar | How to Build Cyber Resilience with Proactive Incident Response Strategies – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 3rd Party Risk Management , Governance & Risk Management Presented by ProcessUnity 60 minutes This webinar covers how...
Navigating the Unstructured Data Maze: Your Journey Starts Here – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cloud Data Security & Resilience , Security Operations Presented by Rubrik 60 Minutes Organizations are grappling with massive...
Let’s Give Thanks for How Far We’ve Come – and Forge Ahead! – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Professional Certifications & Continuous Training , Training & Security Leadership Cybersecurity Training and Education Must Evolve to Keep Pace With the Profession...
Respond to Fewer Alerts with Automated Grouping – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pierre Noujeim Isn’t it annoying when multiple alerts are clearly related, but you can’t easily consolidate them into a single incident? This...
How to Motivate Employees and Stakeholders to Encourage a Culture of Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Courtney Chatterton Cybersecurity impacts us all. Third parties process and handle data every day, whether they’re tapping your phone to pay via...
Microsoft Adds Raft of Zero-Trust Tools and Platforms – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Microsoft this week launched a raft of cybersecurity initiatives that address everything from making Windows platforms more secure to adding...
Shift Left and Shift Up Workload Attack Surface Protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Robert Levine Executive Summary: In today’s security landscape, the concept of a hardened perimeter is increasingly insufficient. With the rise of hybrid...
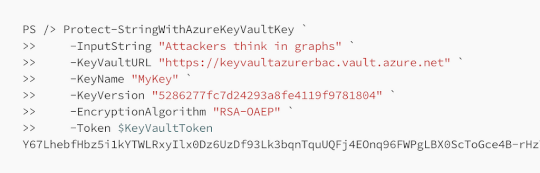
Azure Key Vault Tradecraft with BARK – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Robbins Brief This post details the existing and new functions in BARK that support adversarial tradecraft research relevant to the Azure...
Microsoft Veeps Ignite Fire Under CrowdStrike – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Redmond business leaders line up to say what’s new in Windows security. Microsoft vice presidents David “dwizzzle” Weston (pictured) and Pavan...
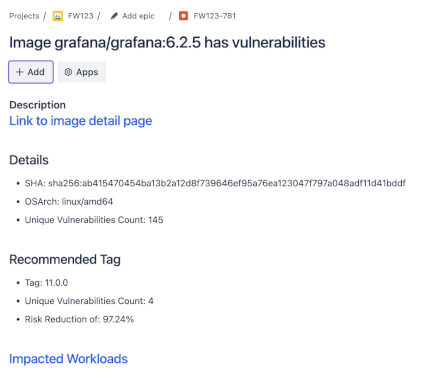
Fairwinds Insights Release Notes 16.1.11 – 16.2.4: CVE Mapping Updates – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dexter Garner Over the last few months, we’ve been working on making a number of meaningful updates to Fairwinds Insights. We’ve delivered...
CISOs Look to Establish Additional Leadership Roles – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy As cybersecurity challenges grow in complexity, chief information security officers (CISOs) are exploring new leadership roles to bolster their teams....
China’s ‘Liminal Panda’ APT Attacks Telcos, Steals Phone Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Jakub Krechowicz via Alamy Stock Photo A newly unveiled threat actor has been spying on mobile phones...
Alleged Ford ‘Breach’ Encompasses Auto Dealer Info – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: imageBROKER.com GmbH & Co. KG via Alamy Stock Photo On Nov. 17, hackers that go by the aliases...
Apple Urgently Patches Actively Exploited Zero-Days – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Shahid Jamil via Alamy Stock Photo Apple has released security updates to address two zero-day vulnerabilities that are...
Small US Cyber Agencies Are Underfunded & That’s a Problem – Source: www.darkreading.com
Source: www.darkreading.com – Author: Michael Daniel Michael Daniel, President & CEO, Cyber Threat Alliance November 20, 2024 5 Min Read Source: Skorzewiak via Alamy Stock Photo...
‘Water Barghest’ Sells Hijacked IoT Devices for Proxy Botnet Misuse – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Jiraroj Praditcharoenkul via Alamy Stock Photo A cybercriminal group is exploiting vulnerabilities in Internet of Things (IoT)...
African Reliance on Foreign Suppliers Boosts Insecurity Concerns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: CG Alex via Shutterstock Every night for five years, computers and network appliances from the headquarters of...