Source: news.sophos.com – Author: Angela Gunn
Microsoft on Tuesday released 71 patches touching 10 product families. Seventeen of the addressed issues, all affecting Windows, are considered by Microsoft to be of Critical severity and all have a CVSS base score of 8.1 or higher. Ten of these involve Remote Desktop Services. At patch time, one of the issues addressed (CVE-2024-49138, an Important-severity Windows Common Log File system driver issue) is known to be under exploit in the wild, with 6 additional CVEs more likely to be exploited in the next 30 days by the company’s estimation. Five of this month’s issues are amenable to detection by Sophos protections, and we include information on those in a table below.
In addition to these patches, the release includes advisory information on two Edge CVEs (patched last week), a Defense-in-Depth update for a specific version of Microsoft Project, and information on six bulletins released by Adobe this week. We are as always including at the end of this post additional appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family.
Finally, this month we are adding a new appendix that breaks out each month’s Windows Server patches by affected version. Administrators are encouraged to use this appendix as a starting point to ascertain their specific exposure, as each reader’s situation — especially as it concerns products out of mainstream support — will vary.
- Total CVEs: 71
- Publicly disclosed: 1
- Exploit detected: 1
- Severity
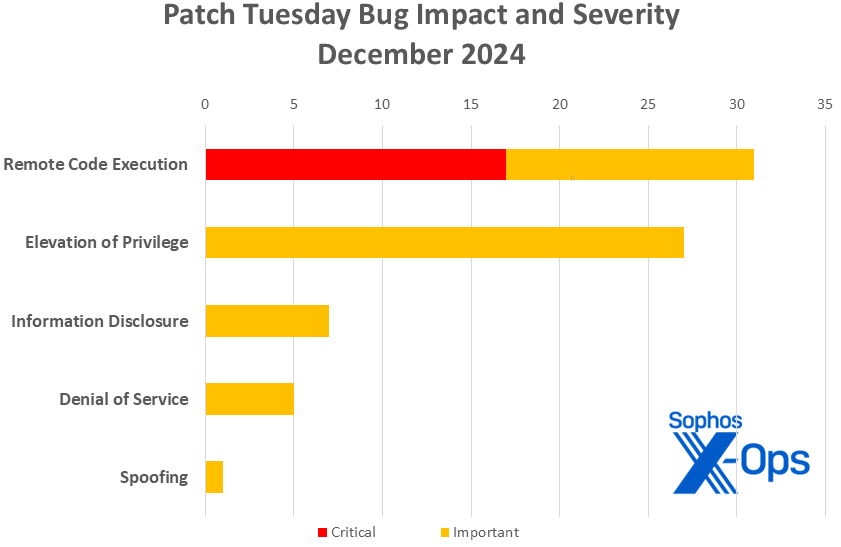
- Critical: 17
- Important: 54
- Impact
- Remote Code Execution: 31
- Elevation of Privilege: 27
- Information Disclosure: 7
- Denial of Service: 5
- Spoofing: 1
- CVSS base score 9.0 or greater: 1
- CVSS score 8.0 or greater: 27
Figure 1: December’s CVEs include no spoofing, denial of service, or security feature bypass issues, but there are plenty of Critical-severity RCEs to keep system administrators busy
Products
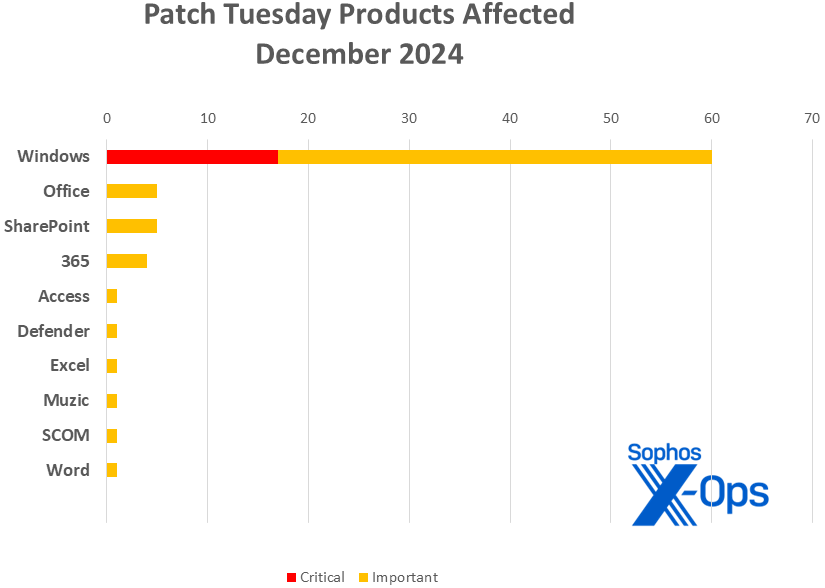
- Windows: 59
- Office: 5
- SharePoint: 5
- 365 Apps: 4
- Access: 1
- Defender: 1
- Excel: 1
- Muzic: 1
- SCOM: 1
- Word: 1
As is our custom for this list, CVEs that apply to more than one product family are counted once for each family they affect.
Figure 2: Six of the ten product families covered in this month’s updates have just one patch apiece. Muzic is a music-generation project on Github (https://github.com/microsoft/muzic) originally developed by a team from Microsoft Research Asia
Notable December updates
In addition to the issues discussed above, a number of specific items merit attention.
CVE-2024-49112 — Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
The only CVE this month with a CVSS base score over 9.0, this Critical-severity RCE weighs in at 9.8/10 and affects not only all supported versions of Windows 10 and 11, but all versions of Server stretching back to 2008. Complexity is low (it requires a maliciously crafted set of LDAP calls), it requires neither privileges nor user interaction, and the attacker able to successfully exploit the bug gains the ability to execute arbitrary code within the context of the LDAP service. For administrators unable to prioritize this patch for whatever reason, Microsoft advises them to ensure that domain controllers are not configured to access the internet, and that inbound RPC from untrusted networks is disallowed.
CVE-2024-49138 — Windows Common Log File System Driver Elevation of Privilege Vulnerability
The only December CVE that’s known to be under active exploit in the wild, this Important-severity elevation of privilege issue likewise affects all supported client and server versions of Windows. A successful attacker would gain system privileges.
CVE-2024-49117 – Windows Hyper-V Remote Code Execution Vulnerability
An attacker successfully utilizing this Critical-severity RCE could potentially execute a cross-VM attack, leaping out of the originally compromised machine to compromise others.
CVE-2024-49114 — Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
This Important-severity issue is a fascinating example of what just might be a new category of vulnerability: False File Immutability, in which certain assumptions built into certain Windows componentry could lead to untrustworthy files, bad system behaviors, or other vulnerabilities. Nevertheless, Microsoft categorizes this CVE as an Elevation of Privilege issue, one more likely to be exploited within the next 30 days.
12 CVEs – RDP issues
As covered in our Active Adversary technical reports, RDP continues to be the Microsoft component most often abused by attackers. Both client-side and server-side installations are in for it this month, with 10 of these CVEs classed as Critical-severity by Microsoft.
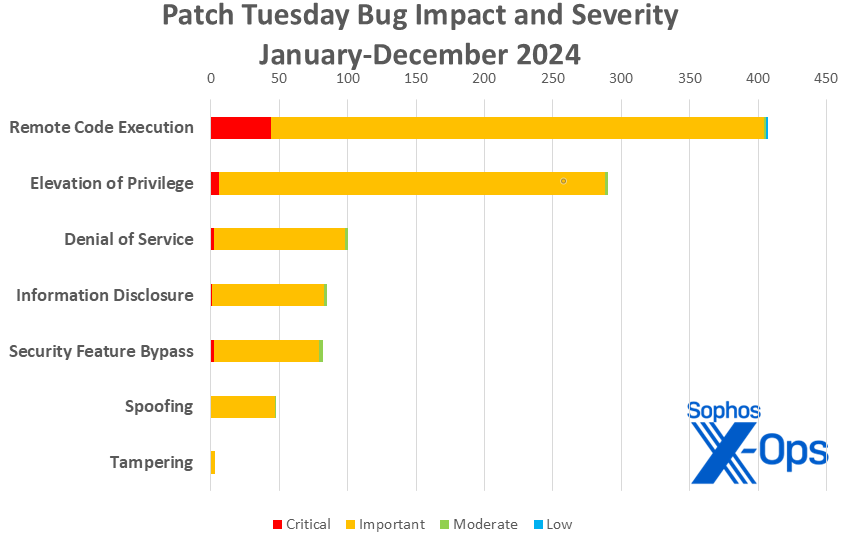
Figure 3: And as 2024 concludes, Remote Code Execution vulnerabilities retain their standing as the most common bug species to be squashed, retaining the title seized from Elevation of Privilege at the end of 2023
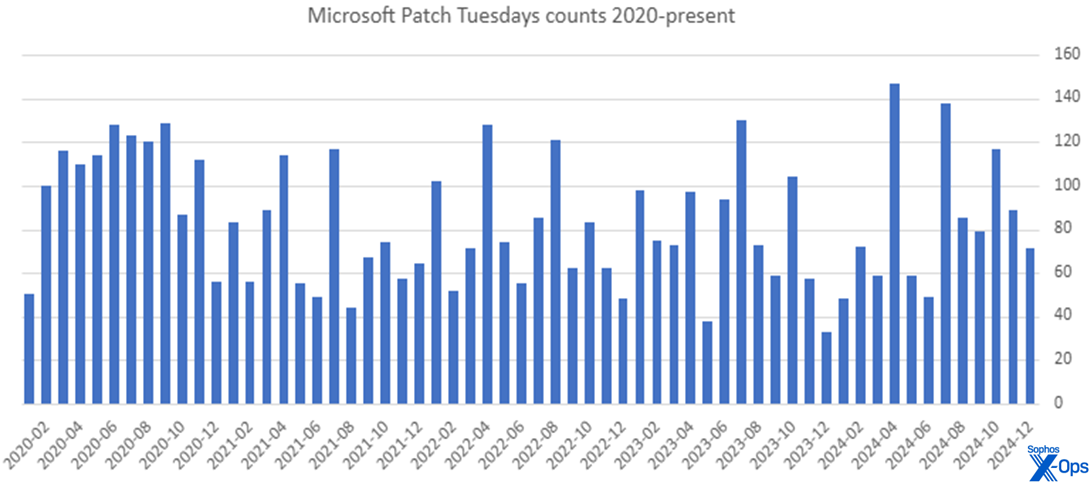
Though it started off with three relatively light months, 2024 ends with 1015 CVEs addressed through the Patch Tuesday process – the highest annual count since 2020’s total of 1245 patches. 2024 also included the two single highest one-month patch counts, in April (147) and July (138). For those curious, December 2023 had the lowest count of the past five years, with 33 patches.
Figure 4: If it felt like 2020 was a crazy year for Microsoft patches, you’re not wrong. Though 2024 had several banner months, 2020 was overall the heaviest patch load in four years for most administrators
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-49088 | Exp/2449088-A | Exp/2449088-A |
| CVE-2024-49090 | Exp/2449090-A | Exp/2449090-A |
| CVE-2024-49093 | Exp/2449093-A | Exp/2449093-A |
| CVE-2024-49122 | sid:2310400 | sid:2310400 |
| CVE-2024-49138 | Exp/2449138-A | Exp/2449138-A |
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of December patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Remote Code Execution (31 CVEs)
| Critical severity | |
| CVE-2024-49105 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2024-49106 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49108 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49112 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2024-49115 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49116 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49117 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-49118 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-49119 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49120 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49122 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-49123 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49124 | Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Vulnerability |
| CVE-2024-49126 | Windows Local Security Authority Subsystem Service (LSASS) Remote Code Execution Vulnerability |
| CVE-2024-49127 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2024-49128 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49132 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-49063 | Microsoft/Muzic Remote Code Execution Vulnerability |
| CVE-2024-49065 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-49069 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49070 | Microsoft SharePoint Remote Code Execution Vulnerability |
| CVE-2024-49079 | Input Method Editor (IME) Remote Code Execution Vulnerability |
| CVE-2024-49080 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-49085 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49086 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49089 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49091 | Windows Domain Name Service Remote Code Execution Vulnerability |
| CVE-2024-49102 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49104 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49125 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49142 | Microsoft Access Remote Code Execution Vulnerability |
| CVE-2024-49063 | Microsoft/Muzic Remote Code Execution Vulnerability |
| CVE-2024-49065 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-49069 | Microsoft Excel Remote Code Execution Vulnerability |
Elevation of Privilege (27 CVEs)
| Important severity | |
| CVE-2024-43594 | System Center Operations Manager Elevation of Privilege Vulnerability |
| CVE-2024-43600 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2024-49059 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2024-49068 | Microsoft SharePoint Elevation of Privilege Vulnerability |
| CVE-2024-49072 | Windows Task Scheduler Elevation of Privilege Vulnerability |
| CVE-2024-49073 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49074 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-49076 | Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability |
| CVE-2024-49077 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49078 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49081 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49083 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49084 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-49088 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49090 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49092 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49093 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-49094 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49095 | Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability |
| CVE-2024-49097 | Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability |
| CVE-2024-49101 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49107 | WmsRepair Service Elevation of Privilege Vulnerability |
| CVE-2024-49109 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49110 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49111 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49114 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-49138 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
Information Disclosure (7 CVEs)
| Important severity | |
| CVE-2024-49062 | Microsoft SharePoint Information Disclosure Vulnerability |
| CVE-2024-49064 | Microsoft SharePoint Information Disclosure Vulnerability |
| CVE-2024-49082 | Windows File Explorer Information Disclosure Vulnerability |
| CVE-2024-49087 | Windows Mobile Broadband Driver Information Disclosure Vulnerability |
| CVE-2024-49098 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
| CVE-2024-49099 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
| CVE-2024-49103 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
Denial of Service (5 CVEs)
| Important severity | |
| CVE-2024-49075 | Windows Remote Desktop Services Denial of Service Vulnerability |
| CVE-2024-49096 | Microsoft Message Queuing (MSMQ) Denial of Service Vulnerability |
| CVE-2024-49113 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2024-49121 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2024-49129 | Windows Remote Desktop Gateway (RD Gateway) Denial of Service Vulnerability |
Spoofing (1 CVE)
| Important severity | |
| CVE-2024-49057 | Microsoft Defender for Endpoint on Android Spoofing Vulnerability |
Appendix B: Exploitability
This is a list of the December CVEs judged by Microsoft to be either under exploitation in the wild or more likely to be exploited in the wild within the first 30 days post-release. The list is arranged by CVE.
| Exploitation detected | |
| CVE-2024-49138 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| Exploitation more likely within the next 30 days | |
| CVE-2024-49070 | Microsoft SharePoint Remote Code Execution Vulnerability |
| CVE-2024-49088 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49090 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49093 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-49114 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-49122 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
Appendix C: Products Affected
This is a list of December’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family. Issues affecting Windows Server are further sorted in Appendix E.
Windows (59 CVEs)
| Critical severity | |
| CVE-2024-49105 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2024-49106 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49108 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49112 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2024-49115 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49116 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49117 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-49118 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-49119 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49120 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49122 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-49123 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49124 | Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Vulnerability |
| CVE-2024-49126 | Windows Local Security Authority Subsystem Service (LSASS) Remote Code Execution Vulnerability |
| CVE-2024-49127 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2024-49128 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2024-49132 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-49072 | Windows Task Scheduler Elevation of Privilege Vulnerability |
| CVE-2024-49073 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49074 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-49075 | Windows Remote Desktop Services Denial of Service Vulnerability |
| CVE-2024-49076 | Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability |
| CVE-2024-49077 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49078 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49079 | Input Method Editor (IME) Remote Code Execution Vulnerability |
| CVE-2024-49080 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-49081 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49082 | Windows File Explorer Information Disclosure Vulnerability |
| CVE-2024-49083 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49084 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-49085 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49086 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49087 | Windows Mobile Broadband Driver Information Disclosure Vulnerability |
| CVE-2024-49088 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49089 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49090 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49091 | Windows Domain Name Service Remote Code Execution Vulnerability |
| CVE-2024-49092 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49093 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-49094 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49095 | Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability |
| CVE-2024-49096 | Microsoft Message Queuing (MSMQ) Denial of Service Vulnerability |
| CVE-2024-49097 | Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability |
| CVE-2024-49098 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
| CVE-2024-49099 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
| CVE-2024-49101 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49102 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49103 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
| CVE-2024-49104 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49107 | WmsRepair Service Elevation of Privilege Vulnerability |
| CVE-2024-49109 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49110 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49111 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49113 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2024-49114 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-49121 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2024-49125 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-49129 | Windows Remote Desktop Gateway (RD Gateway) Denial of Service Vulnerability |
| CVE-2024-49138 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
Office (5 CVEs)
| Important severity | |
| CVE-2024-43600 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2024-49059 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2024-49065 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-49069 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49142 | Microsoft Access Remote Code Execution Vulnerability |
SharePoint (5 CVEs)
| Important severity | |
| CVE-2024-49062 | Microsoft SharePoint Information Disclosure Vulnerability |
| CVE-2024-49064 | Microsoft SharePoint Information Disclosure Vulnerability |
| CVE-2024-49065 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-49068 | Microsoft SharePoint Elevation of Privilege Vulnerability |
| CVE-2024-49070 | Microsoft SharePoint Remote Code Execution Vulnerability |
365 (4 CVEs)
| Important severity | |
| CVE-2024-49059 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2024-49065 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-49069 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49142 | Microsoft Access Remote Code Execution Vulnerability |
Access (1 CVE)
| Important severity | |
| CVE-2024-49142 | Microsoft Access Remote Code Execution Vulnerability |
Defender (1 CVE)
| Important severity | |
| CVE-2024-49057 | Microsoft Defender for Endpoint on Android Spoofing Vulnerability |
Excel (1 CVE)
| Important severity | |
| CVE-2024-49069 | Microsoft Excel Remote Code Execution Vulnerability |
Muzic (1 CVE)
| Important severity | |
| CVE-2024-49063 | Microsoft/Muzic Remote Code Execution Vulnerability |
SCOM (1 CVE)
| Important severity | |
| CVE-2024-43594 | System Center Operations Manager Elevation of Privilege Vulnerability |
Word (1 CVE)
| Important severity | |
| CVE-2024-49065 | Microsoft Office Remote Code Execution Vulnerability |
Appendix D: Advisories and Other Products
This is a list of advisories and information on other relevant CVEs in the December release.
Microsoft information:
| CVE / identifier | Product | Title |
| ADV240002 | Project 2016 | Microsoft Office Defense in Depth Update |
| CVE-2024-12053 | Edge | Chromium: CVE-2024-12053 Type Confusion in V8 |
| CVE-2024-49041 | Edge | Microsoft Edge (Chromium-based) Spoofing Vulnerability |
Adobe Reader advisories:
| CVE | Bulletin | Title |
| CVE-2024-49531 | APSB24-92 | NULL Pointer Dereference (CWE-476) |
| CVE-2024-49530 | APSB24-92 | Use After Free (CWE-416) |
| CVE-2024-49532 | APSB24-92 | Out-of-bounds Read (CWE-125) |
| CVE-2024-49533 | APSB24-92 | Out-of-bounds Read (CWE-125) |
| CVE-2024-49534 | APSB24-92 | Out-of-bounds Read (CWE-125) |
| CVE-2024-49535 | APSB24-92 | Improper Restriction of XML External Entity Reference (‘XXE’) (CWE-611) |
Appendix E: Affected Windows Server versions
This is a table of CVEs in the December release affecting nine Windows Server versions — 2008 through 2025. The table differentiates among major versions of the platform but doesn’t go into deeper detail (eg., Server Core). Critical-severity issues are marked in red; an “x” indicates that the CVE does not apply to that version. Administrators are encouraged to use this appendix as a starting point to ascertain their specific exposure as each reader’s situation, especially as it concerns products out of mainstream support, will vary.
| 2008 | 2008-R2 | 2012 | 2012-R2 | 2016 | 2019 | 2022 | 2022 23H2 | 2025 | |
| CVE-2024-49072 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49073 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49074 | × | × | × | × | × | ■ | × | × | × |
| CVE-2024-49075 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49076 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49077 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49078 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49079 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49080 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49081 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49082 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49083 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49084 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49085 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49086 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49087 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49088 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49089 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49090 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49091 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49092 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49093 | × | × | × | × | × | × | × | × | ■ |
| CVE-2024-49094 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49095 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49096 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49097 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49098 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49099 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49101 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49102 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49103 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49104 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49105 | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49106 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49107 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49108 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49109 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49110 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49111 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49112 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49113 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49114 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49115 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49116 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49117 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2024-49118 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49119 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49120 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49121 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49122 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49123 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49124 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49125 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49126 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49127 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49128 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49129 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49132 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49138 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
Original Post URL: https://news.sophos.com/en-us/2024/12/11/december-patch-tuesday-arrives-bearing-71-gifts/
Category & Tags: Threat Research,featured,Microsoft,Patch Tuesday,RDP,Windows – Threat Research,featured,Microsoft,Patch Tuesday,RDP,Windows
Views: 0