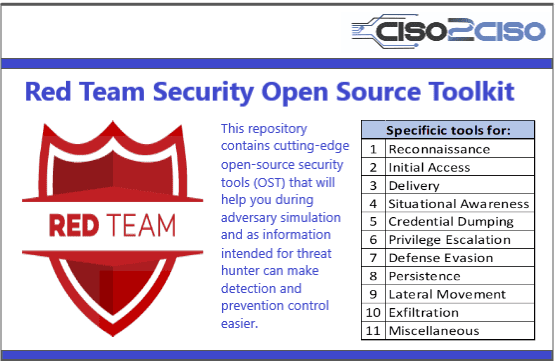
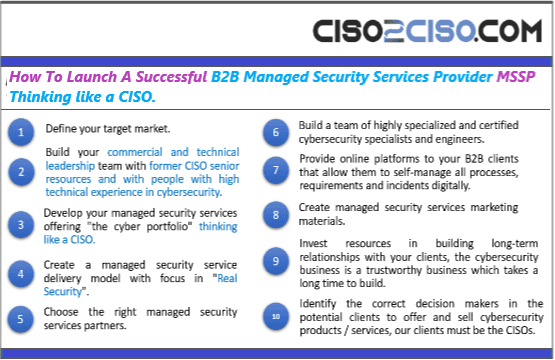
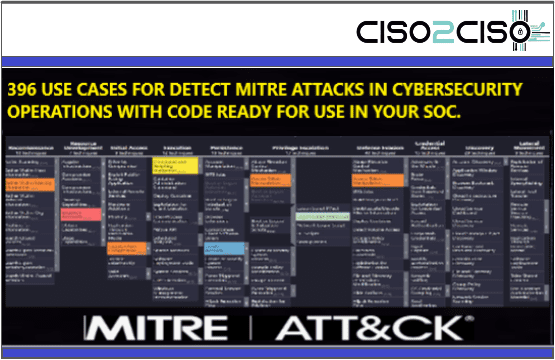
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
LATEST CYBER NEWS
- 03 / 30 : 4:03 am : RESURGE Malware Exploits Ivanti Flaw with Rootkit and Web Shell Features – Source:thehackernews.com
- 03 / 30 : 3:03 am : FBI and DOJ seize $8.2 Million in romance baiting crypto fraud scheme – Source: securityaffairs.com
- 03 / 30 : 3:03 am : Experts warn of the new sophisticate Crocodilus mobile banking Trojan – Source: securityaffairs.com
- 03 / 30 : 2:03 am : What are the cost implications of maintaining NHI compliance? – Source: securityboulevard.com
- 03 / 30 : 2:03 am : What best practices ensure long-term compliance for NHIs? – Source: securityboulevard.com
- 03 / 30 : 2:03 am : How can technology simplify the process of NHI compliance? – Source: securityboulevard.com
- 03 / 30 : 2:03 am : BSidesLV24 – IATC – Time Is Up. You Have Three Years, 3 Months, 3 Weeks, To Protect Your Stuff. What Do You Do? – Source: securityboulevard.com
- 03 / 30 : 2:03 am : Babuk Locker 2.0 vs Seceon Platform: MITRE ATT&CK Mapping and Early-Stage Detection & Remediation – Source: securityboulevard.com
- 03 / 30 : 2:03 am : News alert: SquareX discloses nasty browser-native ransomware that’s undetectable by antivirus – Source: securityboulevard.com
- 03 / 30 : 2:03 am : Executive Perspectives: Pierre Noel on Cybersecurity Leadership, Risk, and Resilience – Source: securityboulevard.com
- 03 / 30 : 2:03 am : Building Smarter, Safer Businesses: How SecureFLO is Bridging AI Innovation with Cybersecurity – Source: securityboulevard.com
- 03 / 30 : 1:04 am : Twitter (X) Hit by 2.8 Billion Profile Data Leak in Alleged Insider Job – Source:hackread.com
- 03 / 29 : 4:03 pm : New Android Trojan Crocodilus Abuses Accessibility to Steal Banking and Crypto Credentials – Source:thehackernews.com
- 03 / 29 : 4:02 pm : New Security Flaws Found in VMware Tools and CrushFTP — High Risk, PoC Released – Source:thehackernews.com
- 03 / 29 : 3:03 pm : Malware in Lisp? Now you’re just being cruel – Source: go.theregister.com
- 03 / 29 : 12:04 pm : Birthday freebies: how to cash in on UK retailers’ gifts and discounts – Source: www.theguardian.com
- 03 / 29 : 11:05 am : SquareX Discloses Browser-Native Ransomware that Puts Millions at Risk – Source:hackread.com
- 03 / 29 : 6:03 am : Critical Condition: Legacy Medical Devices Remain Easy Targets for Ransomware – Source: www.securityweek.com
- 03 / 29 : 6:03 am : 9-Year-Old NPM Crypto Package Hijacked for Information Theft – Source: www.securityweek.com
- 03 / 29 : 6:03 am : In Other News: Hellcat Hackers Unmasked, CrushFTP Bug Controversy, NYU Hacked – Source: www.securityweek.com
- 03 / 29 : 6:03 am : New Issuance Requirements Improve HTTPS Certificate Validation – Source: www.securityweek.com
- 03 / 29 : 6:03 am : Morphing Meerkat Phishing Kits Target Over 100 Brands – Source: www.securityweek.com
- 03 / 29 : 6:03 am : Fresh Grandoreiro Banking Trojan Campaigns Target Latin America, Europe – Source: www.securityweek.com
- 03 / 29 : 6:03 am : Firefox Affected by Flaw Similar to Chrome Zero-Day Exploited in Russia – Source: www.securityweek.com
- 03 / 29 : 4:03 am : Evilginx Tool (Still) Bypasses MFA – Source: www.darkreading.com
- 03 / 29 : 4:03 am : Oracle Still Denies Breach as Researchers Persist – Source: www.darkreading.com
- 03 / 29 : 4:03 am : Harmonic Security Raises $17.5M Series A to Accelerate Zero-Touch Data Protection to Market – Source: www.darkreading.com
- 03 / 29 : 4:03 am : Traditional Data Loss Prevention Solutions Are Not Working for Most Organizations – Source: www.darkreading.com
- 03 / 29 : 4:03 am : SecurityScorecard 2025 Global Third-Party Breach Report Reveals Surge in Vendor-Driven Attacks – Source: www.darkreading.com
- 03 / 29 : 4:03 am : Malaysia PM Refuses to Pay $10M Ransomware Demand – Source: www.darkreading.com
- 03 / 29 : 4:03 am : Concord Orthopaedic Notifies Individuals of Security Incident – Source: www.darkreading.com
- 03 / 29 : 4:03 am : Navigating Cyber-Risks and New Defenses – Source: www.darkreading.com
- 03 / 29 : 4:03 am : Student-Powered SOCs Train Security’s Next Generation – Source: www.darkreading.com
- 03 / 29 : 4:03 am : BlackLock Ransomware Exposed After Researchers Exploit Leak Site Vulnerability – Source:thehackernews.com
- 03 / 29 : 4:03 am : Windows 10 End-of-Life Puts SMBs at Risk – Source: www.darkreading.com
- 03 / 29 : 2:03 am : Crooks are reviving the Grandoreiro banking trojan – Source: securityaffairs.com
- 03 / 29 : 2:03 am : Russian authorities arrest three suspects behind Mamont Android banking trojan – Source: securityaffairs.com
- 03 / 29 : 2:03 am : Mozilla fixed critical Firefox vulnerability CVE-2025-2857 – Source: securityaffairs.com
- 03 / 29 : 2:03 am : PCI DSS 4.0: Achieve Compliance with Feroot Before March 31 – Source: securityboulevard.com
- 03 / 29 : 2:03 am : Cybersecurity & Infrastructure Security Agency (CISA) Pledge – Source: securityboulevard.com
CISO Strategics

SOC OPERATIONS

THREAT INTELLIGENCE

vulnerabilities

cyber attacks

RansoNWARE

DDOS ATTACKS

DDOS ATTACKS

RED - BLUE & PURPLE

DATA BREACH

DATA PRIVACY
CLOUD SECURITY

IOT - OT SECURITY

RISK & COMPLIANCE

DEVSECOPS

DEVSECOPS

CISO2CISO Advisors recomended posts
Latest Published Posts
CYBER ARCHITECTURE
- API Security
- Application Security
- Blockchain Security
- Cloud Security
- Data Security
- Defense in Depth
- DevSecOps
- Endpoint Security
- IA Security
CYBERSECURITY TOOLS
CYBERSECURITY VENDORS
CYBERSECURITY MSSP
- Accenture
- Attos
- AT&T Cybersecurity
- BT Security
- BASE 4 - Hispam
- Deloitte
- Entelgy Security
- KPMG
- NTT Security
CISO2CISO STRATEGIC VALLEY
CISO2CISO SOC OPERATIONS VALLEY
LATEST CYBER NEWS
Latest Published Posts
CISO STRATEGICS
CYBER ARCHITECTURE
- IOT Security
- MAC-OS Security
- Metaverse Security
- Mitre Att&ck
- Mobile & 5G Security
- Network Security
- NIST Security
- OT Security
- OWASP Security
- Perimeter Security
- SAP Security
- Telco & Carrier Security
- Zero Trust Security
CYBERSECURITY TOOLS
CYBERSECURITY VENDORS
- Fortinet
- Guardicore
- IBM
- Mcafee - Trellix
- Mandiant
- Microsoft
- Netscope
- Palo Alto Networks
- RSA Security
- Redhat
- Splunk
- Symantec
- Tenable
- Trendmicro
CYBERSECURITY MSSP
- NTT Security
- Novared - Hispam
- Neosecure - Hispam
- Orange Cyberdefense
- PwC
- Telefonica Tech
- Thales
- Verizon Security
CYBER REGULATIONS
USERS MOST VOTED POST
LATEST CYBER NEWS
Latest Published Posts
LATEST CYBER NEWS
Latest Published Posts
Views: 16650